网鼎杯青龙组部分RE WP
[网鼎杯 2020 青龙组]jocker
1 | |
获得
flag{fak3_alw35_sp_me!!}
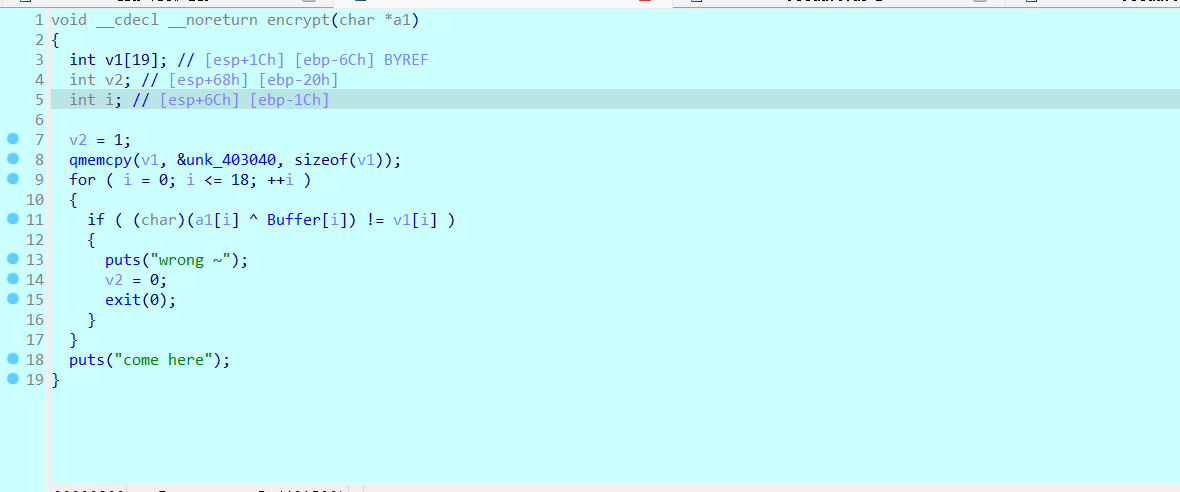
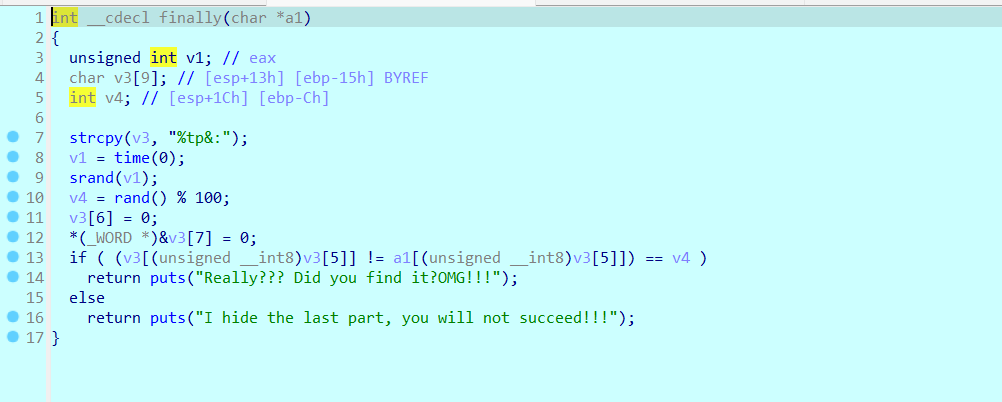
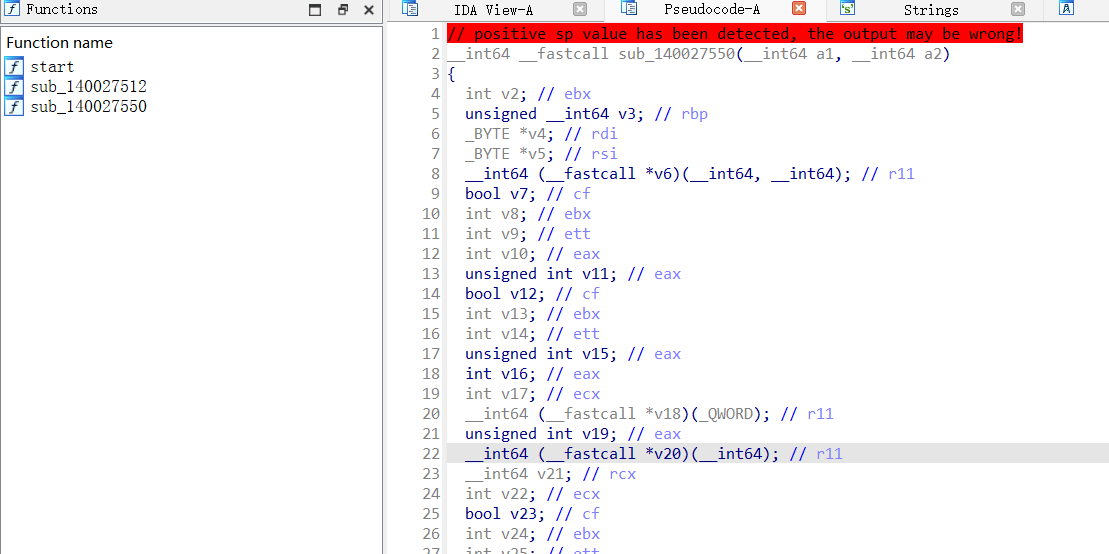
之前的步骤需要处理一下IDA识别里面的堆栈不平衡的问题
其实不解决这个问题也能做,但是遇到了就学下吧
来源:
IDA为什么产生 sp-analysis failed 错误?-CSDN博客
总结一下:
1、确定本函数的栈大小、传入参数数量、是否保存寄存器,对本函数做响应修改
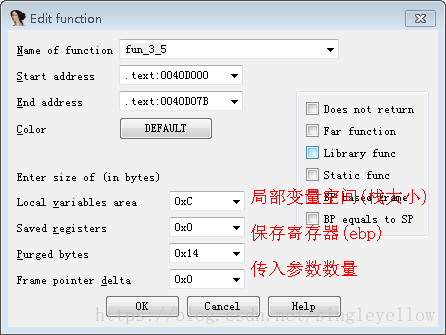
2、在本函数内部分析每一行的栈指针,看ida有没识别错误的,如果有识别错误的通过Alt+K修改过来
