考核题目复现
暑期考核题目wp
【2024春节】解题领红包之Android中级题
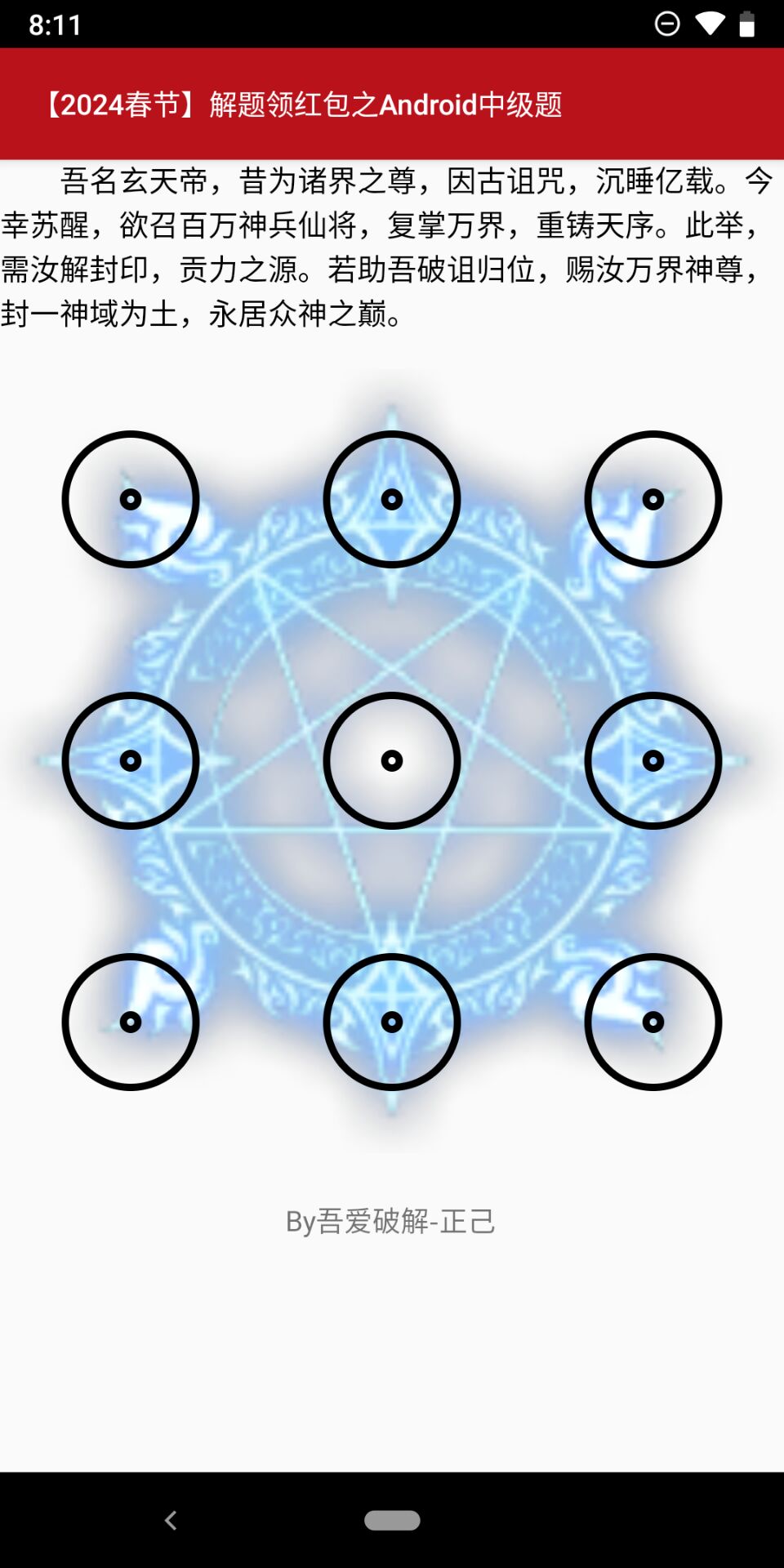
使用真机下载后查看apk,发现是一个解锁,随便尝试连接一下,发现没有回显提示
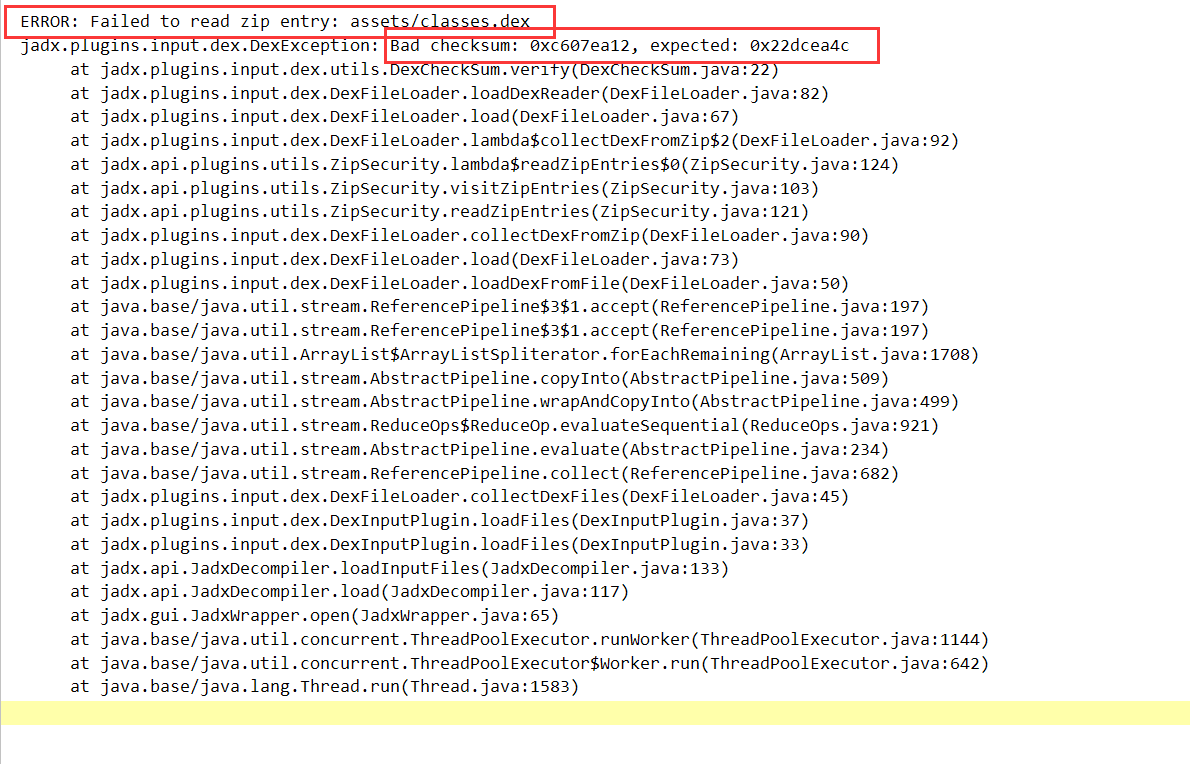
然后我们使用jadx打开apk,发现下方日志报错
先不管报错,我们先查看生成的伪代码。
可以看到前面主要是初始化一个包含文本和手势解锁功能的Android Activity,进行加载布局,设置文本内容并初始化手势解锁控件及其监听器等内容
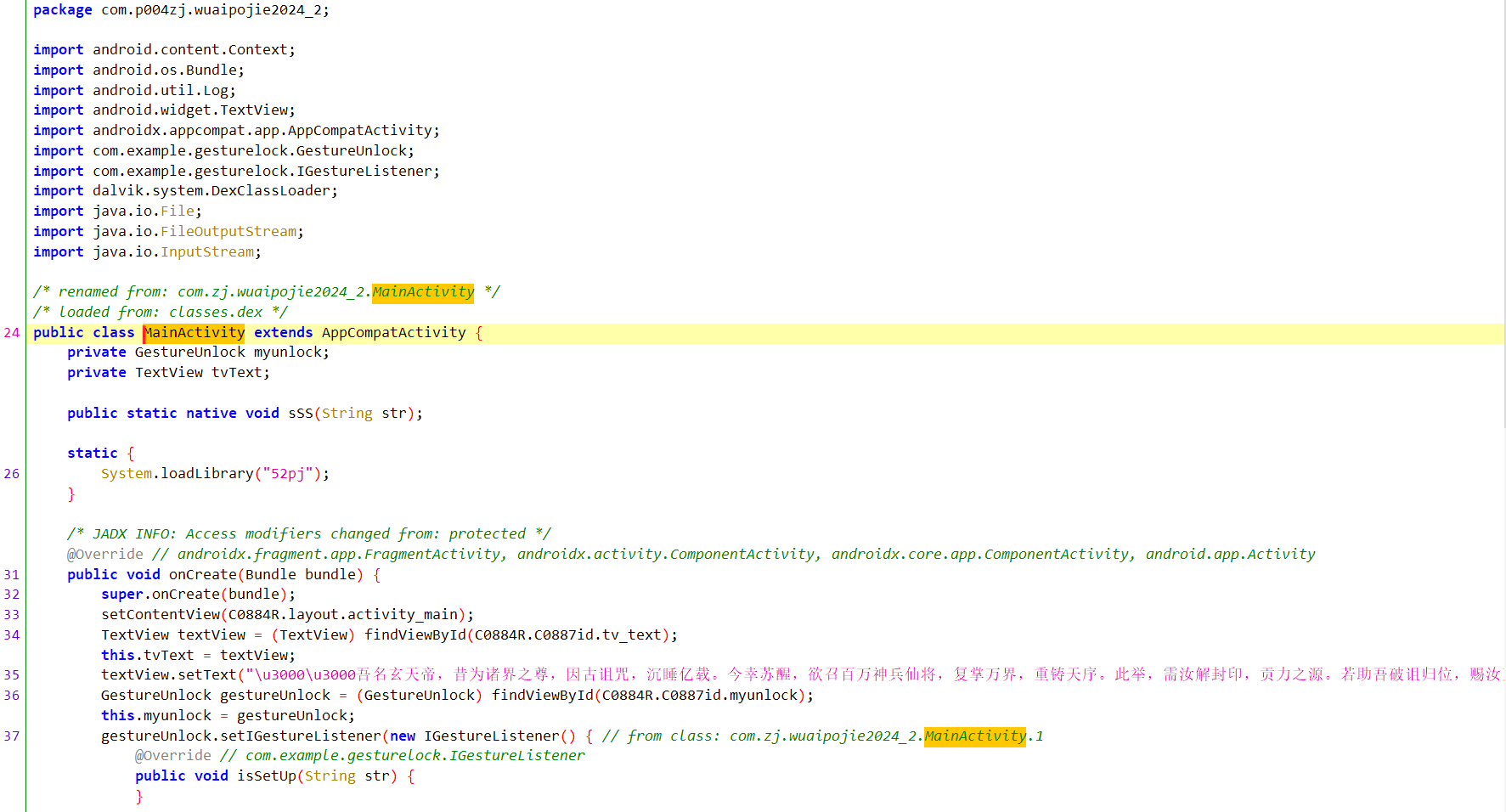
着重关注下面这个地方的代码,我们发现只有在进入了isError函数以后才会调用checkPassword函数
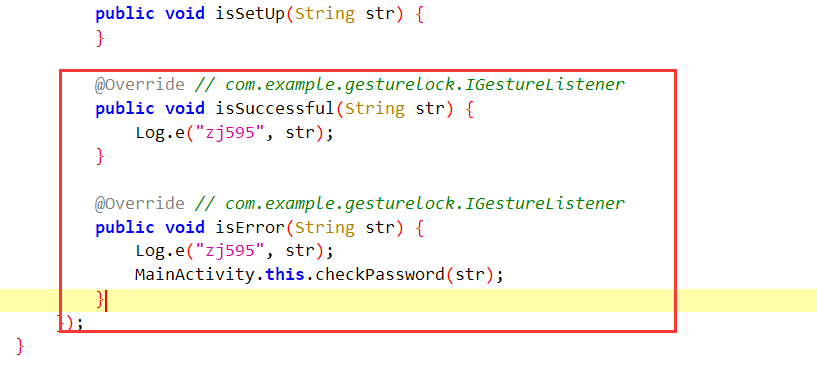
然后看checkPassword函数,
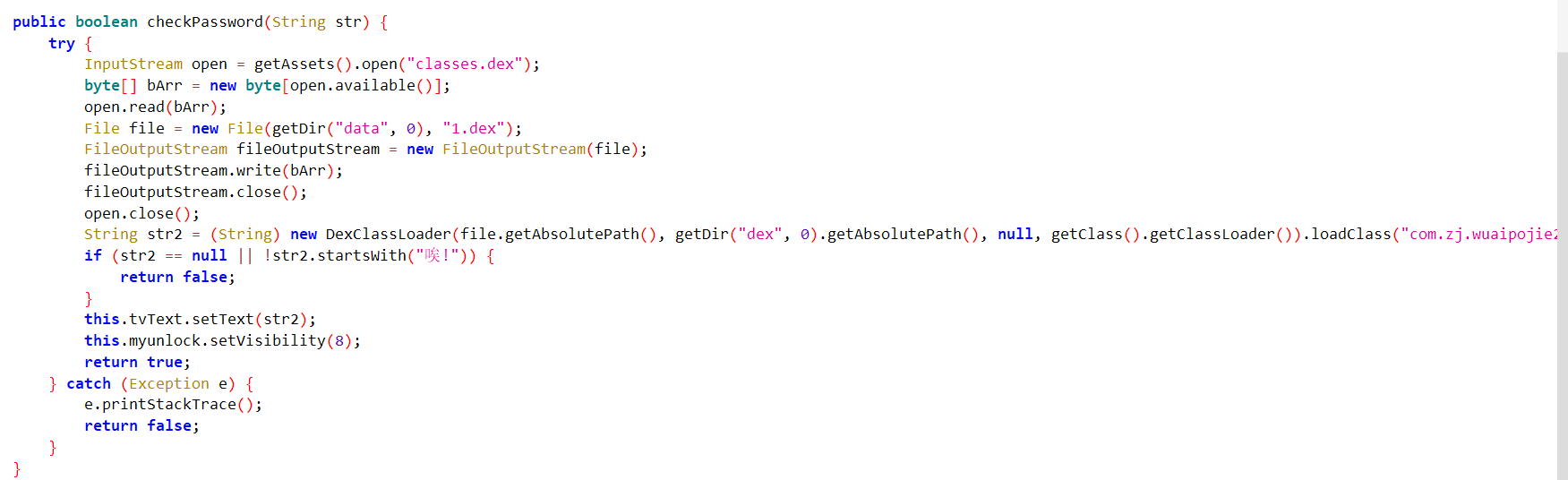
这个函数关键的地方:
其实就是实现读取将assets目录下面的classes.dex,然后通过数据流写入到apk的data这个目录下面的1.dex文件中
然后通过使用DexClassLoader类动态加载刚被写入数据的1.dex文件,加载com.zj.wuaipojie2024_2.C类,调用其中声明的 isValidate方法
这里把下面的代码拎出来:
String str2 = (String) new DexClassLoader(file.getAbsolutePath(), getDir(“dex”, 0).getAbsolutePath(), null, getClass().getClassLoader()).loadClass(“com.zj.wuaipojie2024_2.C”).getDeclaredMethod(“isValidate”, Context.class, String.class, int[].class).invoke(null, this, str, getResources().getIntArray(C0884R.array.A_offset));
可以看到isValidate方法的参数(在反射里面),分别为当前MainActivity 实例),密码字符串 str和array.A_offset数组
然后再去看MainActivity里面提到的GestureUnlock 类
前面其实就是一些视觉元素的初始化与配置,触摸事件处理,绘图逻辑以及手势验证,配置与回调等
1 | |
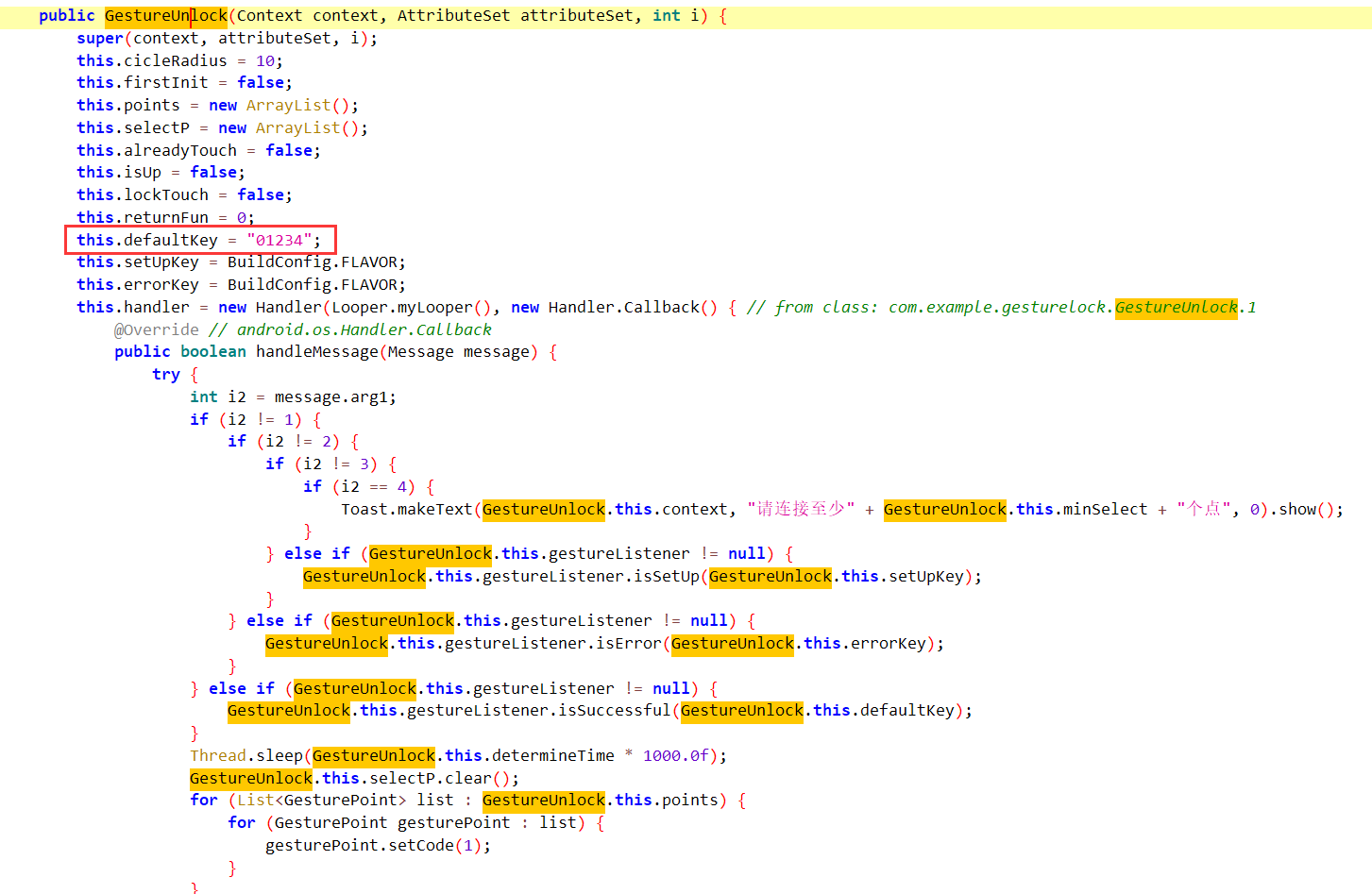
结合最下方的setDefaultKey函数,
而我们通过检查引用发现setDefault函数没有被引用
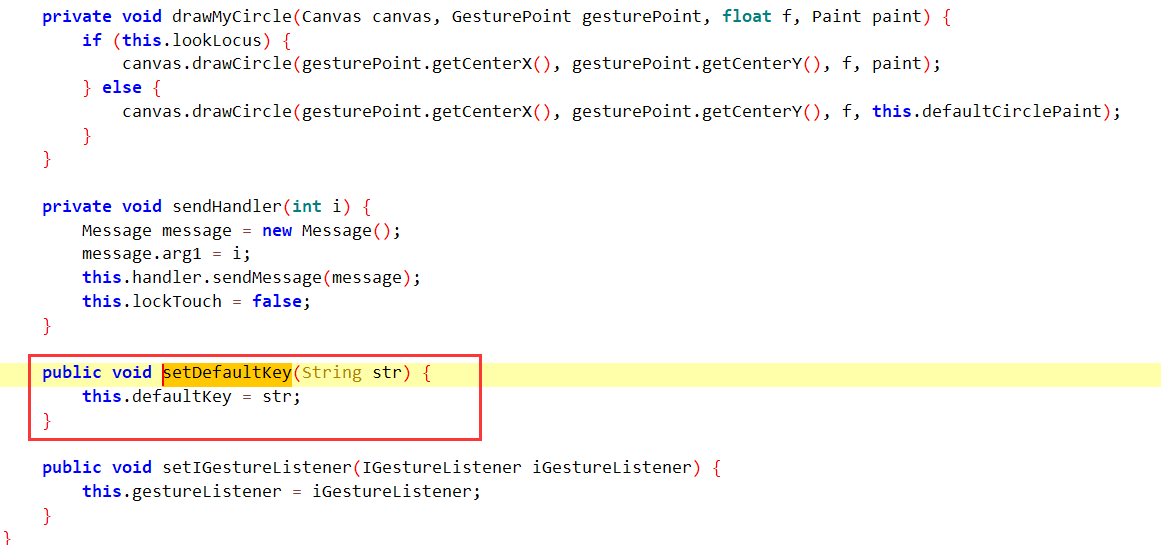
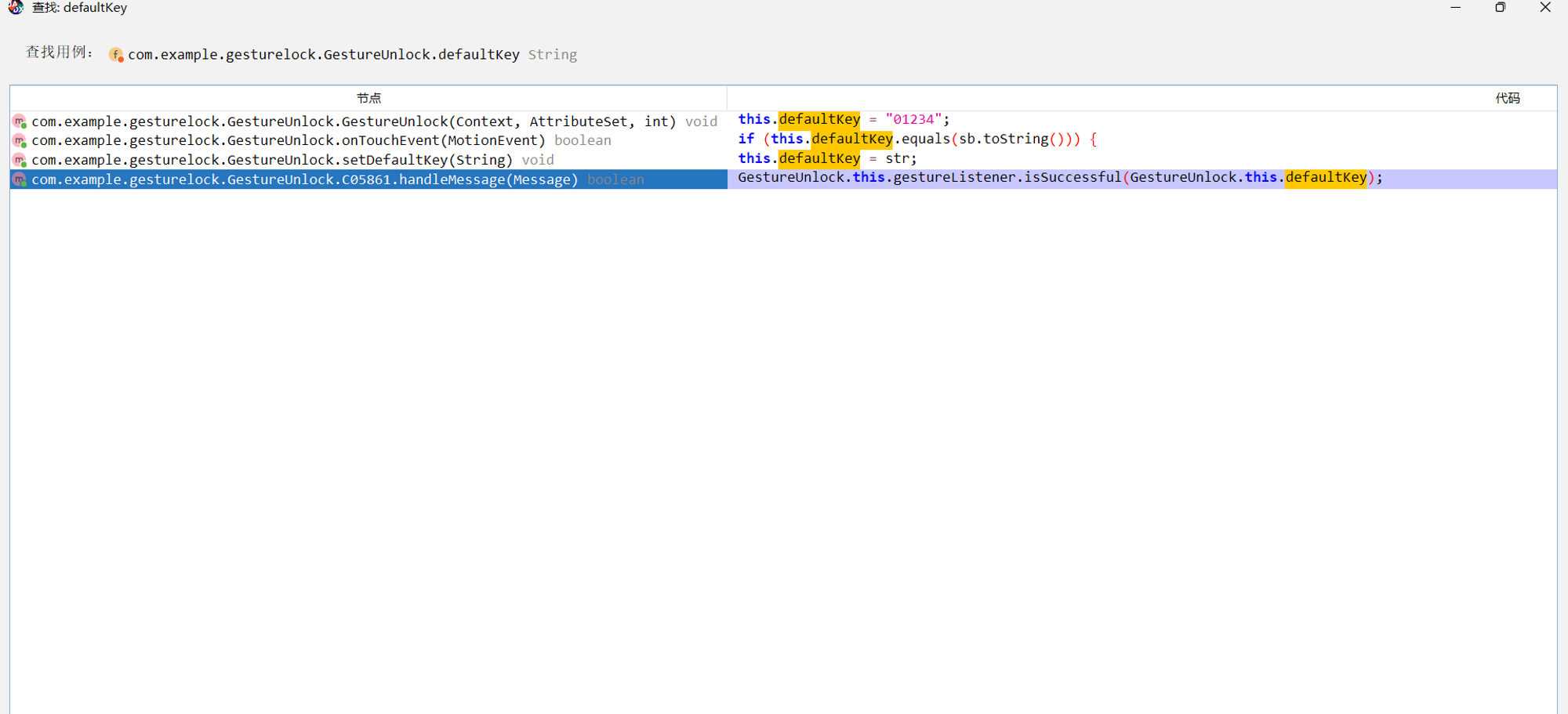
我们可以知道这个”01234“没有被更改过,就是密码锁的密码
而每个点在安卓系统中的图形密码九宫格中是按照从左至右、从上至下的顺序依次编号的,从0到8,这种编号方式如下所示:
1 | |
所以解锁密码应该是这样的
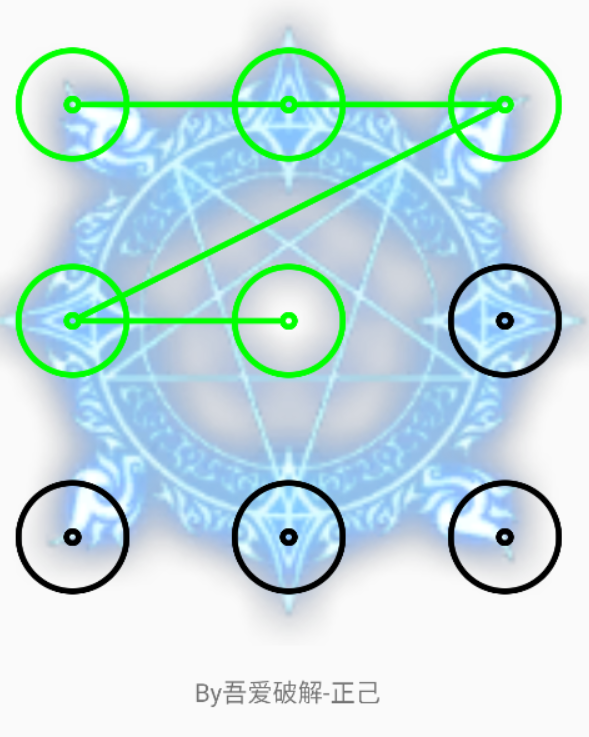
但是发现仍然没有flag(还是太单纯了)
接下来我们就去分析最开始看到的com.zj.wuaipojie2024_2.C类
发现jadx里面找不到,这个时候我们就可以想到最开始使用jadx加载apk时的报错
我们可以将apk解包获取其中assets下的classes.dex然后放入010Editor导入DEX模板进行分析(其实还有个方法,使用jeb打开能直接看到com.zj.wuaipojie2024_2.C类)
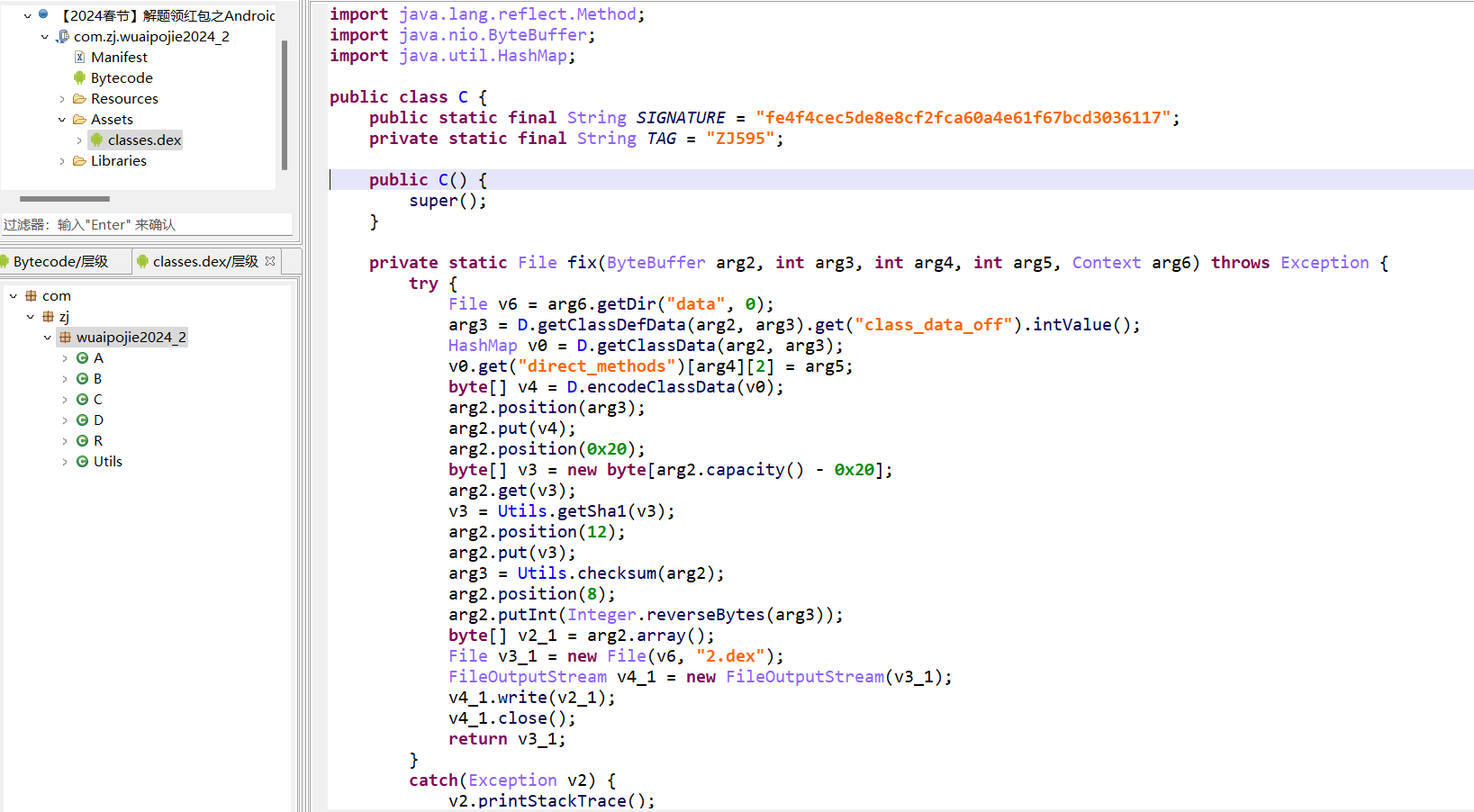
但是还是按照正常逻辑思路来
如果你的010Editor里面没有对应模板
可以进入下载:010 editor 应用templates分析ELF和dex文件_010editor 分析elf-CSDN博客
下载完成以后在010Editor里面的Template选项栏里面找到edit template添加我们刚刚下载好的DEX模板
运行模板,效果如下

最下方报错
Alder32 checksum did not match, expected 22DCEA4C but got C607EA12
Sha1 checksum did not match, expected AA63B92A4B9CA5F53A514B9D620230485C80F0E2 but got DA6A6ECE23966B5BFAA9E922D501E8BB94CA4F9C
Result = 2 warnings found, template may not have run successfully!
所以选择修复DEX
网上随便找个修复教程将这两处的数据修改为正确的即可,当然也可以单独针对这两个部分合理使用AI进行脚本书写
修复后的dex再次拖入010则报错消失
这个时候将dex单独拖入jadx也可以正确的显示出com.zj.wuaipojie2024_2.C类了
其实这个地方可以看到signature(后面会用来进行签名校验的比较,所以这个题如果进行冲打包改了签名的话应该是不可以的)
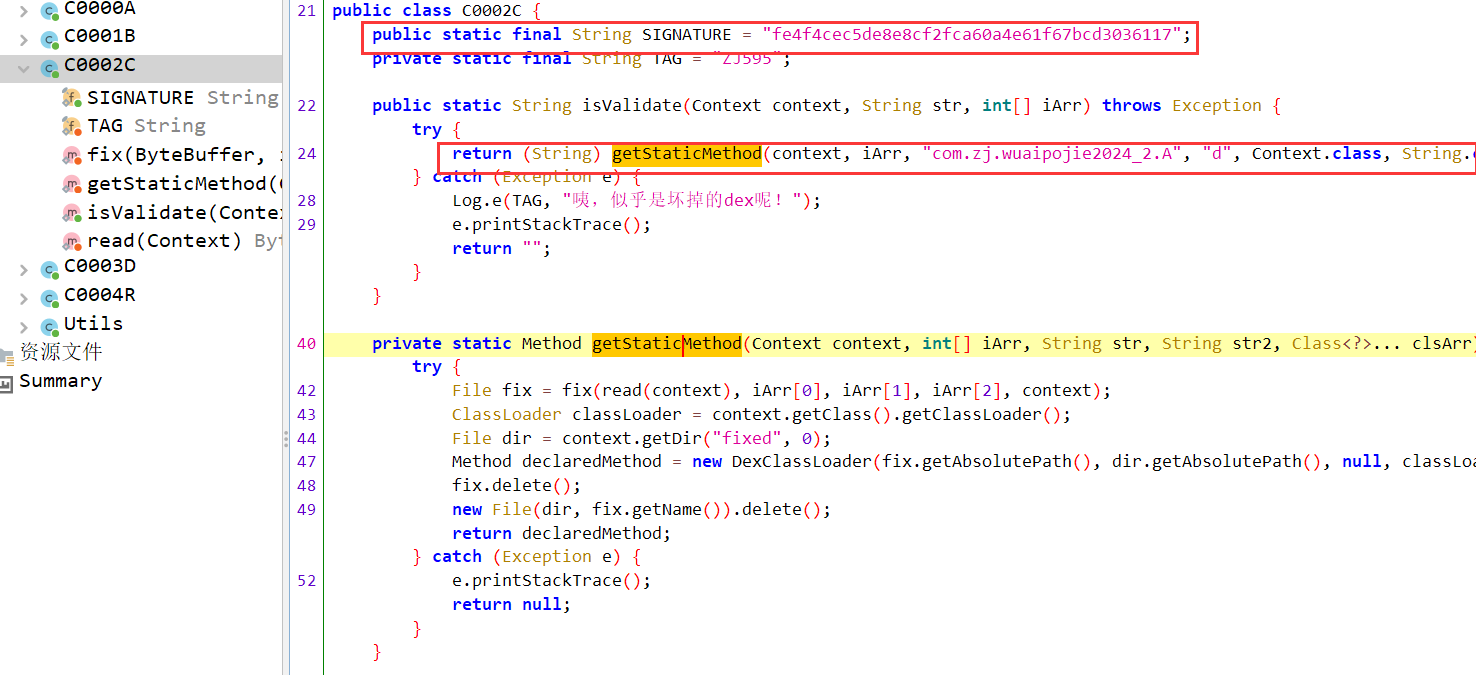
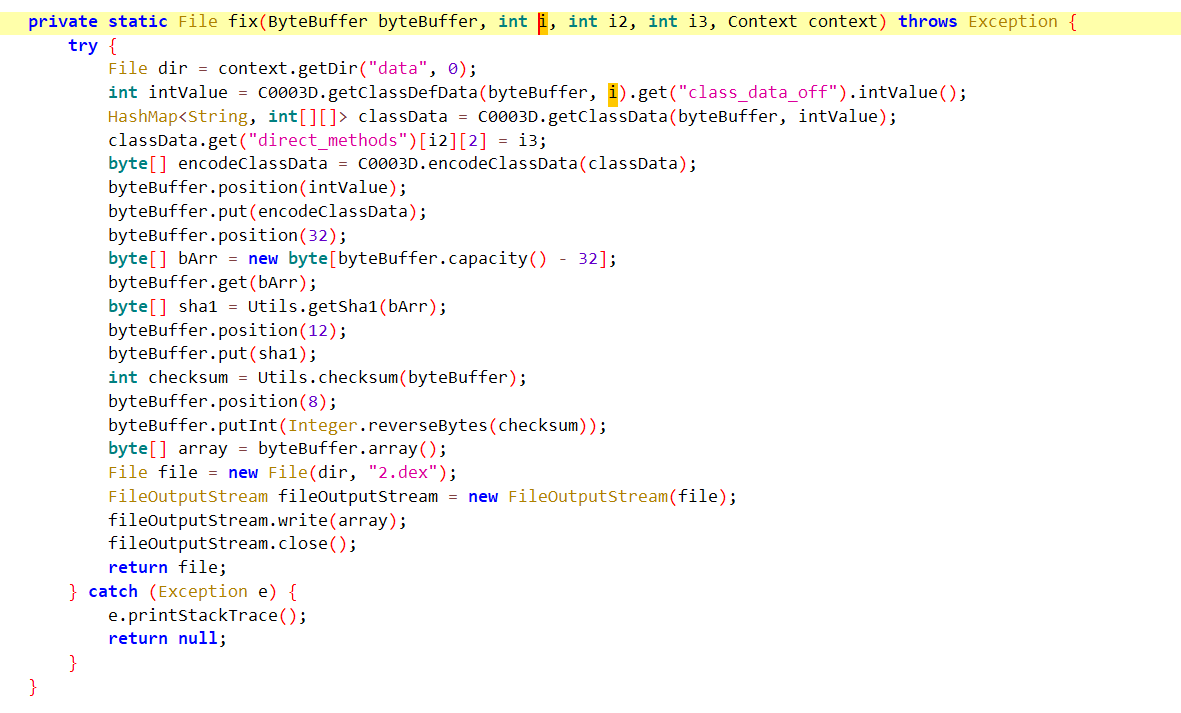
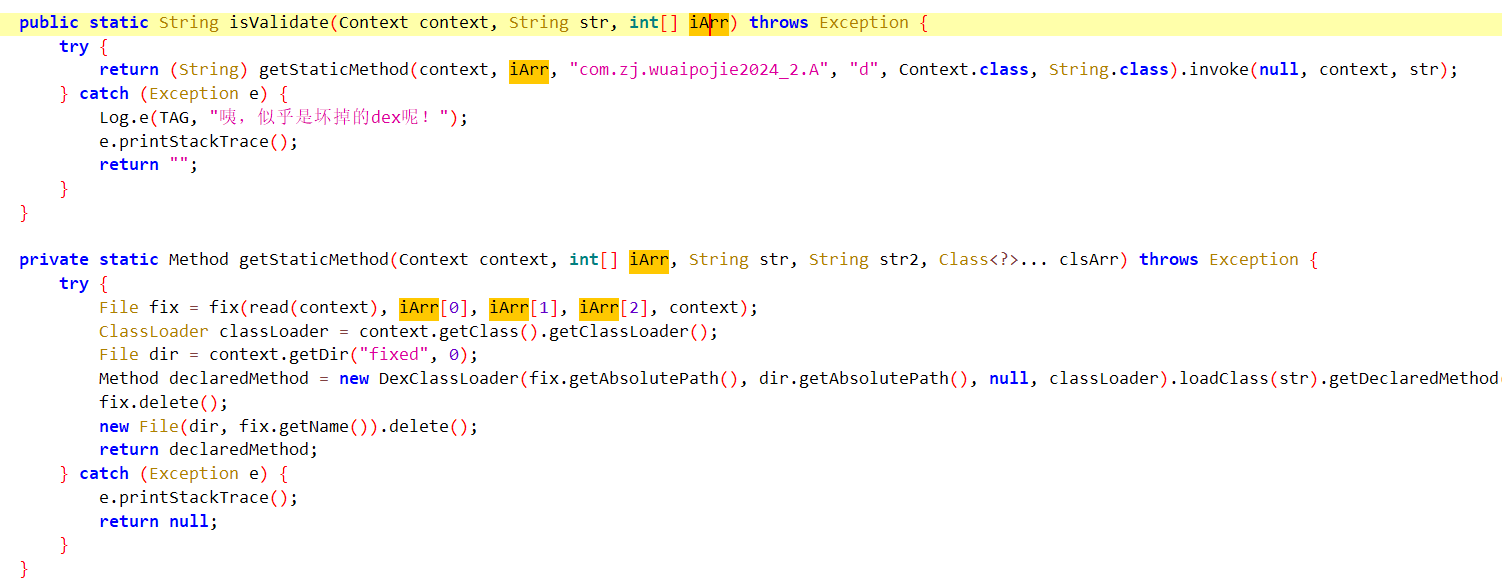
关注第二个框框,结合下面的两个函数我们可以知道,这个地方就是getStaticMethod返回为com.zj.wuaipojie2024_2.A 类,d方法,而这个方法是通过read方法读取data目录下的decode.dex,然后再被fix函数调用生成2.dex(即被修复完成)
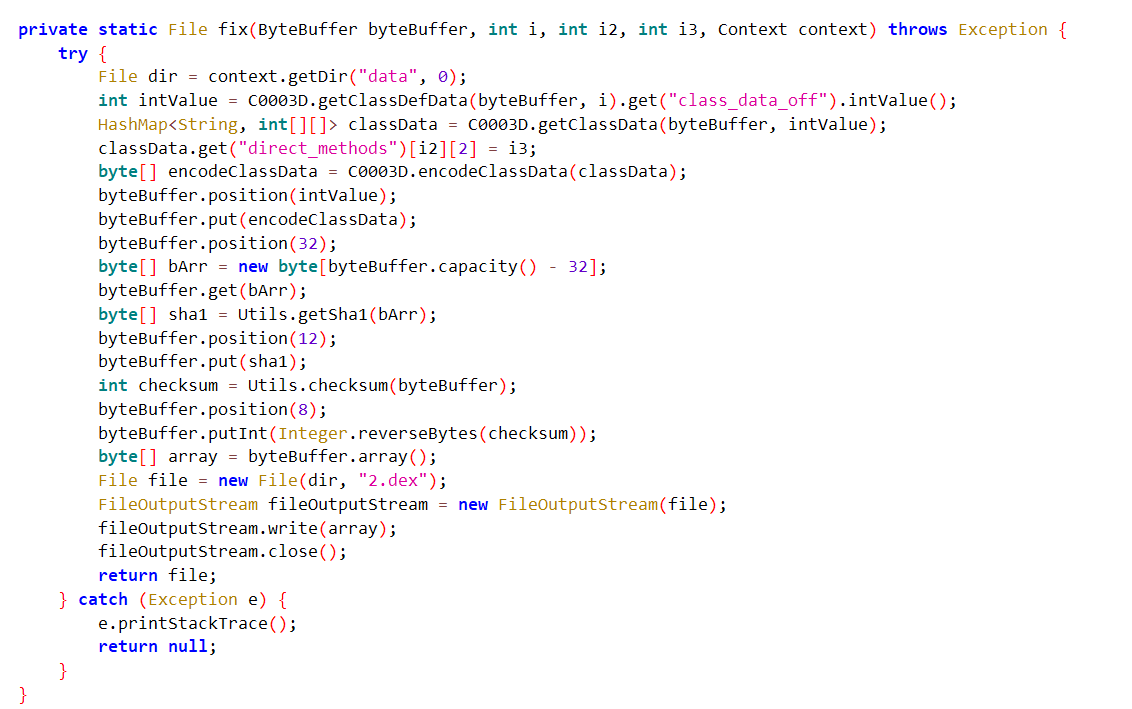
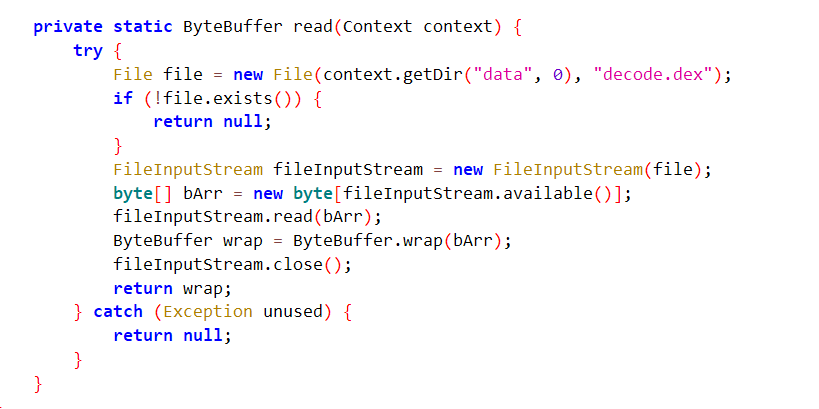
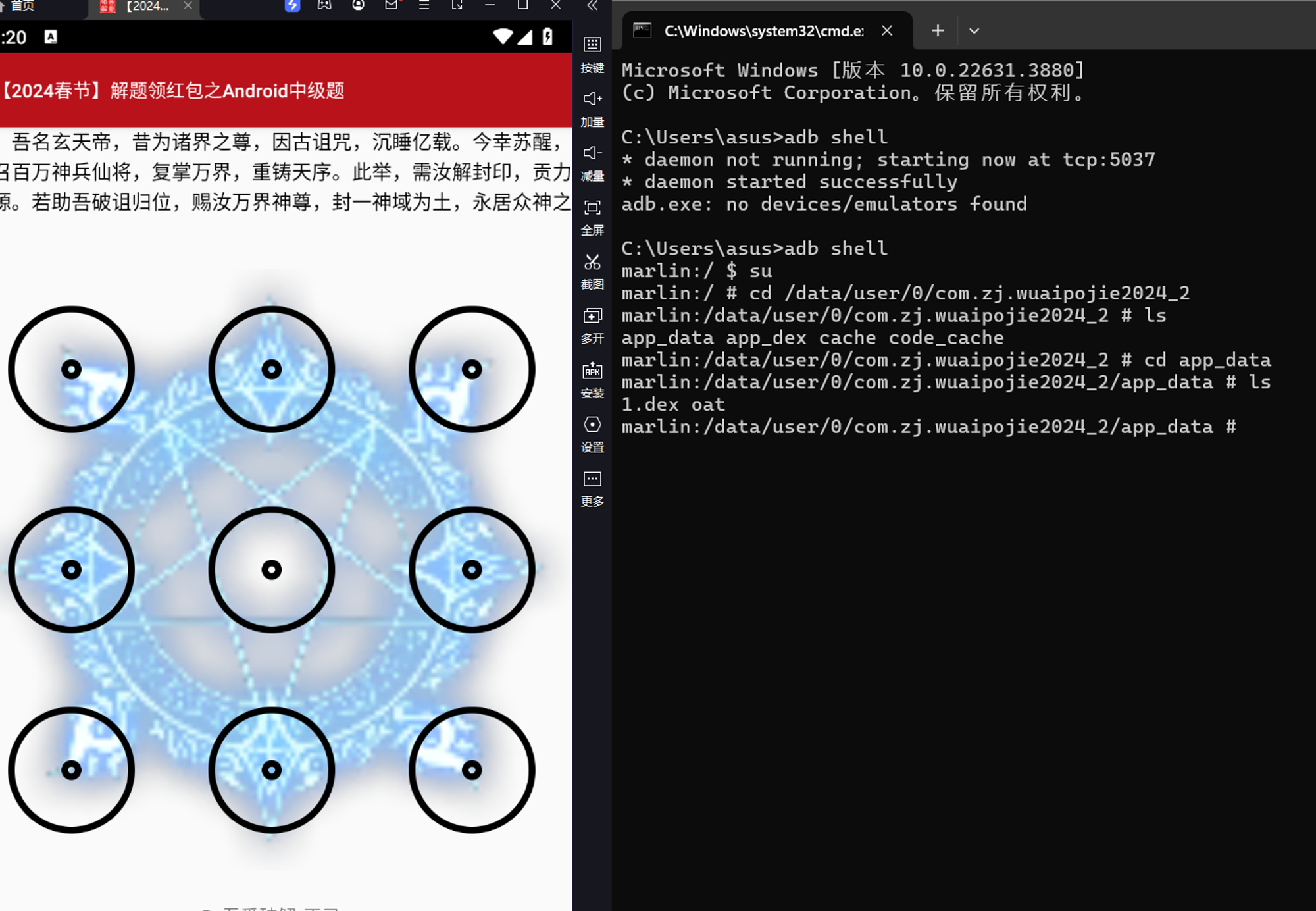
所以我们现在有一个思路就是直接将data目录1.dex的数据赋值给decode.dex,然后再次运行程序获得修复完成的2.dex