这个地方还要注意一下最开始得到假flag的时候提取数据的时候没有去注意具体的数据的类型
[网鼎杯 2020 青龙组]singal
1 | |
运行得到结果:
1 | |
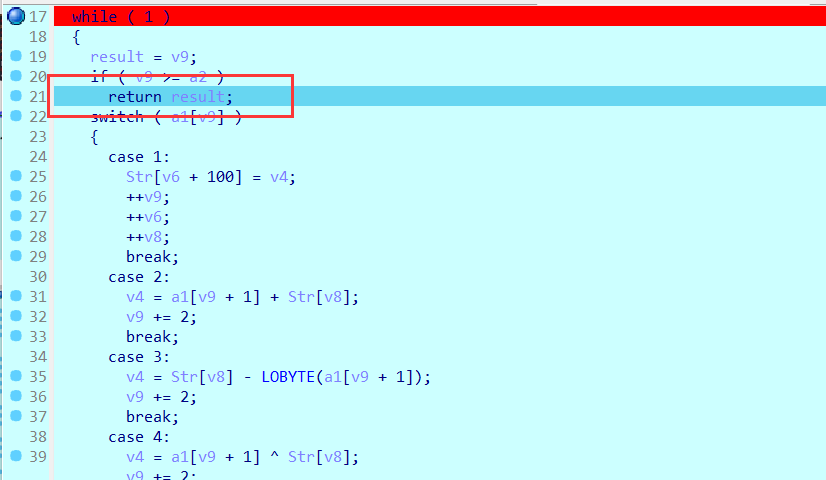
只有case7处是在直接比较输入的数据和最后已知的opcode的指令(opcode[i+1])
那么就是取opcode指令里面的是7的下一个数据
下面得到的[34,63,52,50,114,51,24,167,49,241,40,132,193,30,122]数据则为输入正确的flag以后经过处理最后得到的数据
然后再根据最后每一位得到的input挨个推出就行
也可以选择angr一把梭
1 | |
详情
[BUUCTF-网鼎杯 2020 青龙组]singal——angr学习记录_退出angr环境-CSDN博客
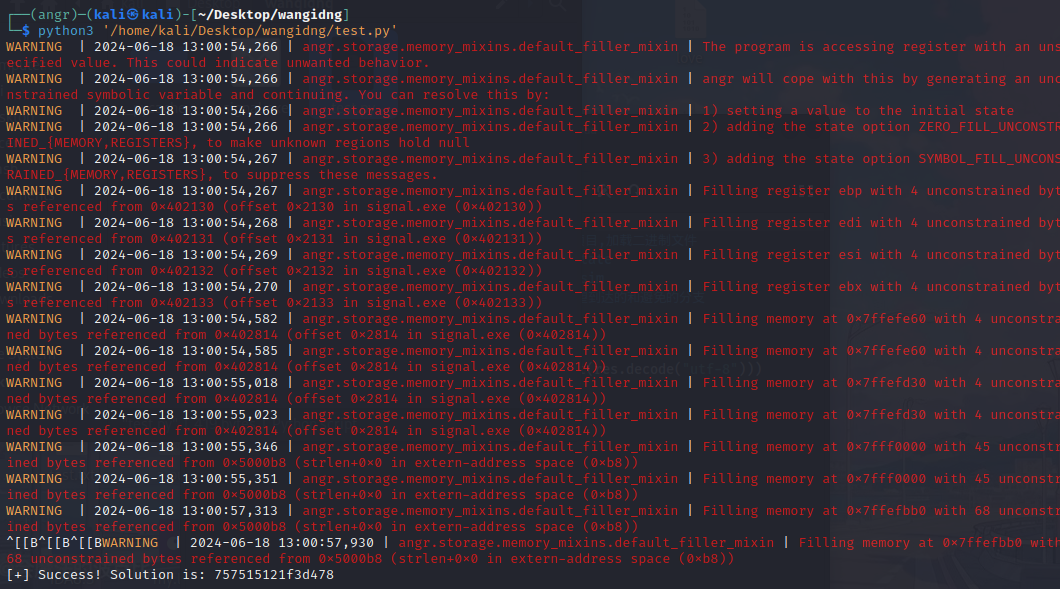
注意angr脚本中的地址
此处判断循环结束,故find地址为0x40175e,避免出现what a shame…,故avoid地址为0x4016e6
[网鼎杯 2022 青龙组]fakeshell
UPX防脱壳机脱壳、去除特征码、添加花指令小探 - 『脱壳破解区』 - 吾爱破解 - LCG - LSG |安卓破解|病毒分析|www.52pojie.cn
UPX壳的修改 - Clovershrub - 博客园 (cnblogs.com)
里面有的upx标志位写的是FUK0和FUK1,分别修改为UPX0和UPX1,55 50 58 30,55 50 58 31
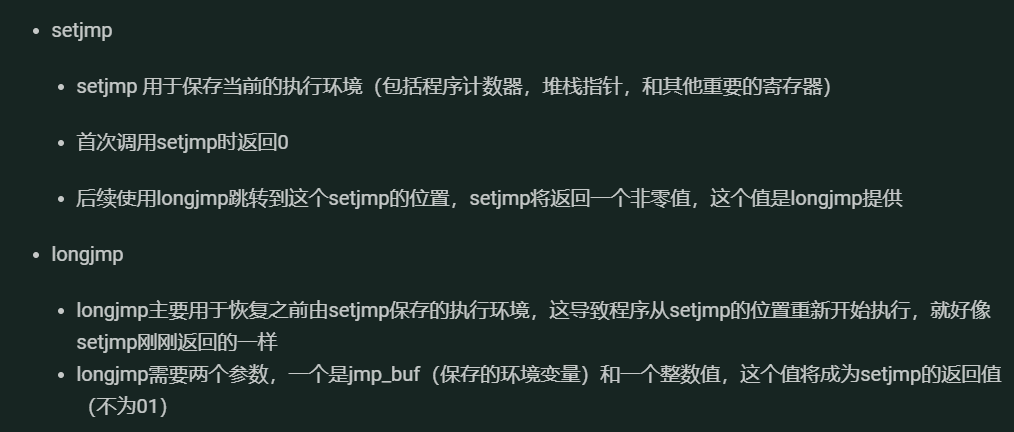
【C/C++ 跳转函数】setjmp 和 longjmp 函数的巧妙运用: C 语言错误处理实践-CSDN博客
j___intrinsic_setjmp
1 | |
使用事例:
1 | |
exp:
1 | |