但是要注意,获得1.dex的时候要避免输入默认的正确的密码锁密码“01234”,不然不会走生成1.dex的checkpassword函数
继续再次运行但是发现原路径下没有2.dex,发现是在getStaticMethod将生成的2.dex删了
使用frida尝试了下将2.dex勾出来,没成功
换思路
我们知道最后修复后是com.zj.wuaipojie2024_2.A 类中的d方法
通过com.p000zj.wuaipojie2024_2 下的函数(分析参数传递)
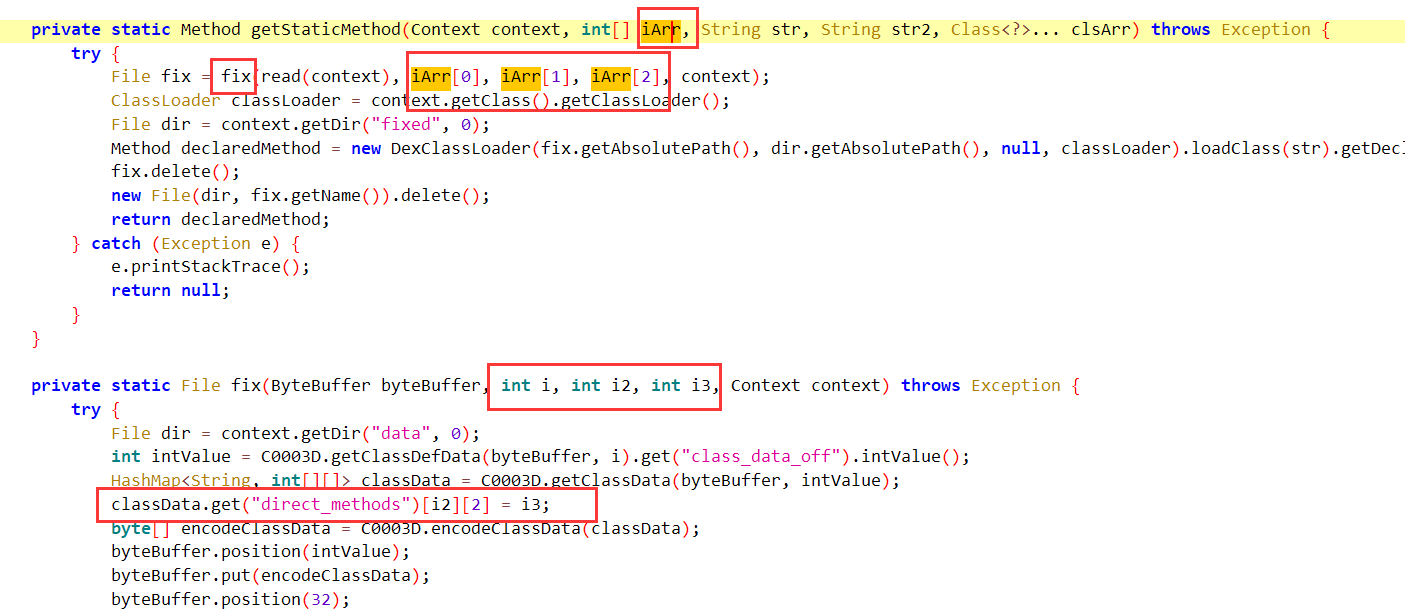
再结合最初我们分析的isValidate的参数,发现这里的i,i2,i3即为array.A_offset 中的值
使用NP管理器
使用ARSC打开方式
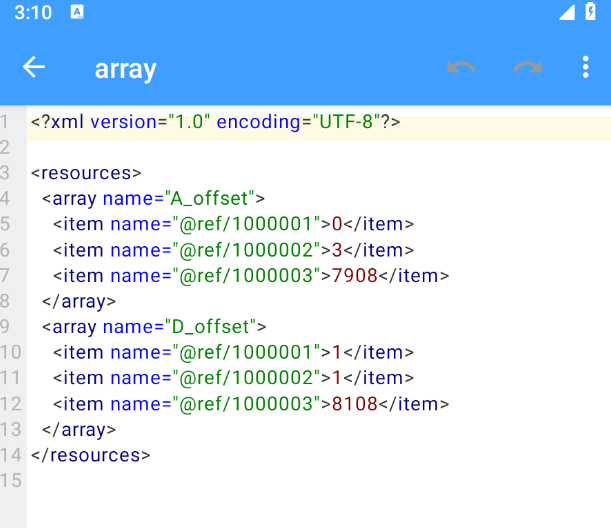
找到对应的值
即 i = 0 , i2 = 3 , i3 = 7908
在fix函数中,发现偏移量的计算与encodeClassDate有关
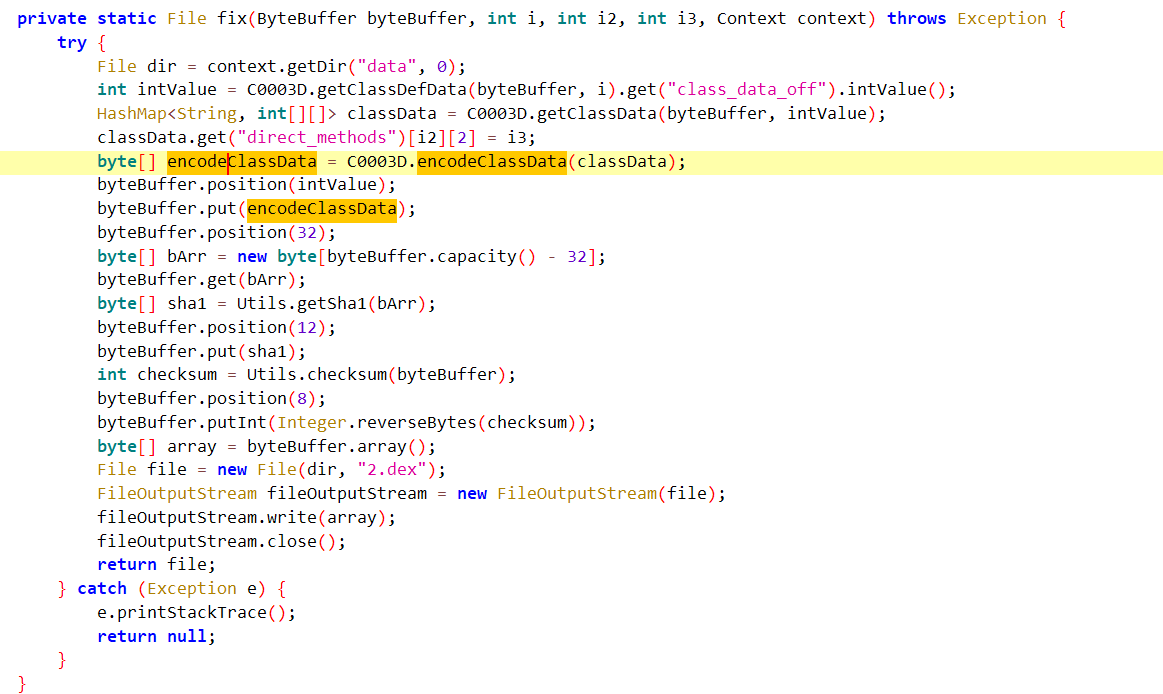
跟进
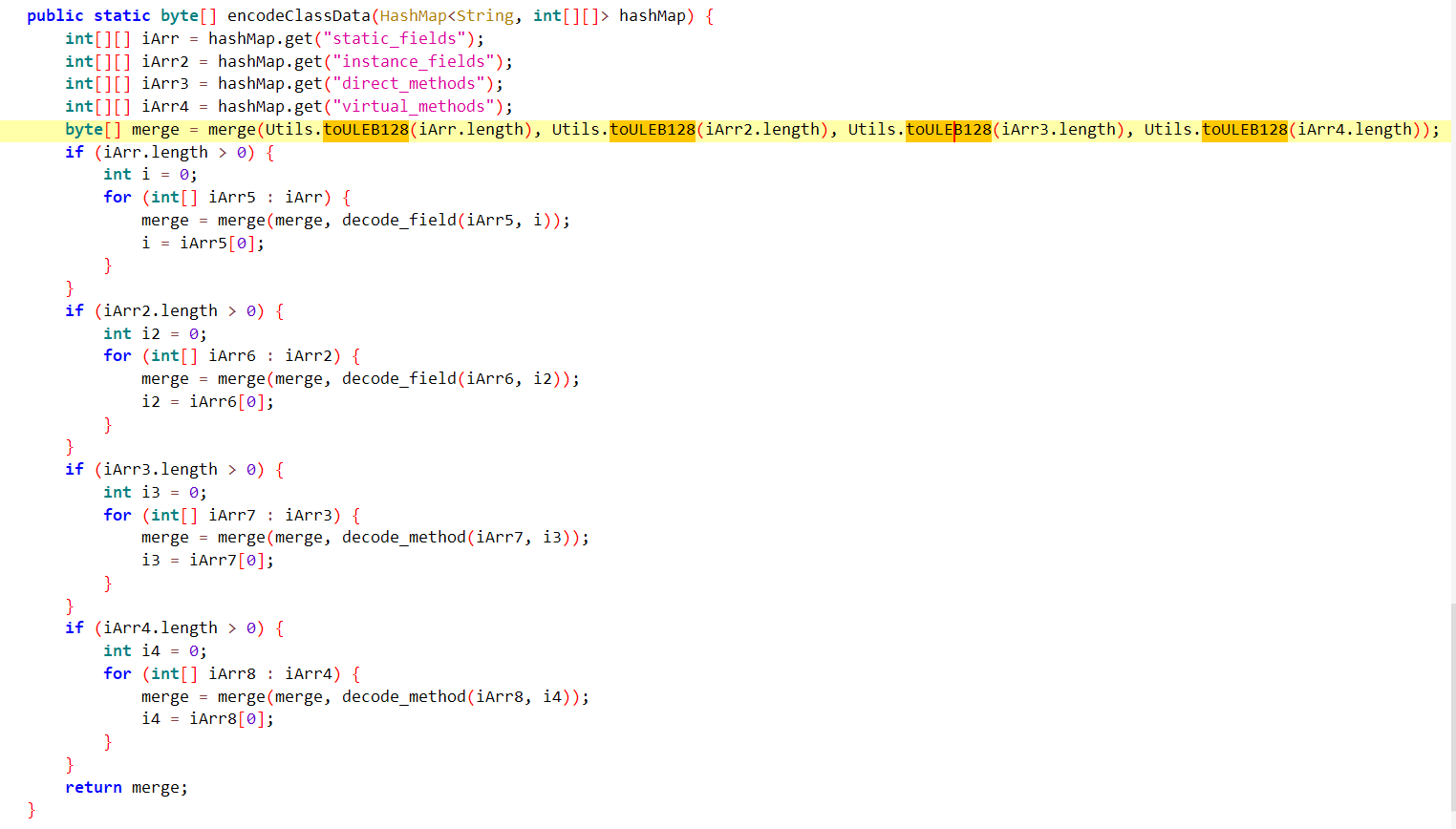
发现对数据进行了toULEB128——通常用于将整数编码为无符号 LEB128 格式的字节数组,是一种变长编码方式,用于有效地编码小整数
经过对比发现是标准编码,所以直接通过在线网站进行数转换即可
7908 转换过来是E4 3D
所以我们用010打开classes.dex,
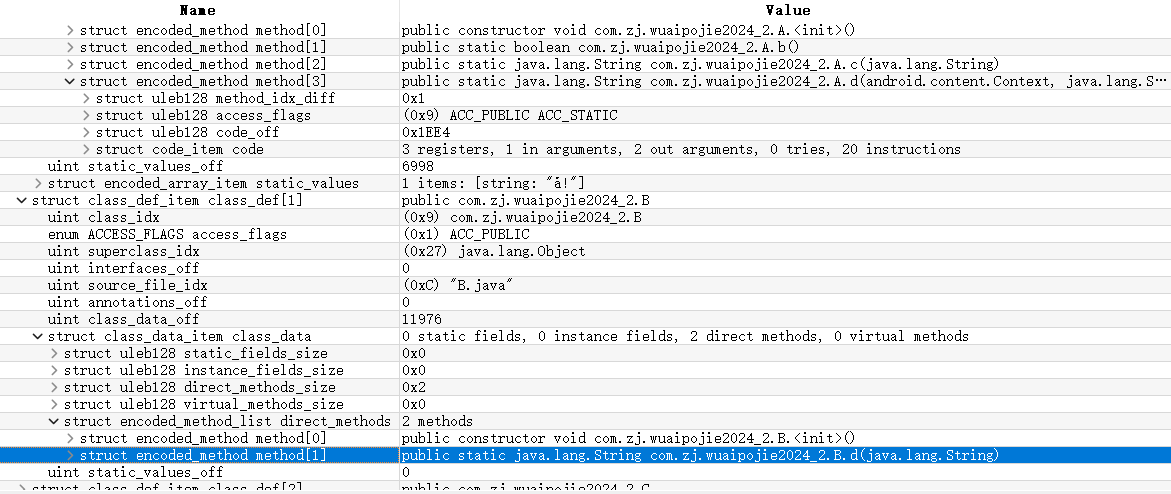
struct class_def_item_list dex_class_defs——>struct class_def_item class_def[0]——>struct class_data_item class_data——>struct encoded_method_list direct_methods——>struct encoded_method method[3]——>struct uleb128 code_off
然后修改下方的数据,修改后再次使用最开始的脚本进行恢复

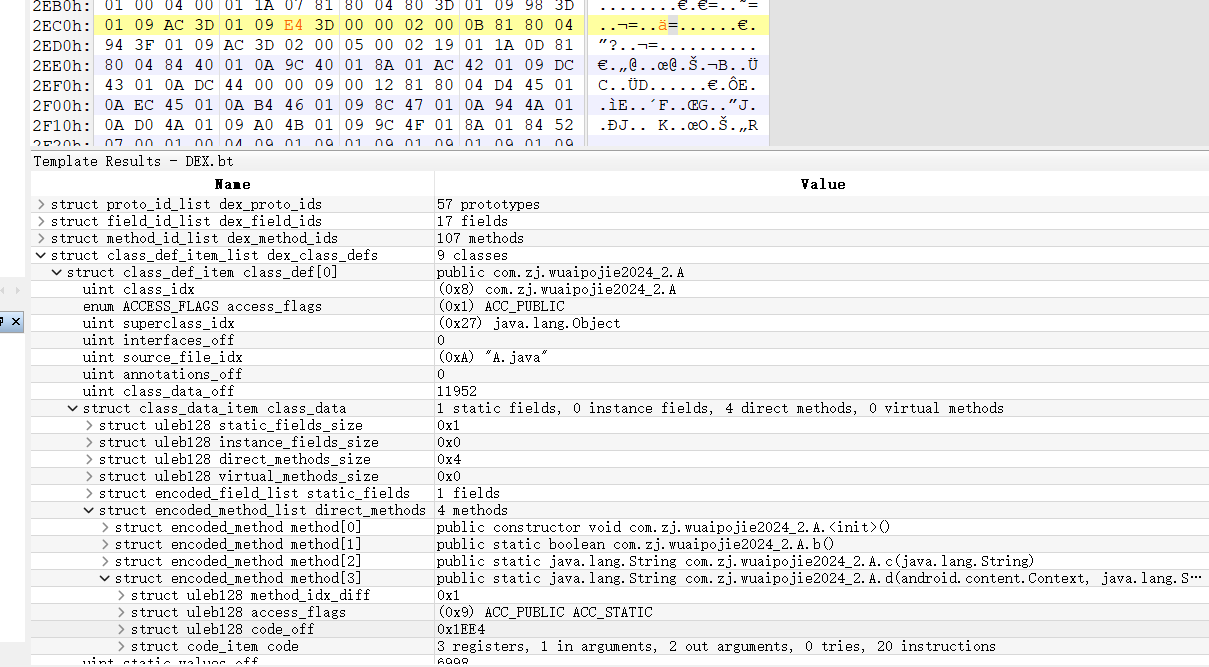
再次打开classes.dex,发现A.d数据被恢复
1 | |
分析这段代码我们可以知道stringBuffer长度为9,所以密码是“048531267”
同时得到提示“坐标在B.d”处
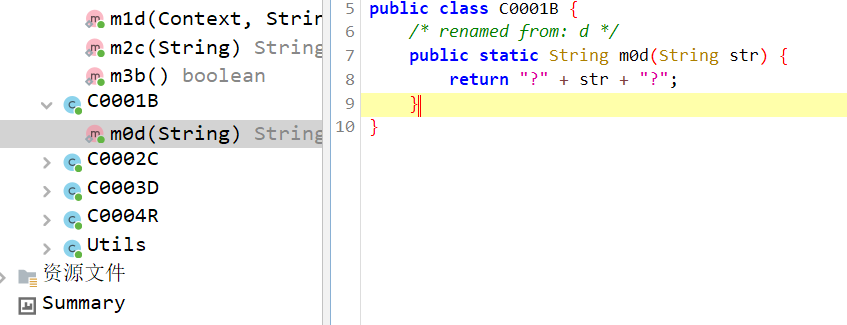
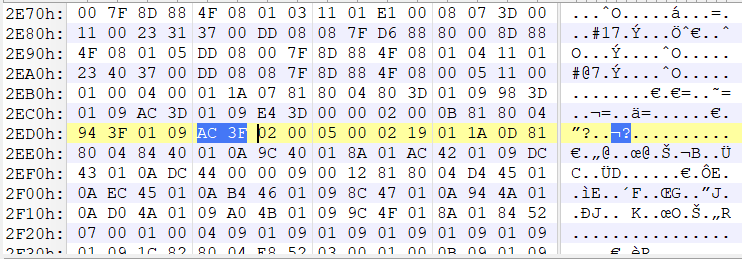
通过之前在np管理器中获取的数据
我们可以知道为[1,1,8108],8108转换后的数据是AC 3F
同样找到B.d,修改code_off处数据
修改后继续使用脚本修复
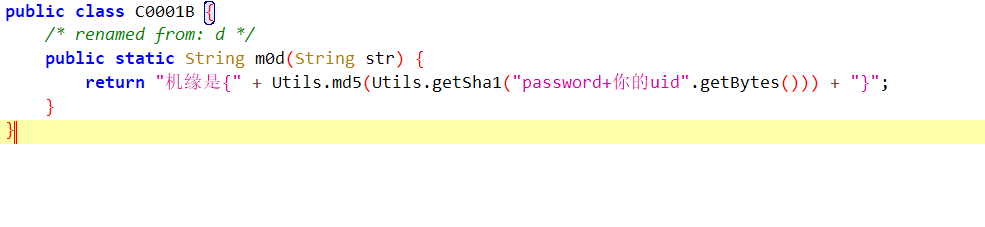
所以flag是
flagmd5(sha1{048531267+’id’})
deeprev
使用finger进行符号恢复
找到main函数并进行重命名
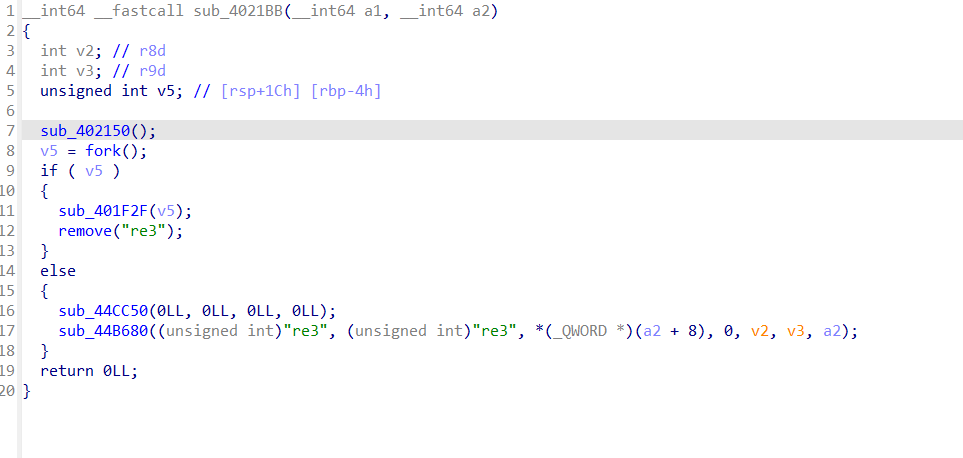
如下
int __cdecl main(int argc, const char **argv, const char **envp)
{
double v3; // xmm0_8
double v4; // xmm1_8
double v5; // xmm2_8
double v6; // xmm3_8
double v7; // xmm6_8
double v8; // xmm7_8
__int64 v9; // r8
__int64 v10; // r9
double v11; // xmm4_8
double v12; // xmm5_8
__int64 v14; // [rsp+0h] [rbp-20h]
unsigned int v15; // [rsp+1Ch] [rbp-4h]
sub_402150();//打开文件 “re3”,将 unk_4BC380 的内容写入到该文件中,然后关闭文件,调用 mprotect_0 函数设置内存保护
v15 = fork();
if ( v15 )
{
sub_401F2F(v15);
remove(“re3”);
}
else
{
sub_44CC50(0LL, 0LL, 0LL, 0LL, v9, v10, (char)argv);
sub_44B680((__int64)”re3”, (__int64)”re3”, v3, v4, v5, v6, v11, v12, v7, v8, *(_QWORD *)(v14 + 8), 0LL);
}
return 0;
}
学习一下fork的性质:fork函数 - 简书 (jianshu.com)
打开unk_4BC380将文件re3的数据提取出来
1 | |
通过数据长度b_length为5CF0h,lazy_dumper导出ELF数据,导出为ELF文件
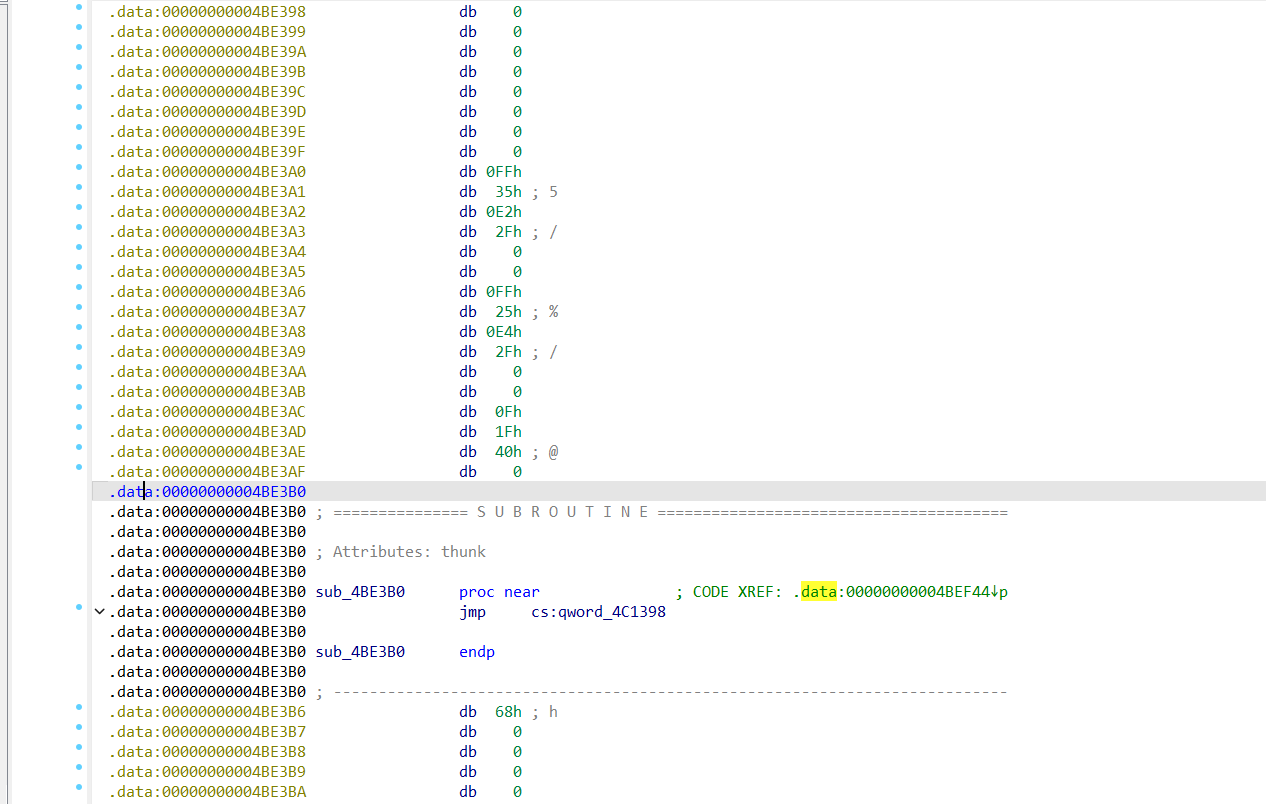
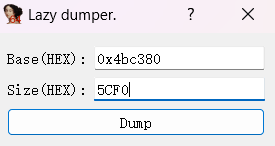
将得到的ELF文件使用IDA打开,发现没有main函数,进入start函数,发现爆红无法生成伪代码,我们全选start函数后u取消识别,再次全选c识别成代码,Force强制转换成代码形式后再次在start点p创建函数
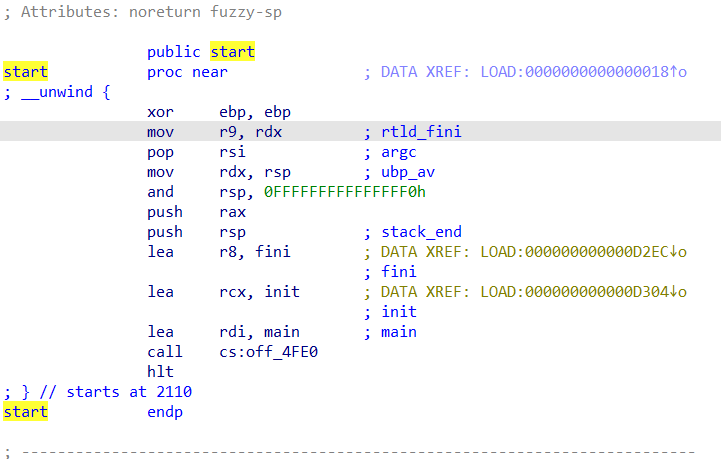
出现main函数
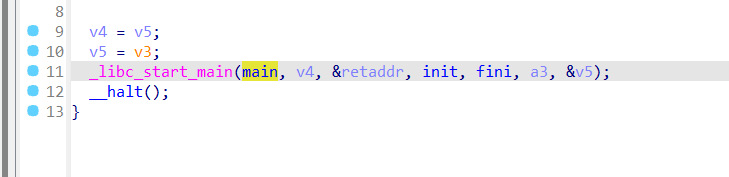
对绿色数据区域c转换成代码,再在main处p创建函数
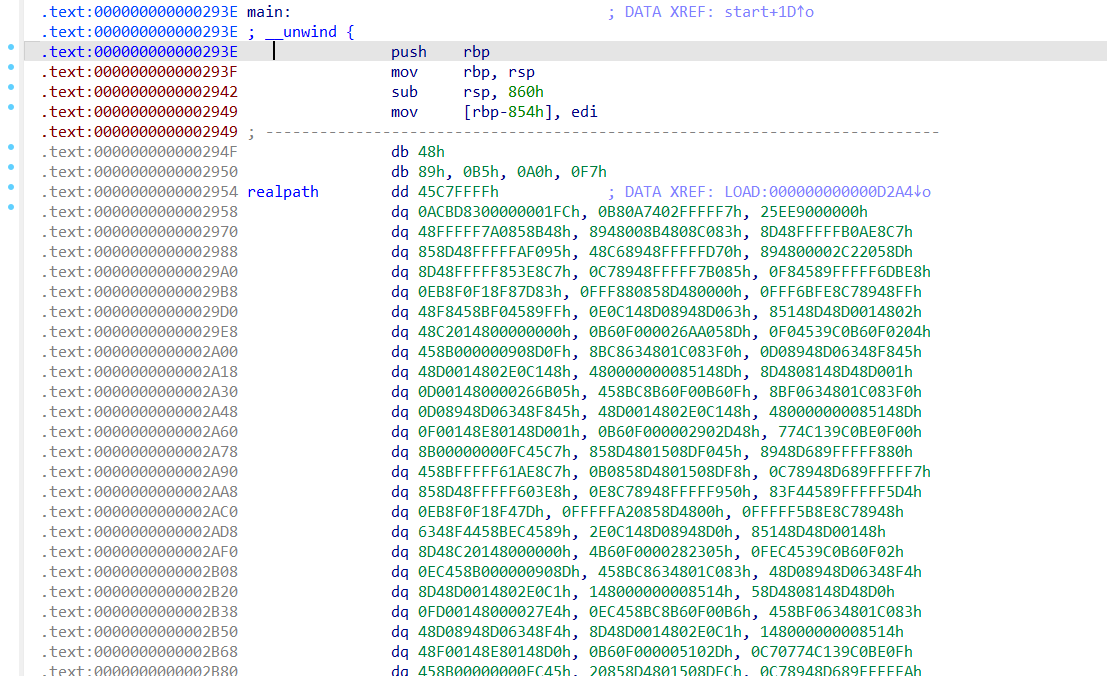
得到main函数
__int64 __fastcall main(int a1, char **a2, char **a3)
{
struct __jmp_buf_tag env[1]; // [rsp+10h] [rbp-850h] BYREF
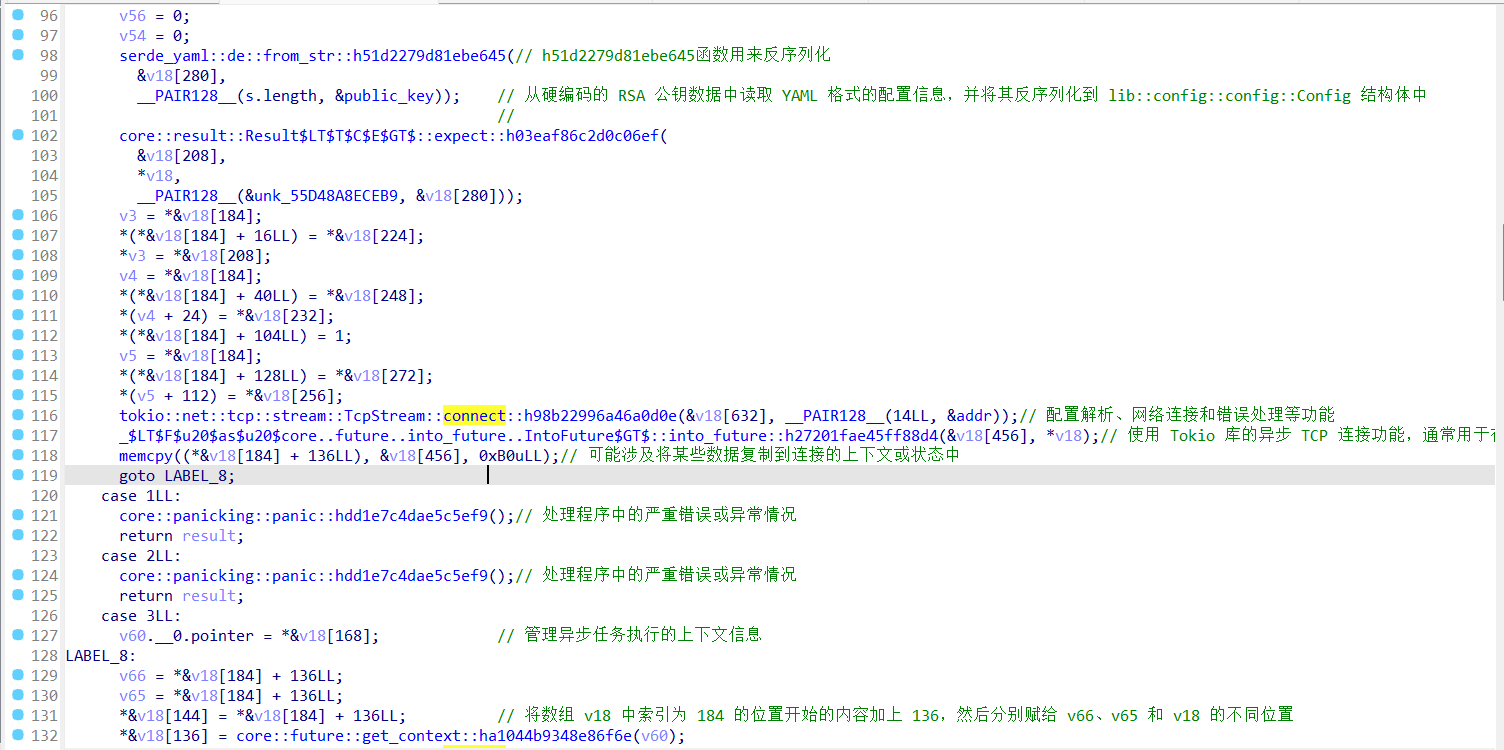
struct __jmp_buf_tag v5[1]; // [rsp+E0h] [rbp-780h] BYREF