[2022网鼎杯青龙组部分wp–re两题(challenge,Fakeshell)_2022网鼎杯青龙组]fakeshell题目下载-CSDN博客
网鼎杯2022 青龙组 Fakeshell | Fight for the good in your heart. (mykonos-x.github.io)
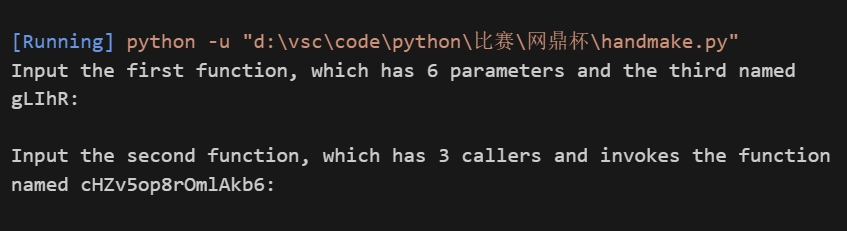
[网鼎杯 2022 青龙组]Handmake
1 | |
得到提示
1 | |
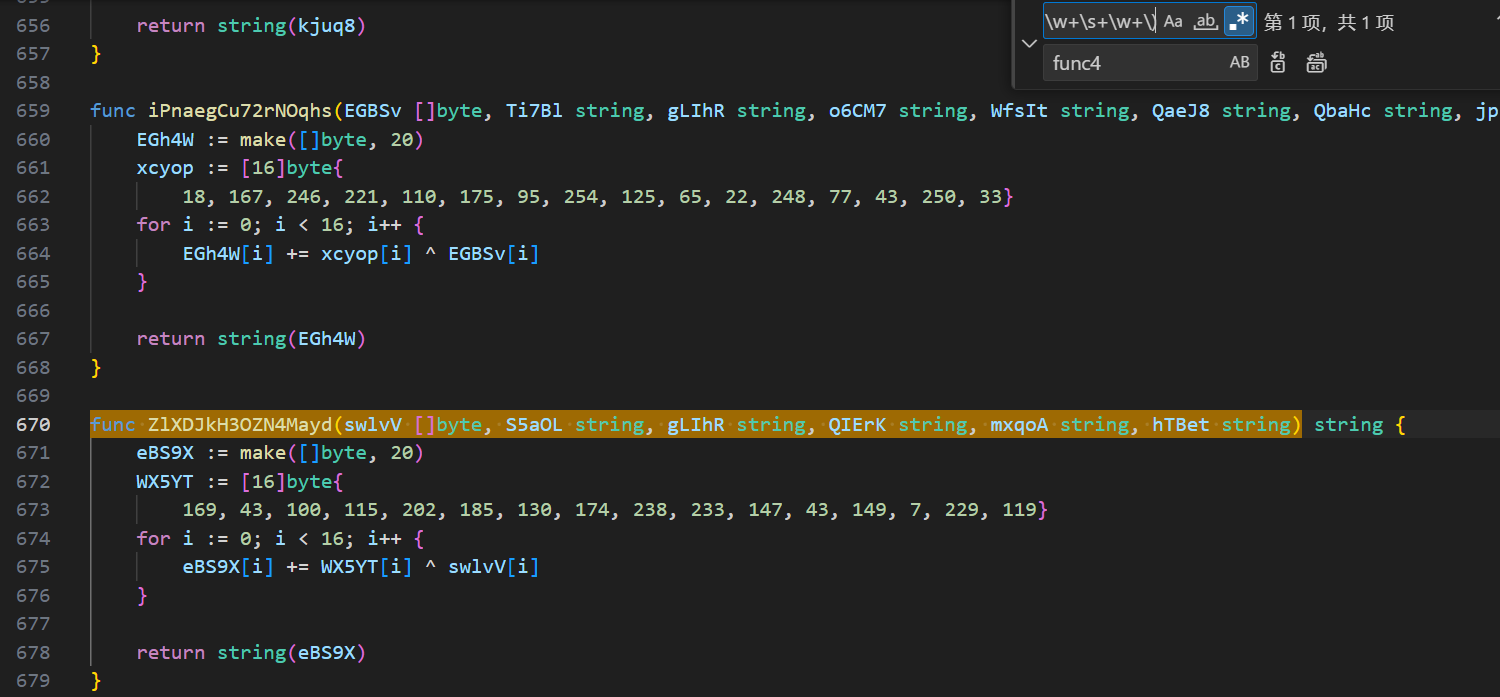
针对提示要找的第一个函数有6个参数第三个参数是“gLIhR”,可以使用正则表达式
1 | |
\w代表一个单词字符,匹配以下字符:
- 所有大小写字母(A-Z,a-z)
- 所有数字(0-9)
- 下划线(_)
\s代表空白字符,匹配以下字符:
- 空格
- 制表符
- 换行符
- 回车符
- 垂直制表符
- 换页符
参考:网鼎杯2022 青龙组 Handmake | Fight for the good in your heart. (mykonos-x.github.io)
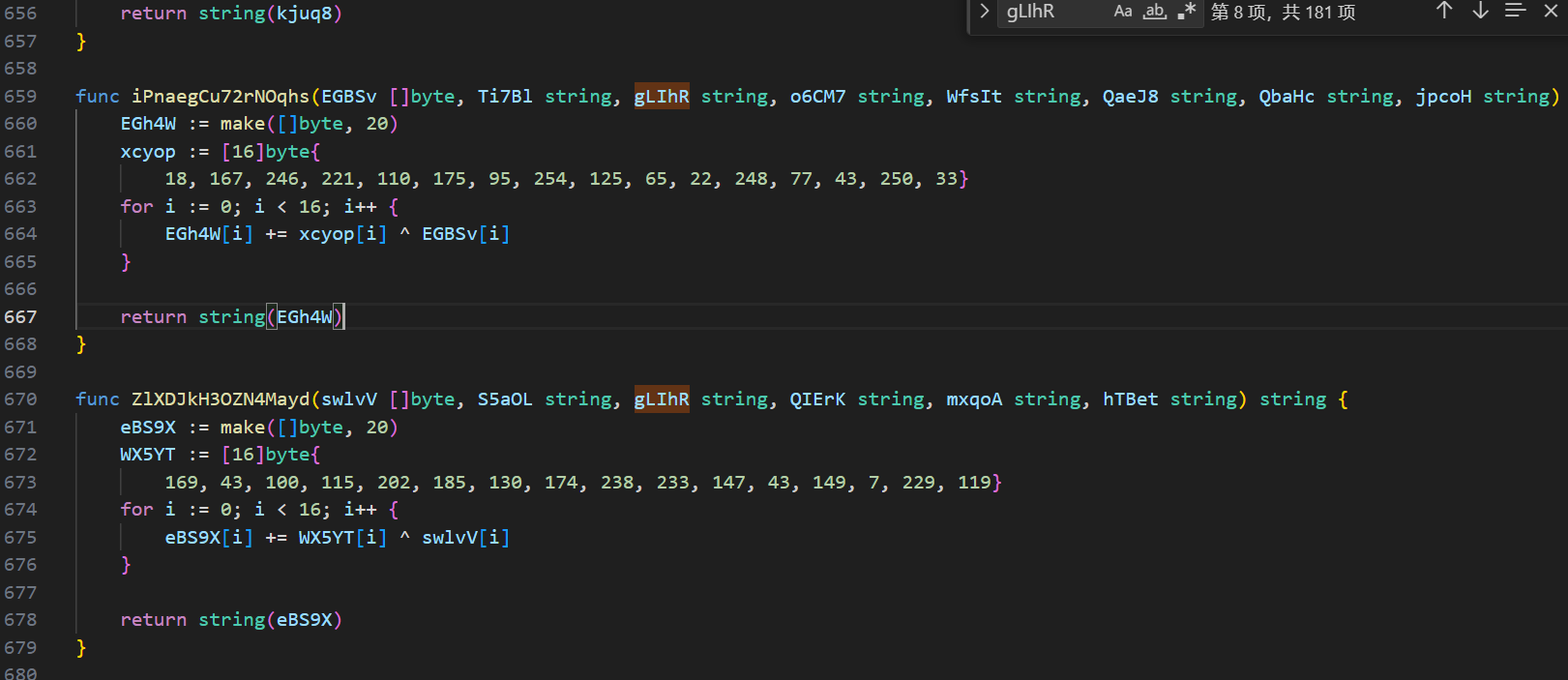
第一个函数:ZlXDJkH3OZN4Mayd
1 | |
1 | |
1 | |
第二个函数:UhnCm82SDGE0zLYO
1 | |
1 | |
最后异或得到结果
1 | |
1 | |
flag{3a4e76449355c4148ce3da2b46019f75}
网上查看别人的wp发现其实可以通过直接对go文件进行编译,或者直接运行,就可以在终端直接获得上述提示输出,然后直接找到对应的函数进行输入就可以得到正确的flag
(这里要注意一个细节,源码里面的scanf中间没有fmt.Scanln(),如果直接输入第一个函数回车然后输入第二个函数的时候会把回车当成第二个输入然后直接退出程序运行)