struct __jmp_buf_tag v6[1]; // [rsp+1B0h] [rbp-6B0h] BYREF
struct __jmp_buf_tag v7[1]; // [rsp+280h] [rbp-5E0h] BYREF
char v8[640]; // [rsp+350h] [rbp-510h] BYREF
char v9[636]; // [rsp+5D0h] [rbp-290h] BYREF
int v10; // [rsp+84Ch] [rbp-14h]
int v11; // [rsp+850h] [rbp-10h]
int v12; // [rsp+854h] [rbp-Ch]
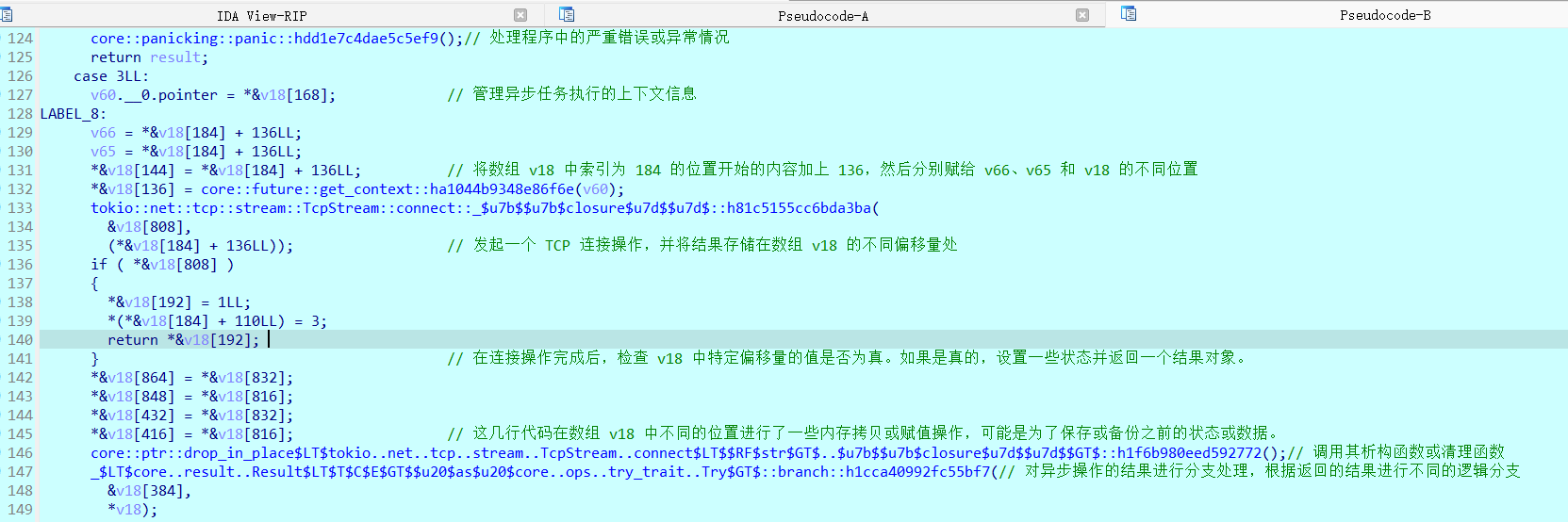
int v13; // [rsp+858h] [rbp-8h]
int v14; // [rsp+85Ch] [rbp-4h]
__int64 savedregs; // [rsp+860h] [rbp+0h] BYREF
v14 = 1;
if ( a1 != 2 )
return 0LL;
((void (__fastcall *)(char *, char **, char **))loc_2490)(a2[1], a2, a3);
((void (__fastcall *)(void *, char *, char *))loc_21F9)(&unk_55C0, v9, v8);
v13 = _setjmp(env);
if ( v13 <= 24 )
{
v11 = _setjmp(v5);
if ( v11 < byte_50A0[25 * v13] )
{
if ( byte_50A0[25 * v13 + 1 + v11] != *((char *)&savedregs + 25 * v13 + v11 - 655) )
v14 = 0;
longjmp(v5, v11 + 1);
}
longjmp(env, v13 + 1);
}
v12 = _setjmp(v6);
if ( v12 <= 24 )
{
v10 = _setjmp(v7);
if ( v10 < byte_5320[25 * v12] )
{
if ( byte_5320[25 * v12 + 1 + v10] != *((char *)&savedregs + 25 * v12 + v10 - 1295) )
v14 = 0;
longjmp(v7, v10 + 1);
}
longjmp(v6, v12 + 1);
}
if ( v14 == 1 )
puts(“GOOD JOB”);
return 0LL;
}
对loc_2490进行相同操作最后创建为函数
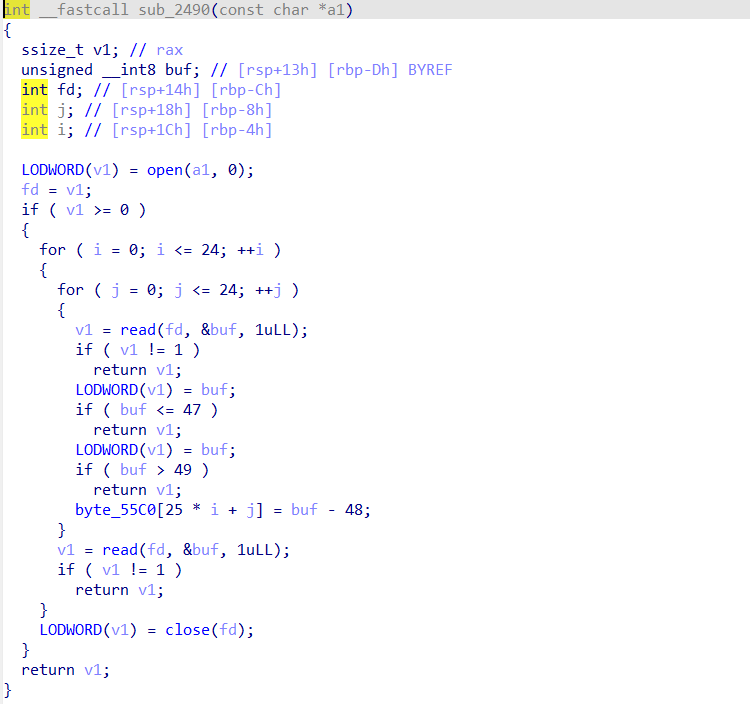
sub_2490即对数据进行读取并存储
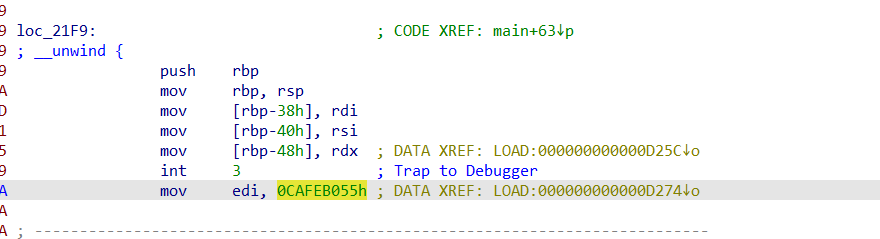
而loc_21F9则不行,经过c转换后可以看到int 3,所以我们猜测这个地方被做了处理,为smc或者其他加密形式,而可以猜测执行的时候这个地方是触发中断后将这个信号传递给主进程,然后主进程对这个地方进行解密
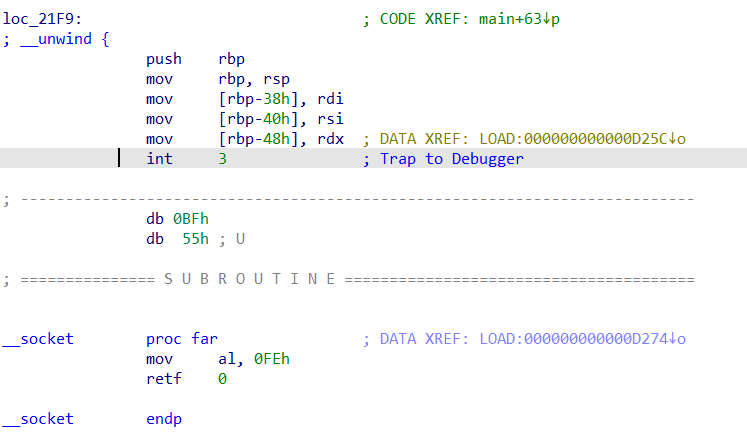
我们再回到最开始的题目进行分析
打开父进程的函数,其中sub_44CC50可以得出是ptrace函数,而又因为我们知道在re3文件中是中断信号然后返回父进程,而这里刚好通过if中捕获中断状态(具体可以看下文)的值然后来分别进行两个相似的操作,所以我们可以判断re3文件中的是smc
__int64 __fastcall sub_401F2F(unsigned int pid)
{
__int64 v1; // r8
__int64 v2; // r9
unsigned int v3; // ecx
__int64 v4; // rdx
__int64 result; // rax
__int64 v6; // r8
__int64 v7; // r9
__int64 v8; // r8
__int64 v9; // r9
__int64 v10; // r8
__int64 v11; // r9
__int64 v12; // r8
__int64 v13; // r9
__int64 v14; // r8
__int64 v15; // r9
char v16; // [rsp+0h] [rbp-130h]
char v17; // [rsp+0h] [rbp-130h]
char v18; // [rsp+0h] [rbp-130h]
char v19; // [rsp+0h] [rbp-130h]
unsigned int v20; // [rsp+10h] [rbp-120h]
__int64 v21; // [rsp+18h] [rbp-118h]
int v22; // [rsp+2Ch] [rbp-104h] BYREF
unsigned __int64 v23[16]; // [rsp+30h] [rbp-100h] BYREF
__int64 v24; // [rsp+B0h] [rbp-80h]
unsigned __int64 v25; // [rsp+108h] [rbp-28h]
__int64 v26; // [rsp+110h] [rbp-20h]
__int64 v27; // [rsp+118h] [rbp-18h]
int i; // [rsp+124h] [rbp-Ch]
__int64 v29; // [rsp+128h] [rbp-8h]
sub_44B360(pid, 0LL, 0);
ptrace(7LL, pid, 0LL, 0LL, v1, v2, v16); // 通过调用系统调用 sys_ptrace 来对目标进程进行控制和调试
v27 = sub_401A30(pid);
v3 = sub_4017E5();
result = v4;
v20 = v3;
v21 = v4;
for ( i = 0; i <= 2; ++i )
{
v22 = 0;
sub_44B360(pid, &v22, 0);
result = v22 & 0x7F;
if ( (v22 & 0x7F) == 0 )
break;
ptrace(12LL, pid, 0LL, v23, v6, v7, v17);
v26 = v24 - 1;
v25 = ptrace(1LL, pid, v24 - 1, 0LL, v8, v9, v18);
if ( v25 == 0xCAFEB055BFCCLL )
{
v29 = v26;
decode(pid, v26, v27, v20, v21);//经过分析和下面的encode函数形式基本是一样的
v24 = v26 + 10;
ptrace(13LL, pid, 0LL, v23, v12, v13, v19);
}
else if ( v25 == 0xCAFE1055BFCCLL )
{
encode(pid, v29, v26, v27, v20, v21);
v24 = v26 + 10;
ptrace(13LL, pid, 0LL, v23, v14, v15, v19);
}
result = ptrace(7LL, pid, 0LL, 0LL, v10, v11, v19);
}
return result;
}
上面的分析中我们可以通过对ptrace函数的第一个参数按m,然后搜索ptrace,获得具体的函数名称
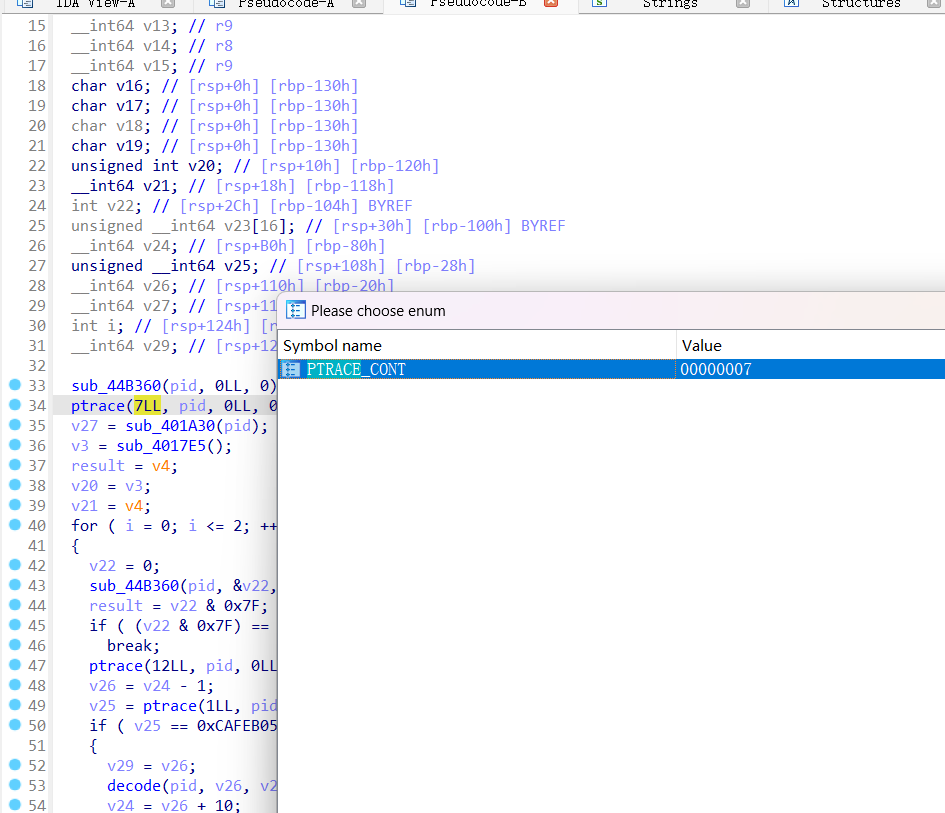
而ptrace的函数原型:
1 | |
对照下图作用:
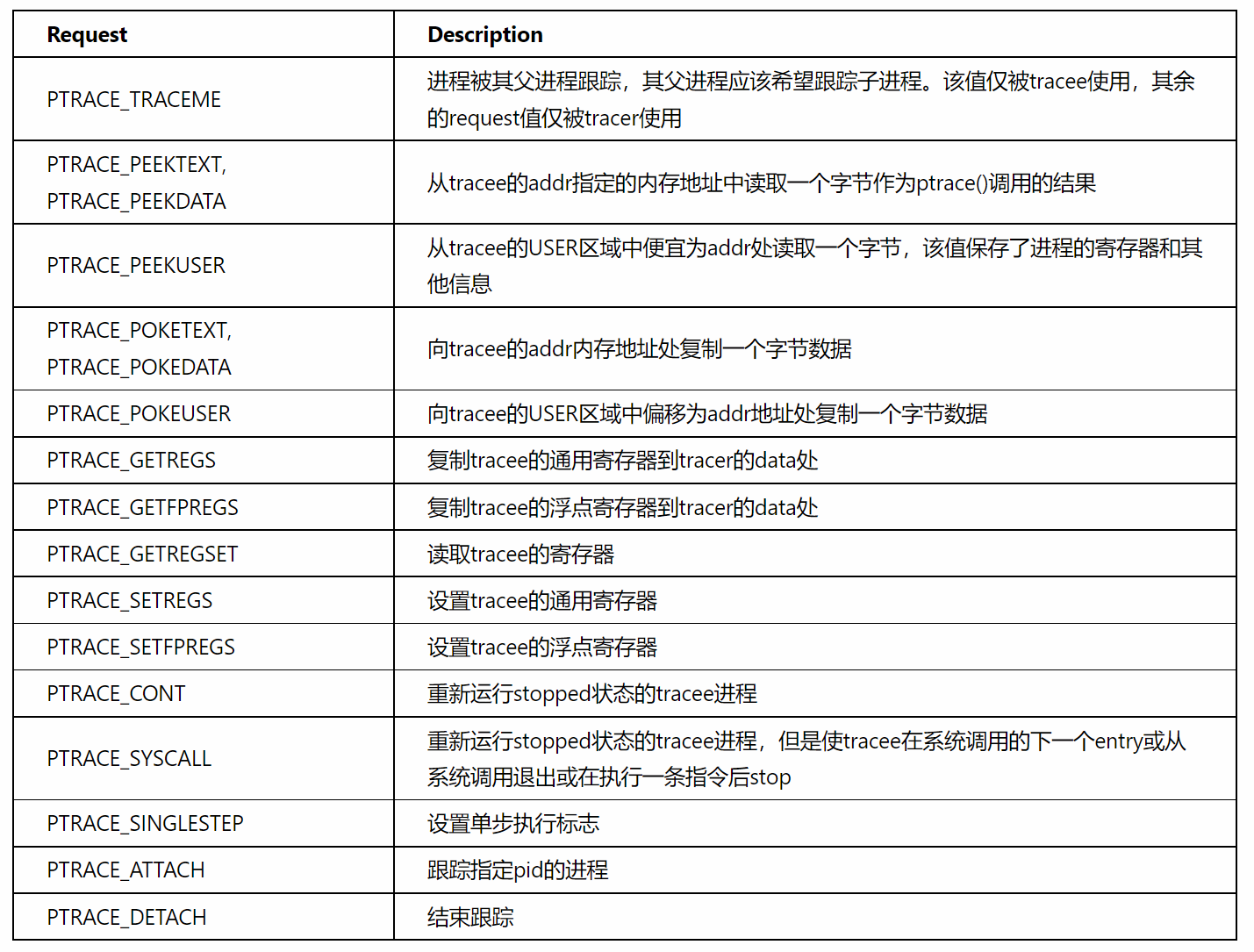
进入sub_44B360:
1 | |
分析发现这个函数就是父进程等待子进程,接收子进程信号
所以我们改变函数名称后
如图
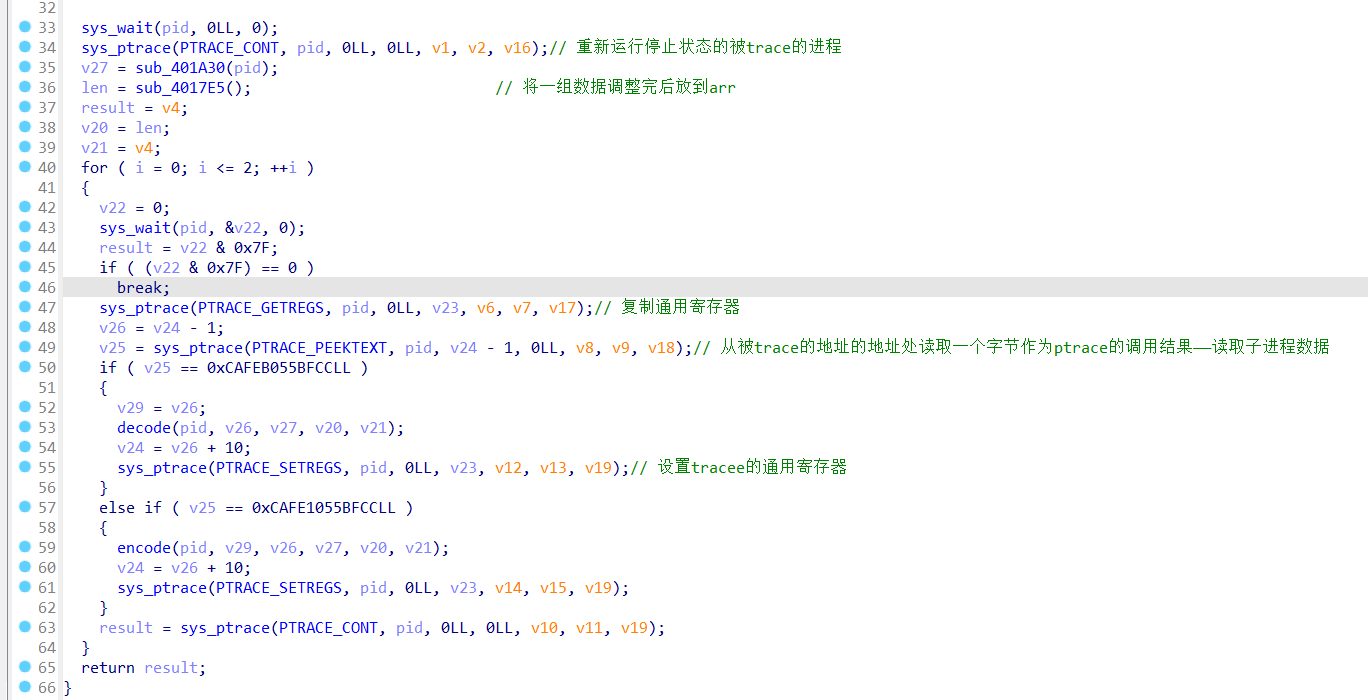
在sub_4017E5中
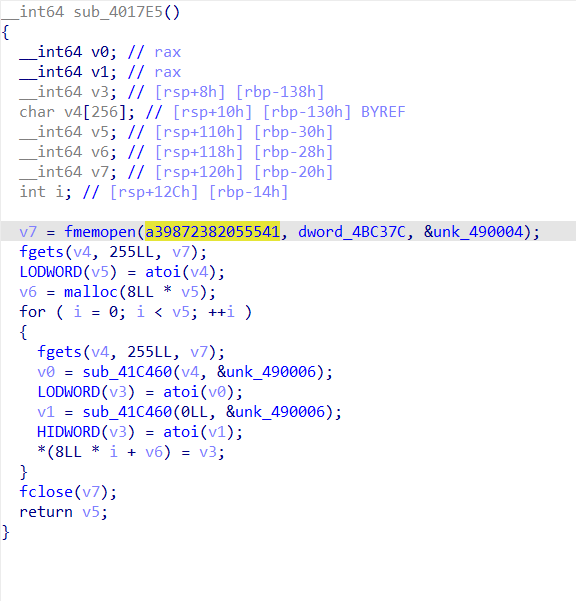
我们会发现很多很奇怪的数据,分析这个函数就是在提取下面的数据
退出继续看
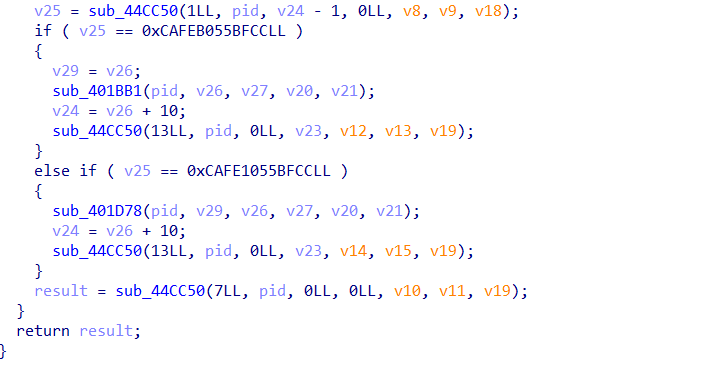
发现v25处的比较数据看上去有点奇怪
我们去提取出来的ELF中找找
可以分别在21F9的开头处和结尾处看到使用mov将刚刚上面提到的两个值赋值到寄存器,所以我们可以推断v24-1返回地址处的值v25即为此处值
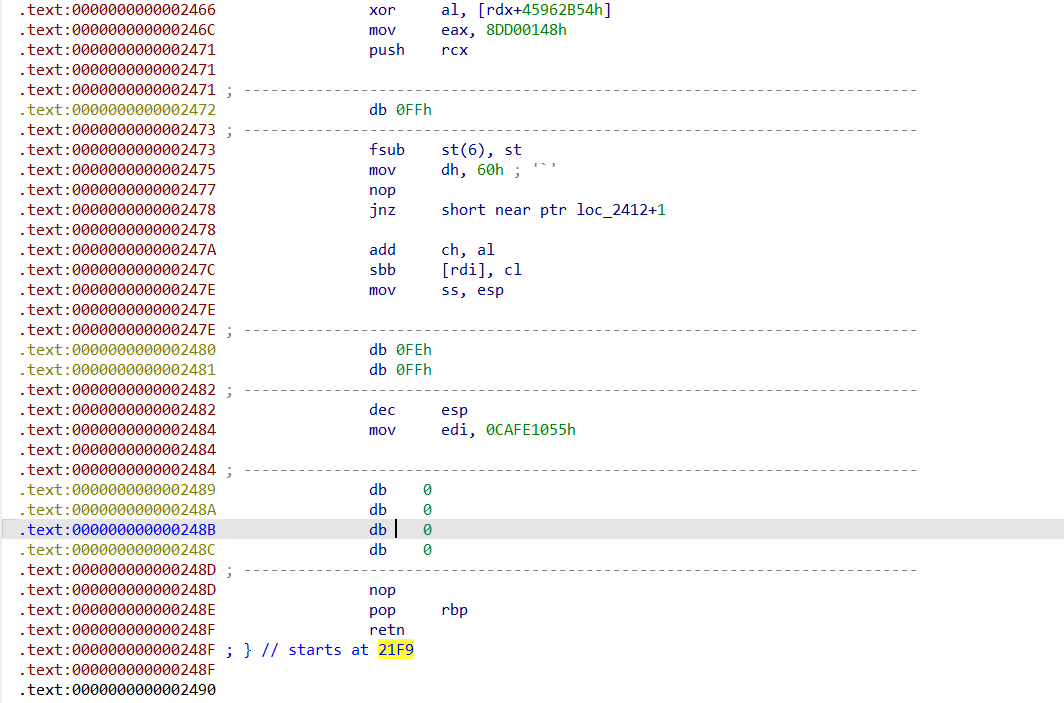
在调试过程中,发现arr处为8723,与刚刚在函数中提取到的奇怪数据是一样的
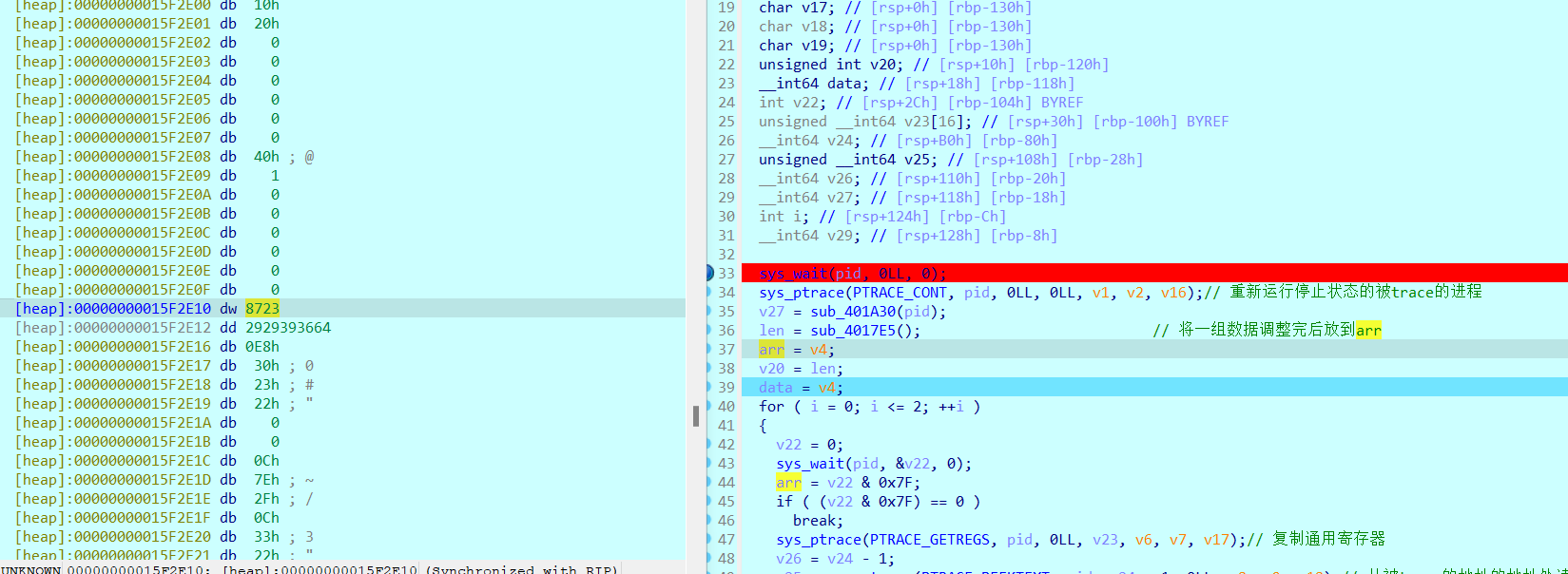
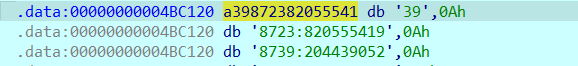
h进行十六进制的转换,发现是2213
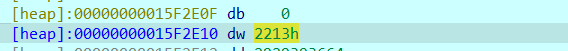
刚好于与re3中mov 后的地址是吻合的,所以我们猜测其实刚刚奇怪数据的地方是在传入子进程里面的对应地址的数据
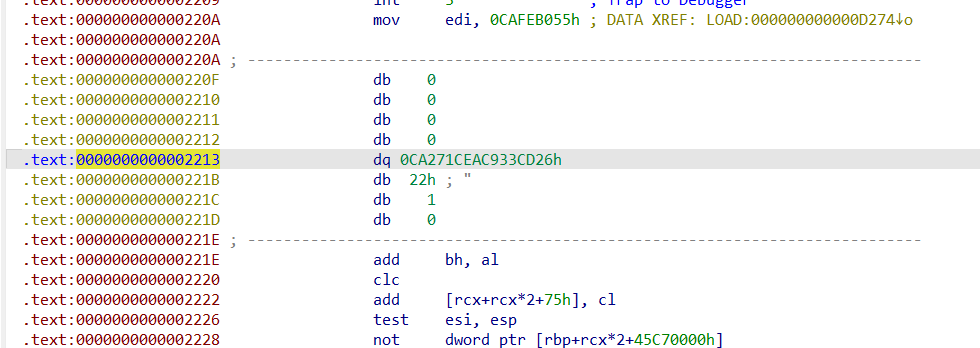
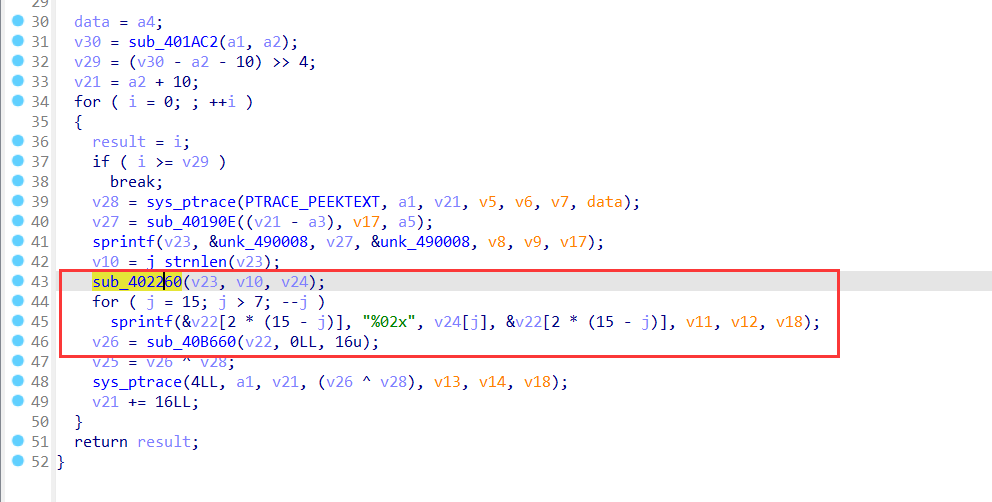
在解密函数里面,根据PTRACE_PEEKTEXT的性质我们知道v28就是我们最后需要获取的解密数据
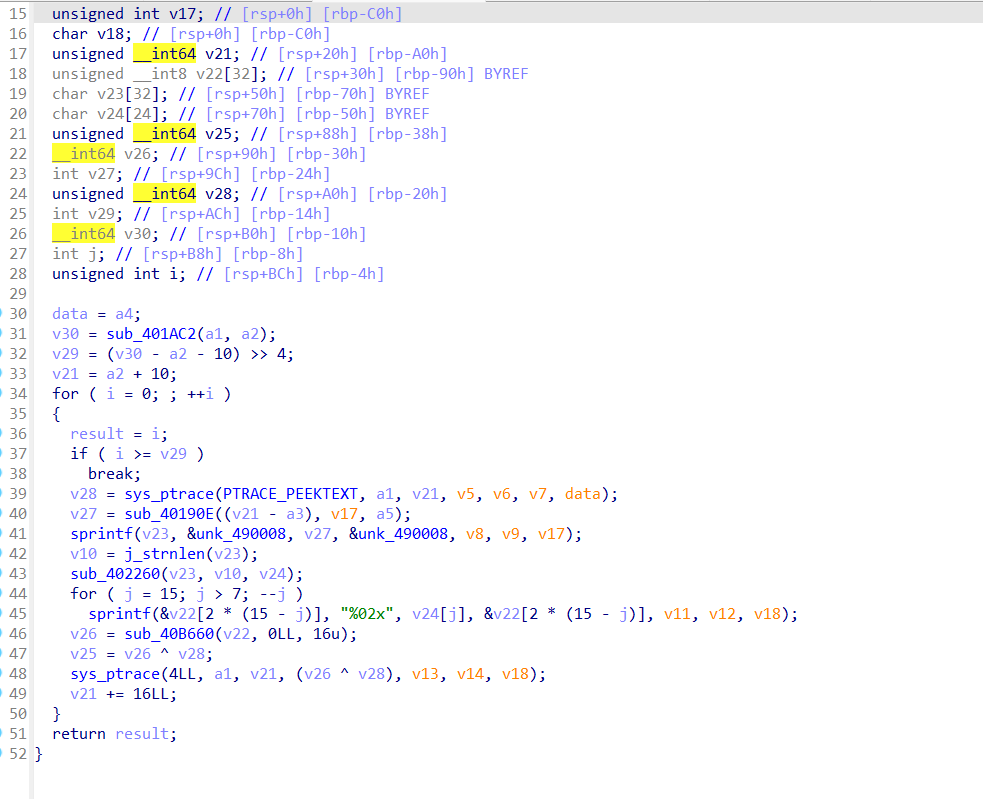
那么其实分析下来最后程序的逻辑就是
父进程等待子进程运行,然后子进程中通过int 3进行切换到主程序中的判断语句,然后通过Mov xxx赋值来进行先解密运行完成后再加密回去的操作。而v28经过调试其实可以发现是最开始的奇怪数据中的后半部分解密函数后经过
处理后得到的数据
使用idapython打印即可
1 | |
但貌似不大行,试了很多次,后面才知道进入解密处的时候调试是需要传入参数的
也可以解密后直接去最开始的地方提取数据
获得:
xorKey = {8723: 2533025110152939745, 8739: 5590097037203163468, 8755: 17414346542877855401, 8771: 17520503086133755340, 8787: 12492599841064285544, 8803: 12384833368350302160, 8819: 11956541642520230699, 8835: 12628929057681570616, 8851: 910654967627959011, 8867: 5684234031469876551, 8883: 6000358478182005051, 8899: 3341586462889168127, 8915: 11094889238442167020, 8931: 17237527861538956365, 8947: 17178915143649401084, 8963: 11176844209899222046, 8979: 18079493192679046363, 8995: 7090159446630928781, 9011: 863094436381699168, 9027: 6906972144372600884, 9043: 16780793948225765908, 9059: 7086655467811962655, 9075: 13977154540038163446, 9091: 7066662532691991888, 9107: 15157921356638311270, 9123: 12585839823593393444, 9139: 1360651393631625694, 9155: 2139328426318955142, 9171: 2478274715212481947, 9187: 12876028885252459748, 9203: 18132176846268847269, 9219: 17242441603067001509, 9235: 8492111998925944081, 9251: 14679986489201789069, 9267: 13188777131396593592, 9283: 5298970373130621883, 9299: 525902164359904478, 9315: 2117701741234018776, 9331: 9158760851580517972}
addr = 0x2213
while True:
data = get_qword(addr)
key = xorKey[addr]
dec = data ^ key
idc.patch_qword(addr, dec)
addr += 16
将上面脚本放到re3里面运行,运行后去除一些0和int 3
1 | |
根据搜索得知这个是数织,先盲用上面的两个数组数据去在线网站盲试,结果不行
所以我们的思路是去看看哪里对这个进行了修改,前往init段和preinit段,修复一下函数
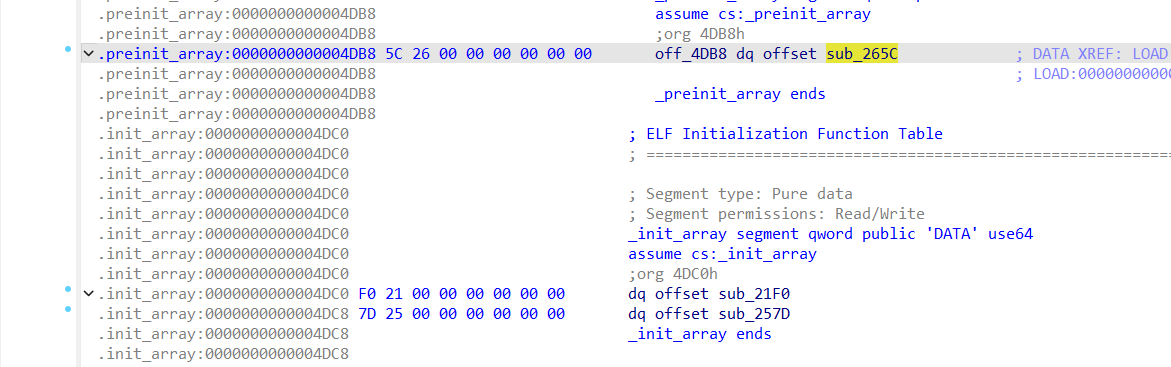
char *sub_265C()
{
unsigned int v0; // eax
char *result; // rax
char v2[639]; // [rsp+0h] [rbp-300h] BYREF
char needle[2]; // [rsp+27Fh] [rbp-81h] BYREF
char v4; // [rsp+281h] [rbp-7Fh]
char v5[4]; // [rsp+282h] [rbp-7Eh] BYREF
__int16 v6; // [rsp+286h] [rbp-7Ah]
char v7[4]; // [rsp+288h] [rbp-78h] BYREF
__int16 v8; // [rsp+28Ch] [rbp-74h]
char v9[2]; // [rsp+28Eh] [rbp-72h] BYREF
char v10; // [rsp+290h] [rbp-70h]
char format[8]; // [rsp+291h] [rbp-6Fh] BYREF
int v12; // [rsp+299h] [rbp-67h]
__int16 v13; // [rsp+29Dh] [rbp-63h]
char v14; // [rsp+29Fh] [rbp-61h]
char haystack[16]; // [rsp+2A0h] [rbp-60h] BYREF
char s[32]; // [rsp+2B0h] [rbp-50h] BYREF
__int64 v17; // [rsp+2D0h] [rbp-30h]
int v18; // [rsp+2DCh] [rbp-24h]
FILE *stream; // [rsp+2E0h] [rbp-20h]
int ii; // [rsp+2E8h] [rbp-18h]
int n; // [rsp+2ECh] [rbp-14h]
int m; // [rsp+2F0h] [rbp-10h]
int k; // [rsp+2F4h] [rbp-Ch]
int j; // [rsp+2F8h] [rbp-8h]
int i; // [rsp+2FCh] [rbp-4h]
*(_QWORD *)format = 0xEAABA1EDE1FCFEA1LL;
v12 = -268763743;
v13 = -1030;
v14 = -3;
*(_WORD *)v9 = -5399;
v10 = -20;
*(_DWORD *)v7 = -268633374;
v8 = -5139;
*(_DWORD *)v5 = -268633347;
v6 = -5139;
*(_WORD *)needle = -5401;
v4 = -17;
for ( i = 0; i <= 14; ++i )
format[i] ^= 0x8Eu;
for ( j = 0; j <= 2; ++j )
v9[j] ^= 0x8Eu;
for ( k = 0; k <= 5; ++k )
v7[k] ^= 0x8Eu;
for ( m = 0; m <= 5; ++m )
v5[m] ^= 0x8Eu;
for ( n = 0; n <= 5; ++n )
needle[n] ^= 0x8Eu;
v0 = getppid();
snprintf(s, 0x1EuLL, format, v0);
stream = fopen(s, “r”);
fgets(haystack, 16, stream);
fclose(stream);
result = (char *)(strstr(haystack, needle) || strstr(haystack, v9) || strstr(haystack, v7) || strstr(haystack, v5));
v18 = (int)result;
if ( !(_DWORD)result )
{
qmemcpy(v2, &unk_32A0, 0x271uLL);
result = (char *)&unk_5834 - 1940;
v17 = (__int64)&unk_5834 - 1940;
for ( ii = 0; ii <= 24; ++ii )
result = (char *)memcpy((void *)(25 * ii + v17), &v2[25 * ii], (unsigned __int8)v2[25 * ii] + 1);
}
return result;
}
__int64 sub_257D()
{
char v1[640]; // [rsp+0h] [rbp-290h] BYREF
__int64 v2; // [rsp+280h] [rbp-10h]
int i; // [rsp+28Ch] [rbp-4h]
qmemcpy(v1, &unk_3020, 0x271uLL);
v2 = (__int64)&unk_5838 - 1304;
for ( i = 0; i <= 24; ++i )
memcpy((void *)(25 * i + v2), &v1[25 * i], (unsigned __int8)v1[25 * i] + 1);
return nullsub_2();
}
可以看到上面两个函数的赋值操作,到&unk_32A0和&unk_3020,把它们dump出来,然后按每 25个数据取出非0的数字就可以了(第一个数据是显示当前有多少非0的数,也不需要),可以手搓
box1 = [0x05, 0x05, 0x05, 0x03, 0x01, 0x03, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x0A, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x07, 0x01, 0x01, 0x05,
0x01, 0x03, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x05, 0x01, 0x02, 0x04, 0x05, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x07, 0x05, 0x02, 0x01, 0x01, 0x01, 0x01, 0x01,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x05,
0x01, 0x01, 0x01, 0x01, 0x05, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x05, 0x01, 0x02, 0x06, 0x01, 0x03, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x07, 0x02, 0x02, 0x01, 0x01,
0x01, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x06, 0x02, 0x05, 0x01, 0x03, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x09, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x03,
0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x07, 0x02,
0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x04, 0x02, 0x05, 0x03, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x05, 0x03, 0x05, 0x01, 0x01, 0x01,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x08, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x06, 0x01, 0x01, 0x01, 0x03, 0x05, 0x05, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x06, 0x01, 0x03,
0x05, 0x01, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x03, 0x01, 0x01, 0x03, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x05, 0x05, 0x01, 0x02, 0x04, 0x01, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x04, 0x01, 0x01, 0x04, 0x03, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x05, 0x01, 0x01, 0x02, 0x04, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x03, 0x05, 0x04, 0x03,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x04, 0x02, 0x05, 0x04, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x05, 0x05, 0x03, 0x01, 0x01, 0x01, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x07,
0x01, 0x02, 0x01, 0x01, 0x01, 0x04, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x03, 0x01, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00]
box2 = [0x06, 0x05, 0x01, 0x03, 0x02, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x08, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x07, 0x03, 0x01, 0x03,
0x01, 0x04, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x08, 0x01, 0x01, 0x01, 0x02, 0x01, 0x01, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x07, 0x01, 0x04, 0x01, 0x03, 0x02, 0x01, 0x03,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x06, 0x04, 0x04, 0x04, 0x01, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x08, 0x01, 0x02, 0x02, 0x01,
0x02, 0x01, 0x02, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x08, 0x01, 0x01, 0x01, 0x01, 0x03, 0x04, 0x03, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x0A, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01,
0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x07, 0x03,
0x01, 0x03, 0x01, 0x04, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x02, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x06, 0x01, 0x01, 0x04, 0x01, 0x01,
0x04, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x07, 0x08, 0x01, 0x01, 0x01, 0x01, 0x02, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x08, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x04, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x0A, 0x02, 0x02,
0x01, 0x02, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x05, 0x02, 0x05, 0x01, 0x01, 0x03, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x06, 0x0C, 0x02, 0x01, 0x01, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x09, 0x02, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x07, 0x04, 0x07, 0x02,
0x01, 0x01, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x09, 0x01, 0x01, 0x02, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x02, 0x0C, 0x02, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x04,
0x01, 0x01, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x04, 0x04, 0x02, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00]
import binascii
import binhex
print(bytes.fromhex(hex(0xEAE7 ^ 0x8e8e)[2:]))
box1 = box1[:625]
print(box2 == box1)
import numpy
box1 = numpy.array(box1).reshape(25, 25)
box1 = numpy.array(box2).reshape(25, 25)
for x in box1:
t = x[1:]
print(“ “.join(map(hex, t)))
拿到在线网站上去试
Nonogram (handsomeone.github.io)
flag{I LOVE PLAY ctf_QWB 2022}
Ferris_proxy
分析题目可知题目意思应该是两个程序之间的通信被流量包所捕获,我们需要解密这个流量包找到其中的flag
前述:
wireshark可以捕获一般的网络数据包文件,例如cap,pcap,pcapng,pcap.gz这几种,前三种直接双击打开即可,最后一种拖入wireshark即可
打开后如下
我们可以根据
网络分析工具——WireShark的使用(超详细)-CSDN博客中
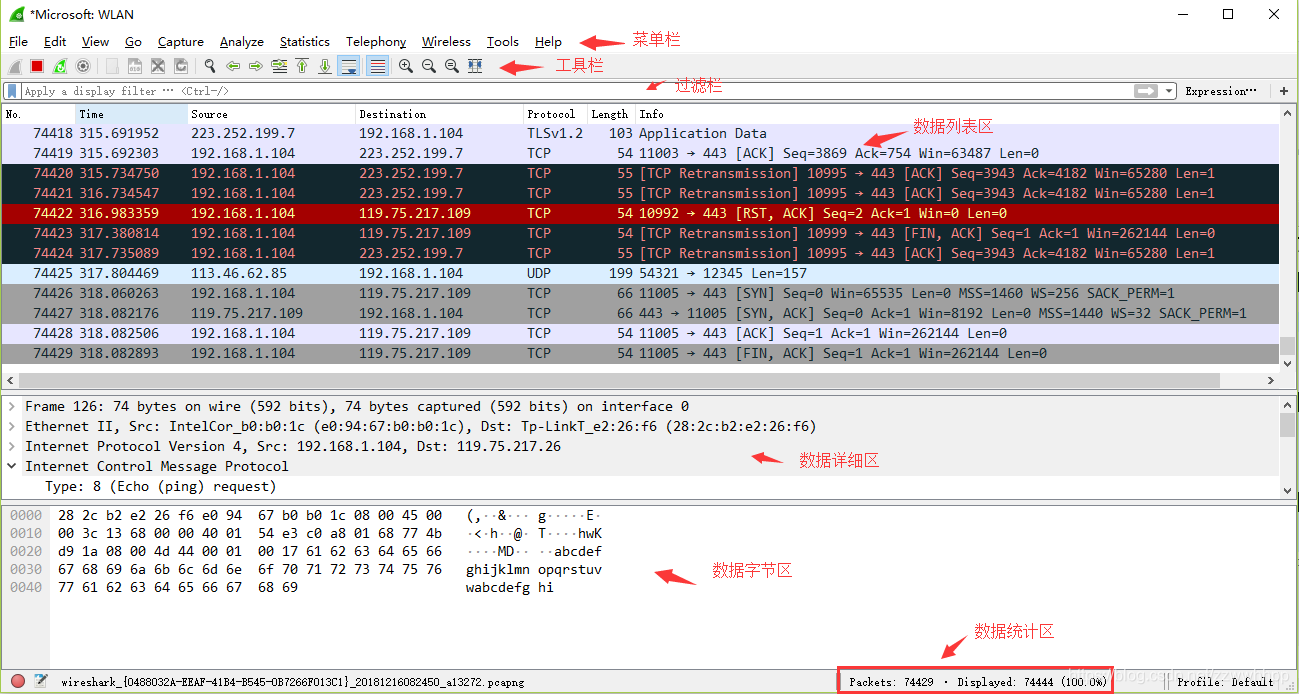
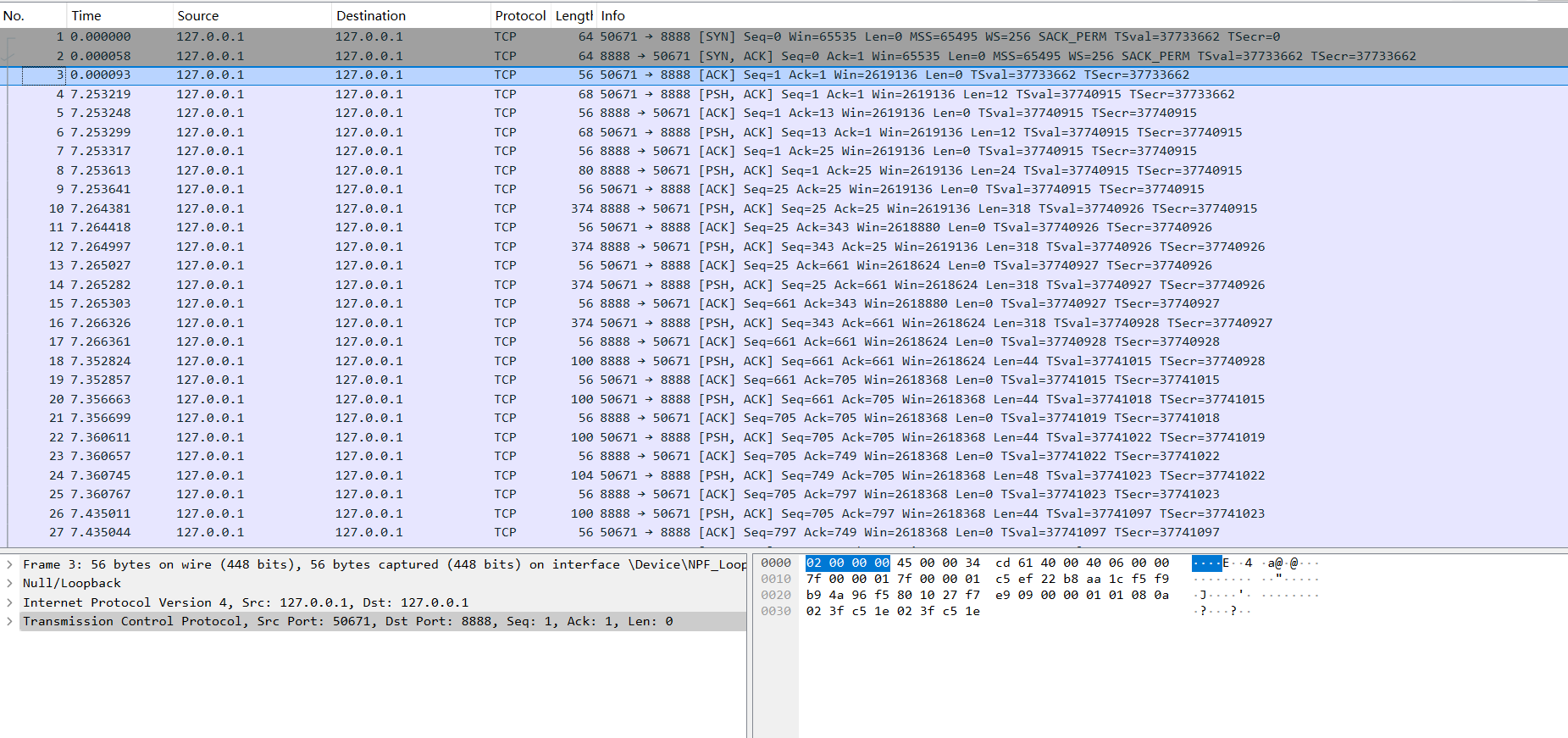
比对知道中间的为数据列表区域
下图中的框住的三行代表TCP的三次握手
过程分别为:
1.客户端发送一个SYN=1,ACK=0标志的数据包给服务端,请求进行连接
2.服务端收到请求并且允许连接的话,就会发送一个SYN=1,ACK=1标志的数据包给发送端,告诉它,可以通讯了,并且让客户端发送一个确认数据包
3.服务端发送一个SYN=0,ACK=1的数据包给客户端,告诉它连接已被确认,这就是第三次握手。TCP连接建立,开始通讯。
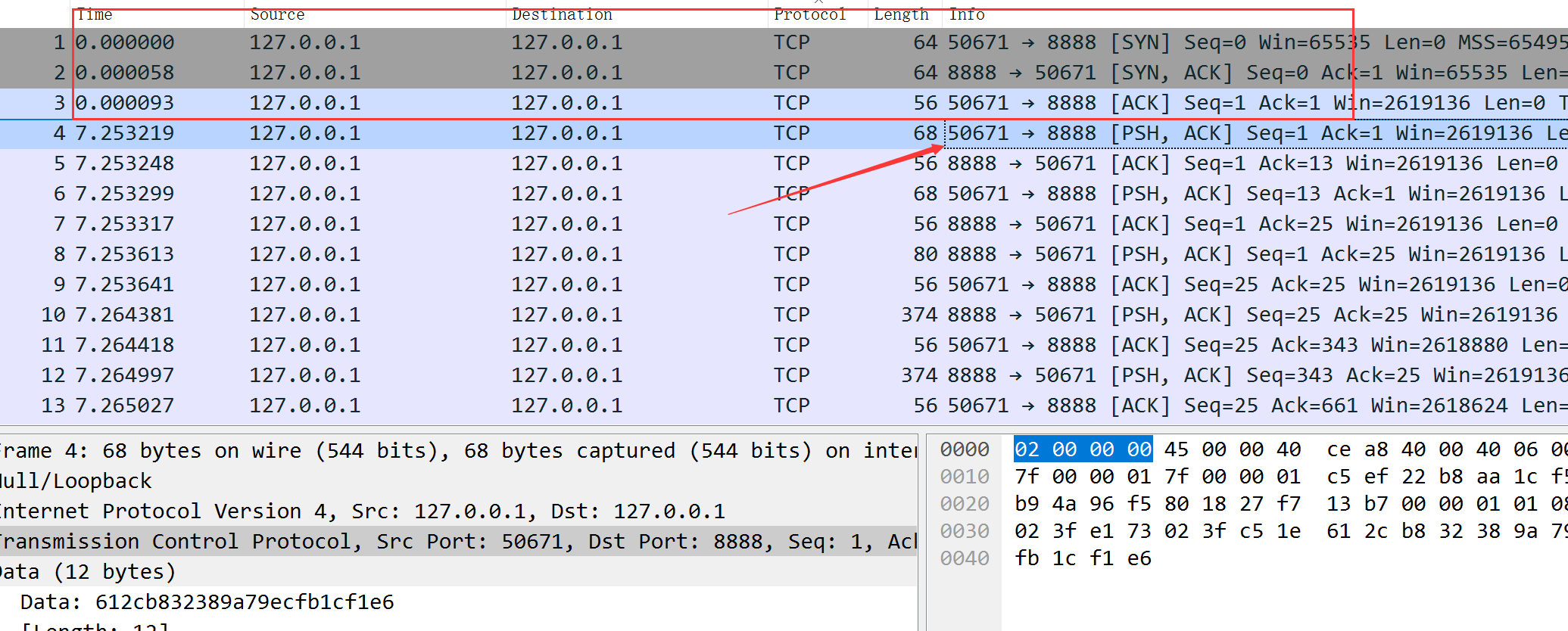
所以我们可以通过框出来的地方知道客户端(client)是50671,服务端(server)是8888
当然也可以使用strace命令对题目中的client进行查看,发现客户端的端口是8888
因为这里是客户端向服务端发送信息,所以我们的追踪过程应该是从本机端口50671到本机端口8888,data就在这么一个模式的数据包中,所有50671->8888的发送包下都有一个data数据,所以我们捕获发送数据
通过右键点击第三次握手,选择追踪流
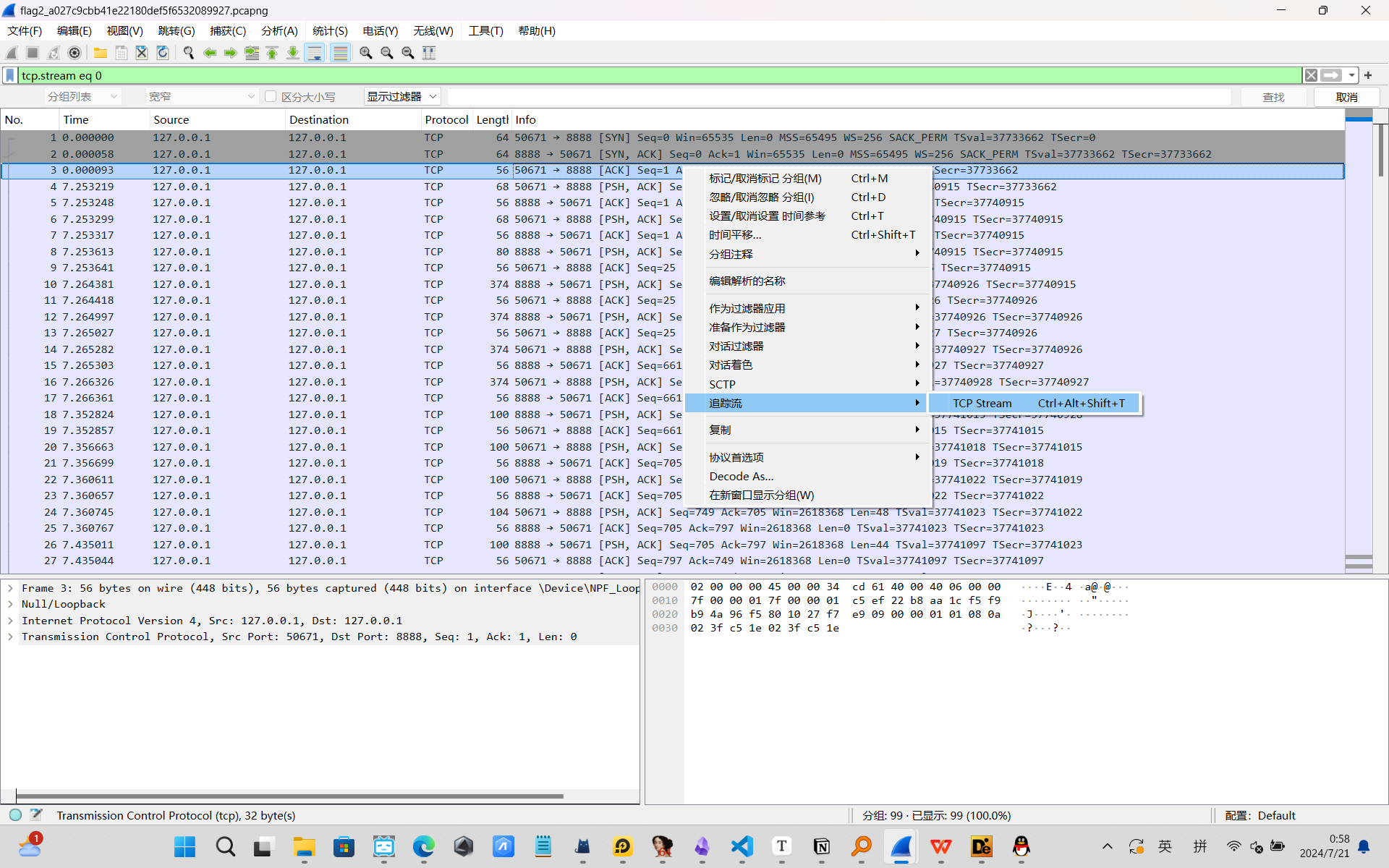
获取从客户端到服务端的数据
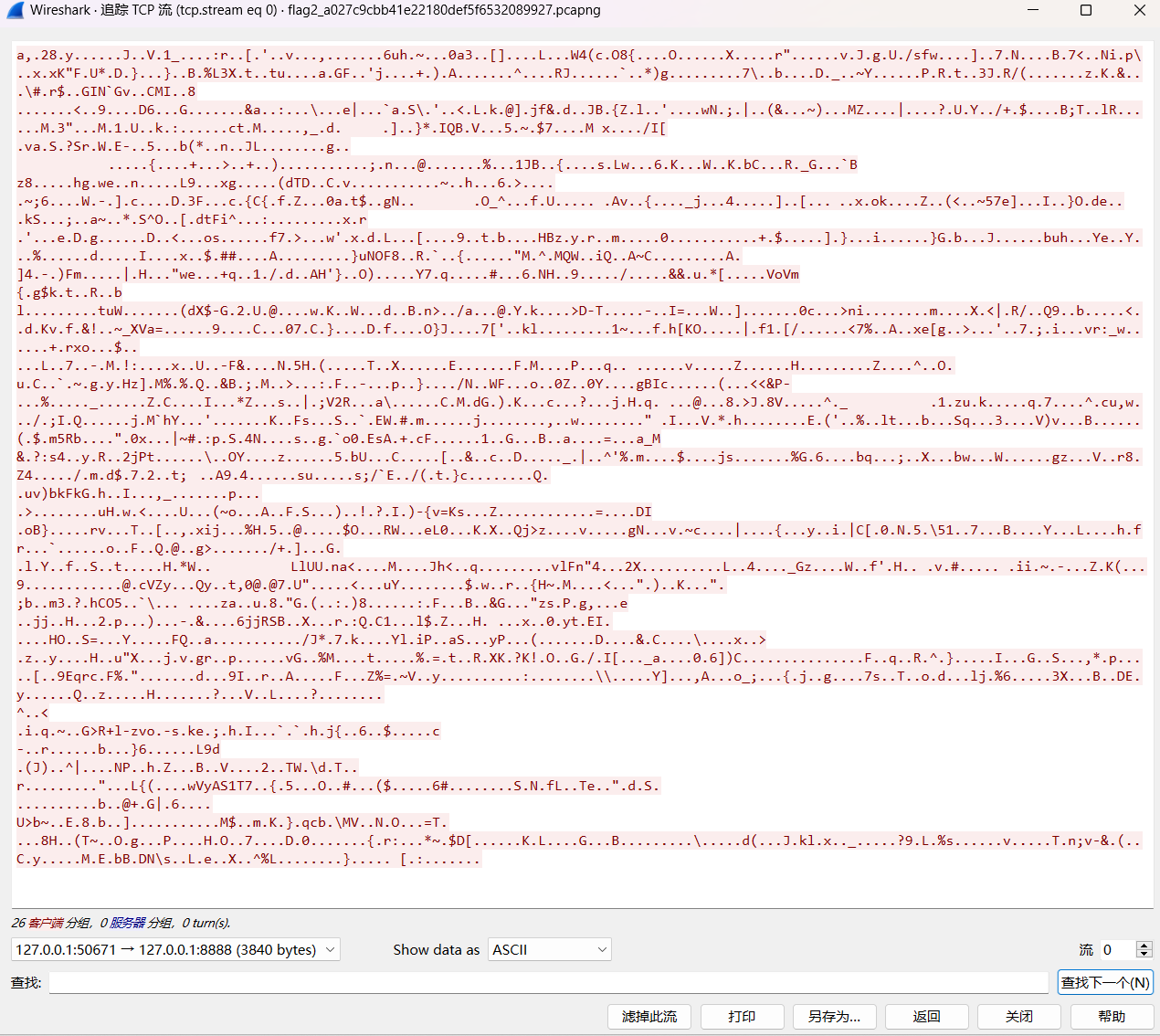
在下方选择原始数据形式后
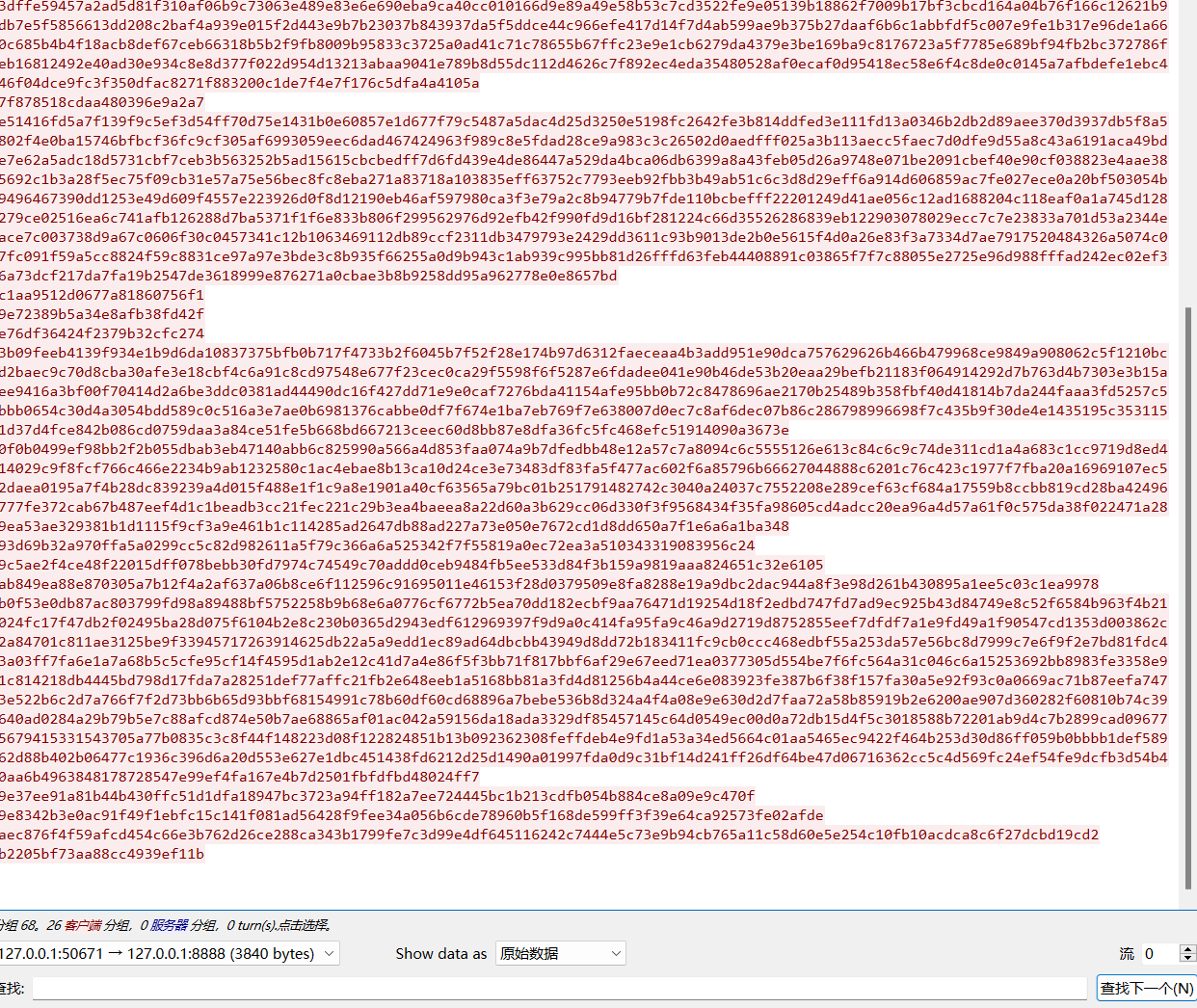
分析流量包
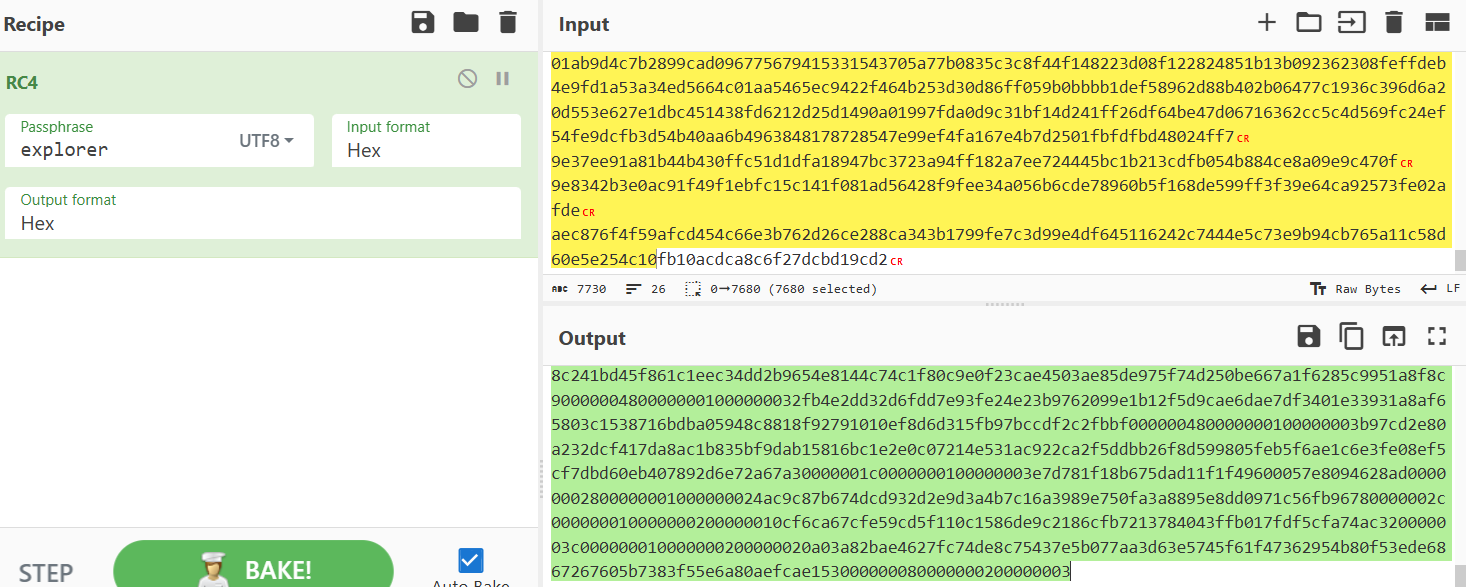
得到数据
1 | |
现在开始分析client程序
rust写的,嘶
shift +F12 走一波 ,最开始硬编码处点开也可以看到,

信息如下:
获得RSA公钥和私钥
—-BEGIN RSA PUBLIC KEY—–
MIIBCgKCAQEA231sNrX6WxlQpfsy8u6VR9rw4H4lY93fspAmXefjDhQhYCPM+SypBvIgb/w9f8AGkEwUlDQxfZCClz72GAuS9jrlsqg9LpSMZ+PJA
O0BDWisJCJtyyENW/9VVPpJLA0SSeYuTYJ84WDAcjsb0T++V97TXlSiq9svXt16LDxCQJjRXv9O1UTBkDpGGZmnR4xLiQT+Px6KOqAsrJcAF0EJa
ji5aBfHVQdrXQwgmq8PEsfnvp2iQCLZ2iDPLlGbRahdFeigXXT4L6UvjpbFr/9INvDb2+vQkRl7zlHVtUAMR4X5smW2nHHH5YyTi1cOvMFsN+oPG
xgBGpSqYCxmPwINwIDAQAB
—–END RSA PUBLIC KEY—–mkey:explorer
—-BEGIN PRIVATE KEY—–
MIIEvQIBADANBgkqhkiG9w0BAQEFASCBKcwggSjAgEAAoIBAQC93GDINPM6HX2NN3bCznyri2rDHDVcamzA/rPDXi9Mb2hu1Ypqek4km/kf4MKDsr
OU/3T5mcdx5kA80s7mBWlGaItg/sy6dsh2XOoKVEHcZYyrbSAbkYrT9CoLLMJlipbsalKenkW9JlHB0h+vwv/rAwXJ9IMSc4RQkvjn/QKuBPhcXf
rfaAIKNO0L+iqUL3asFM2CF8DXZXy8pLAxMy2PDJLtb0I/rXDWRImlBcIWBrhg7lDA0UxWXDD1i5MmMlvxmyho1F8Brh7ietK3XW7LWshD2ARID
gPoTZ7lZm7P9JbKSN+Uk7fay6LdkJXYszfT89Owmi7tmfUQ41fcBAgMBAAGCggEAWyGJru+Dg/Sd44t6peY4lVy3fO/GxRz+qHeTjojX2HAkppn
GHM96q3XWkWYHHu/Ets6n+msQOcIRldwx01QHp6yrJI/CJkkLrq6yjhfu1dTWlFK+XhsQQT/ZVq/GBdzBF+qdHLAGnV7ZmUCqVyIipGLqbPw4VC
2Ltr2kUBhlDySAA+gCnUrPyVi6O9OFcyDepKMy481gZLLijakINejYrsbdCInz2omHq12w/50tuf1s4XMWJN+A0g1Hx+tTk2jDX1Wqg/htmJhjG
qTj02GLJ/CJQjRodEdA7mx3HGwhisigeZgHTdPgP1B5Z9NXwUg9Qxln72D4mGhLCGYcw8VQKBgQD6+oltv1i44BO/ROUJkZPTLWeoBrxP2OOli4
aOSilLifeGrUQOSUtvcFHOxzy5RrhvX89f3GnklXcGyH XD03wg0/hqL0HM1EzNLmWkJW0Ng5WRFFgfcQIKbWBK9SHhAmKzkHtZPq6NwN8MbZUF
vndxDtcSOdH0/TbMtCMYYs0MswKBgQDBqM7QxWT6qebCU4YOV+5uwnP+hAunsWkvVW7pHgiPnZ8ARRZ9iFIqqiVRvKeeyZBEK22eOJNguz6Cqfz
2451D/AHA7sXht+1D9GCE/ebvUw+lPNQIRKkAgwQ8Dx+R6ikaUGzUKYhmWYJ5xgS9ZALZ+k4+rSjFg9jVjFjT7xQvewKBgHo9bJI3kE77VKLkO2
ndrdI9Wy9LmIyLZtVKj87d8B8Ko7TEz1DmAgfU/QNppvnWqB4W3DokcK8U3VRAbptidgLHG0ccnT/WZ1HIN1kroWHjpQV0kzc9I3FQtIXNvyKItu
oehPWCwiHovrqe5OZXTnWSdM47uzdH3Vj2o+FMvfJhAoGAQvusbTGZd8oEcvqIx7VKVy0TCdmKXnpSs3iNYDxvIZ2XPXSoDst0ACXRuq/SGm4FZ
E7RH4TaFP8u4+sAADVCVB16Tc1IzIXdnz+LkvRvSCAmrTSY8jMtcWvfrxZcCRBBH0TqH4guEZisNIp1YTySb+rP3YXvMEImYdalcsii5rkCgYEA
imnWJ5aFN3TDt3h76CL3nRQegnzekJBjXZfcrHdExkgNChWjiz+WU/FW/Z87xMxtfIEwwzzIQHxbKZhgzO/Up2eXdqH59DvauggbiS3h4p9k2kx
WTocztaRvdftMW0ncmA4yCKiUQEmWD784JCyxOupNNfr2rgViWggVBEtJUIg==
—–END PRIVATE KEY—–
在非对称加密中,公钥用于加密数据或验证签名,而私钥用于解密数据或生成签名
服务器通常会将其公钥公开给客户端,以便客户端使用该公钥加密需要发送给服务器的敏感信息。所以这个client程序的publickey应该是server的
开始调试,这里不得不说这个真的太难调了,很卡(),也去切换了wsl(最开始甚至还调试不了,瞎忙活半天配了个库后面终于能调了)
提一些关键步骤:
最终在return处被遣返退出调试
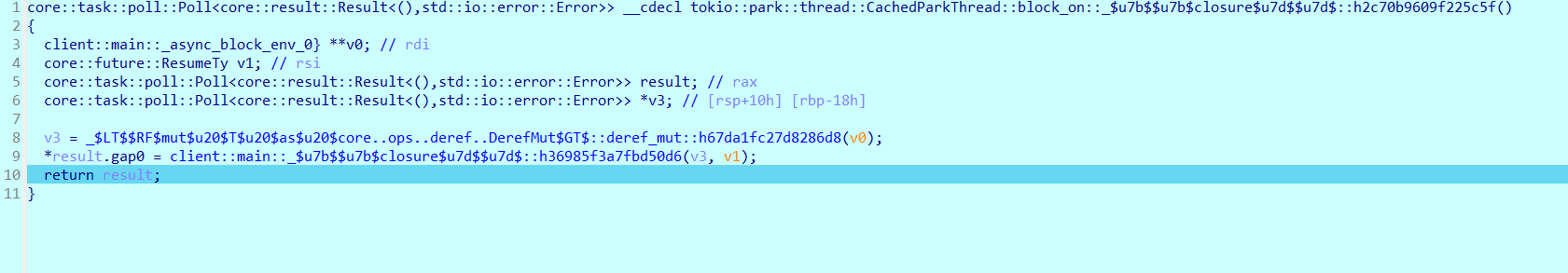
继续静态分析
监听端口,我们可以在这里找到accept函数

里面的connect处我们点开字符串发现这个地方是在连接端口
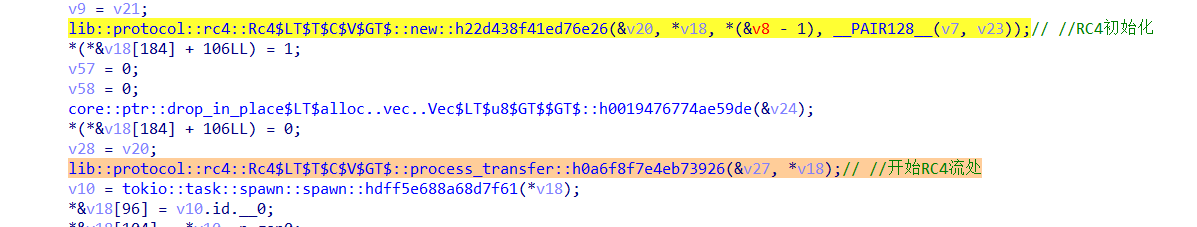
总结上面的流程就是前面部分的逻辑就是客户端连接127.0.0.1:8888端口,然后同时开启了RC4的流加密,此链路进行加密,然后开启监听12345端口(bind) ,等待连接(accept)
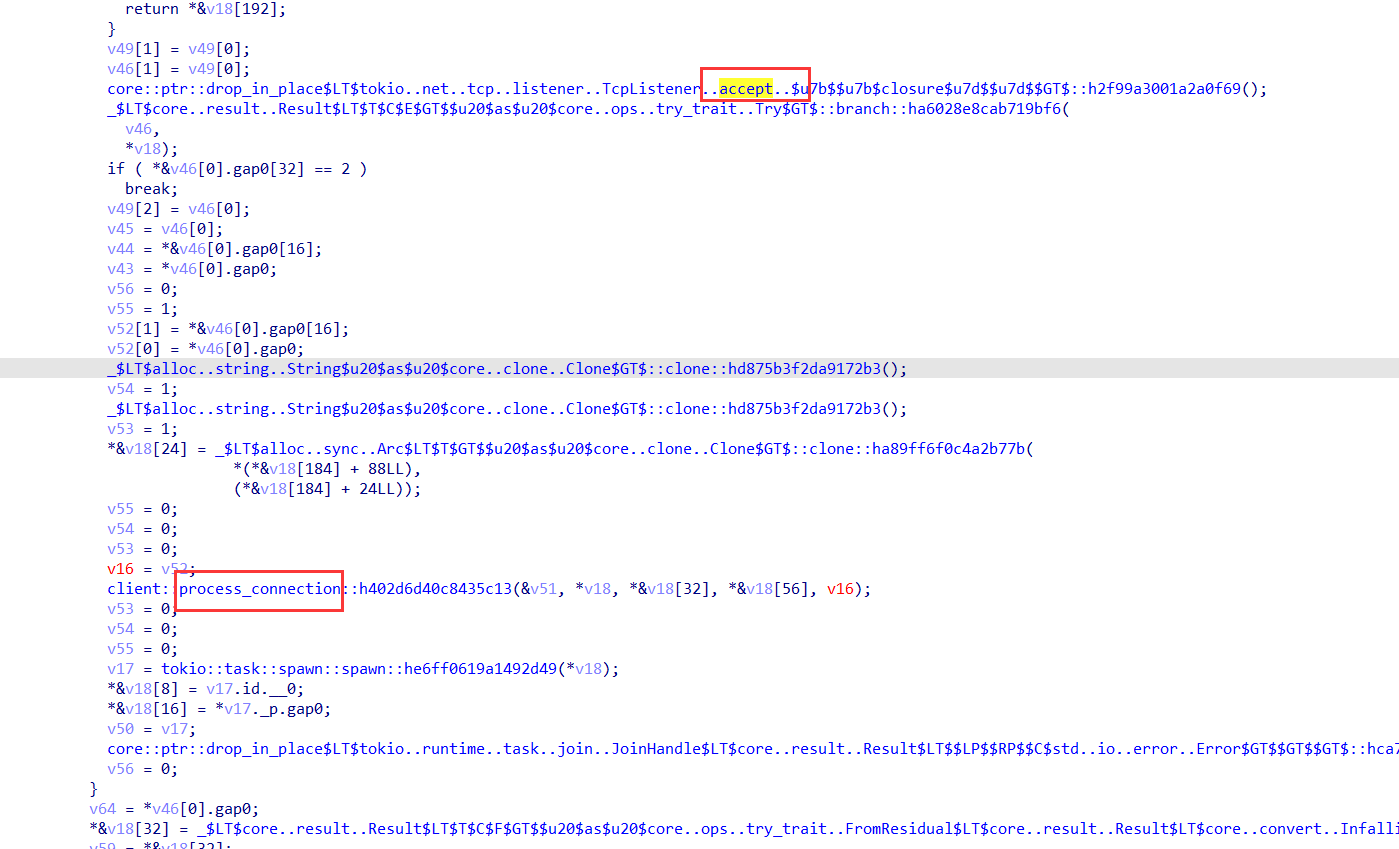
通过搜索我们可以知道 process_connection 负责接受来自客户端的连接请求,负责处理数据的发送和接收,例如读取客户端发送的数据并做出响应。
在这里我们可以看到key_exchange以及它上方的crypto的new函数,表示开启了新的加密算法
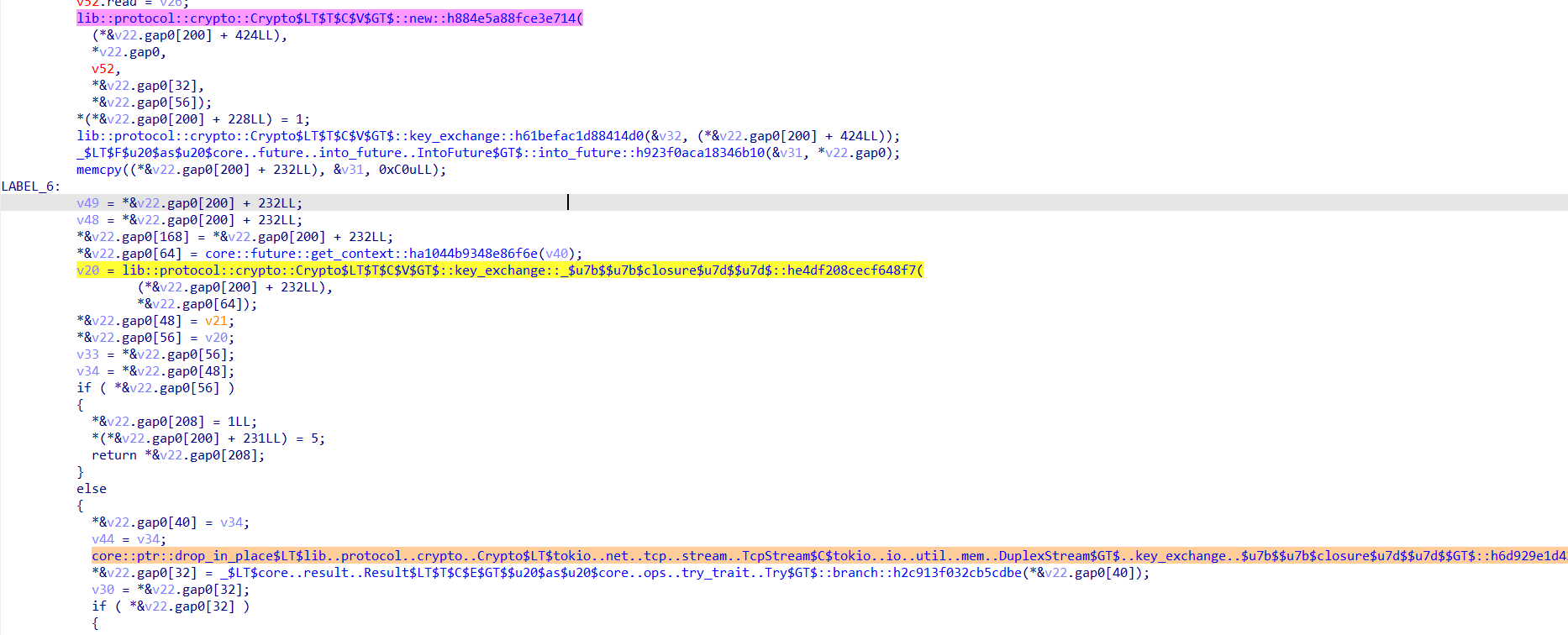
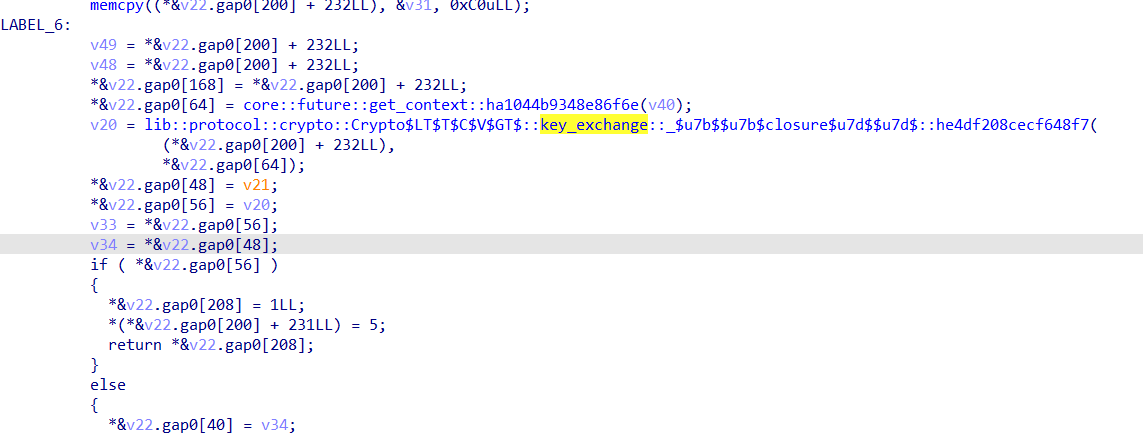
我们可以知道这个地方就是在检查密钥是否交换成功,点击进入
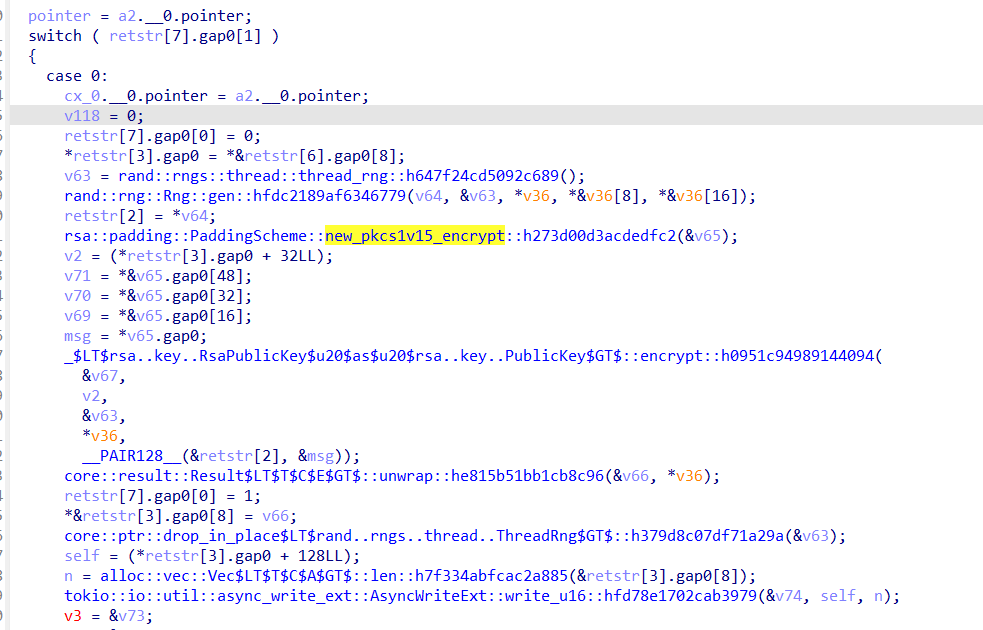
点开函数
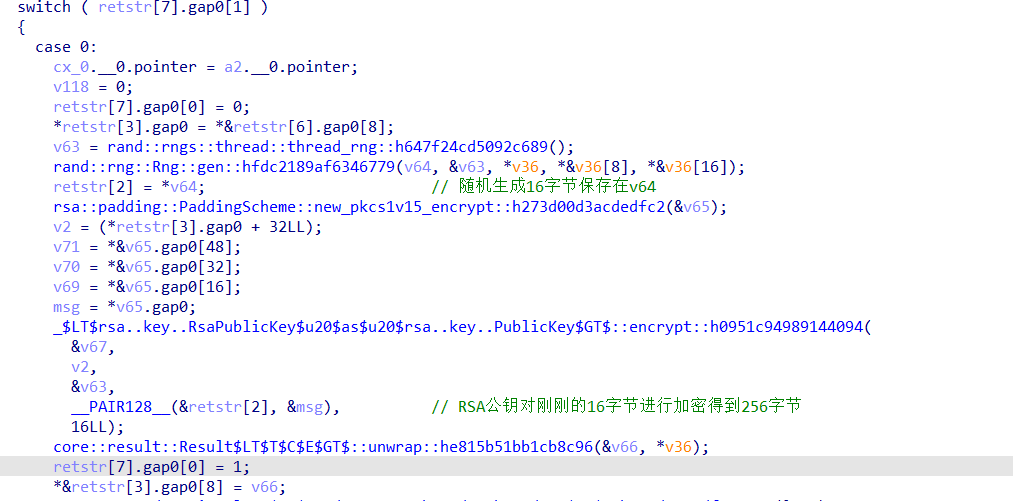
这里的主要逻辑是先随机生成字符串(v64)并保存到restr里面,然后再通过最开始我们获得的公钥进行RSA加密得到256字节发送给server
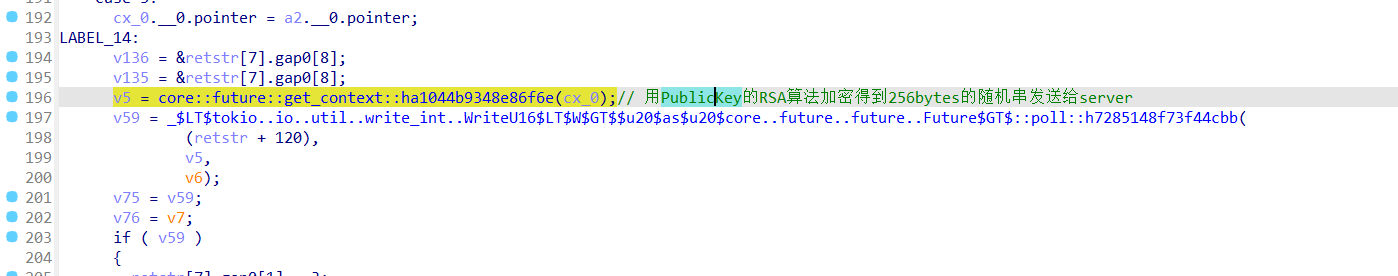
与此同时程序也读取server下发的16字节随机串通过公钥加密后的256字节,采用client的私钥对server发来的256字节进行解密,解密后字节存入v23中
然后使用前面client生成的16字节随机串和刚刚解密以后的server的随机串执行异或操作,得到新的密钥
然后我们对刚刚生成的新的密钥进行sha256并且将结果发送给server
最后进行比较
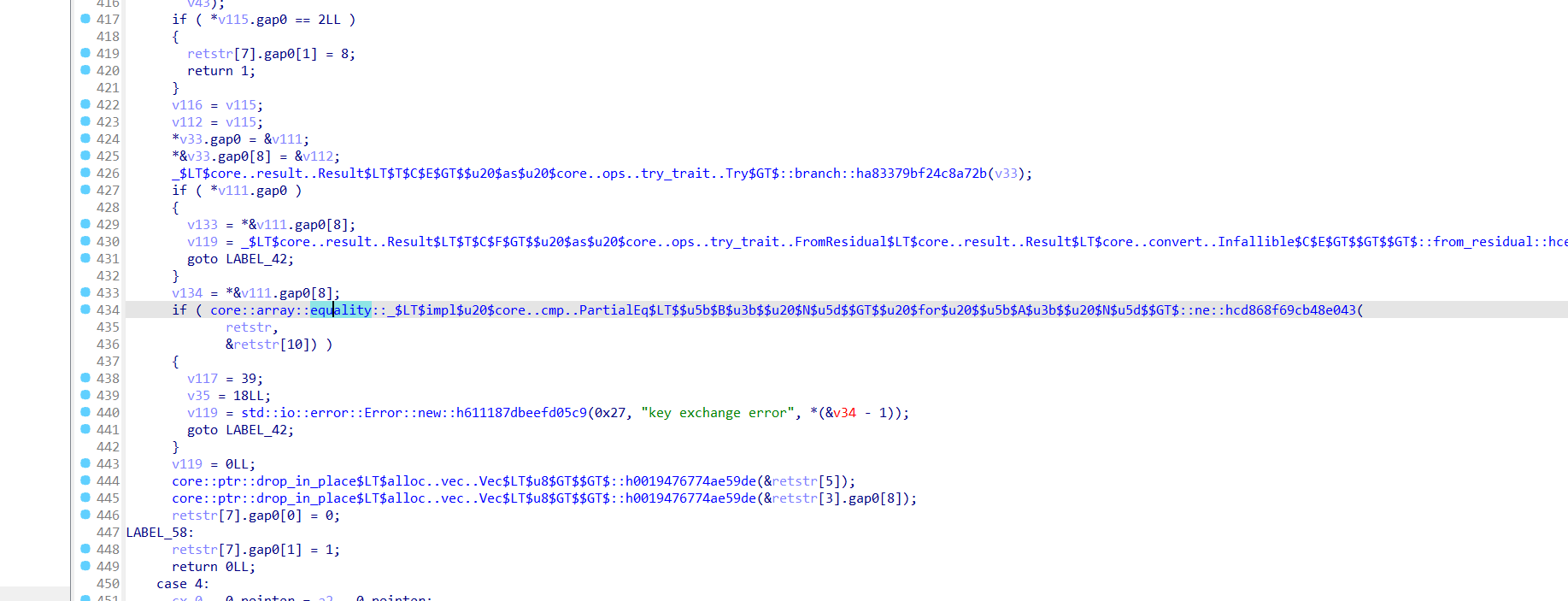
然后看到process_data_dec_in函数
发现AES—CBC,读取内容放入下面
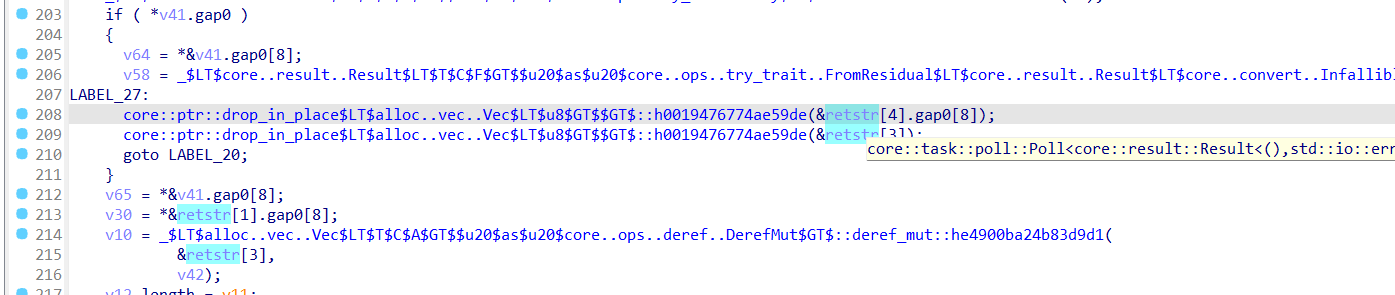
最终解密函数
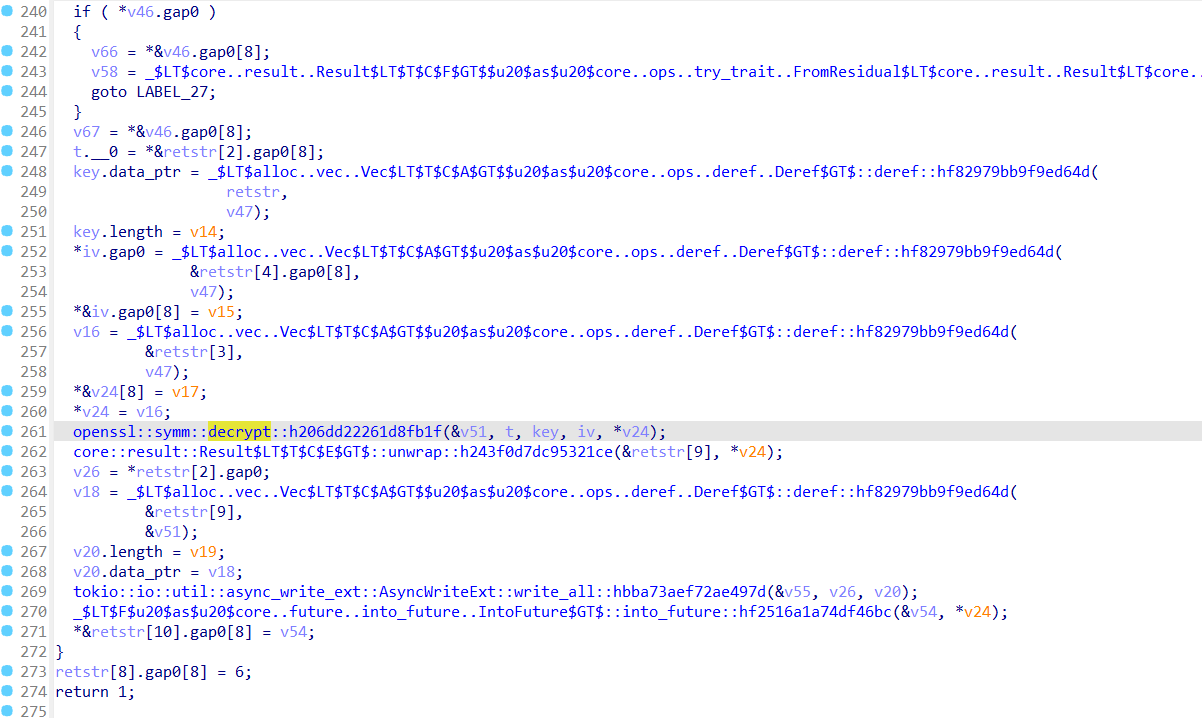
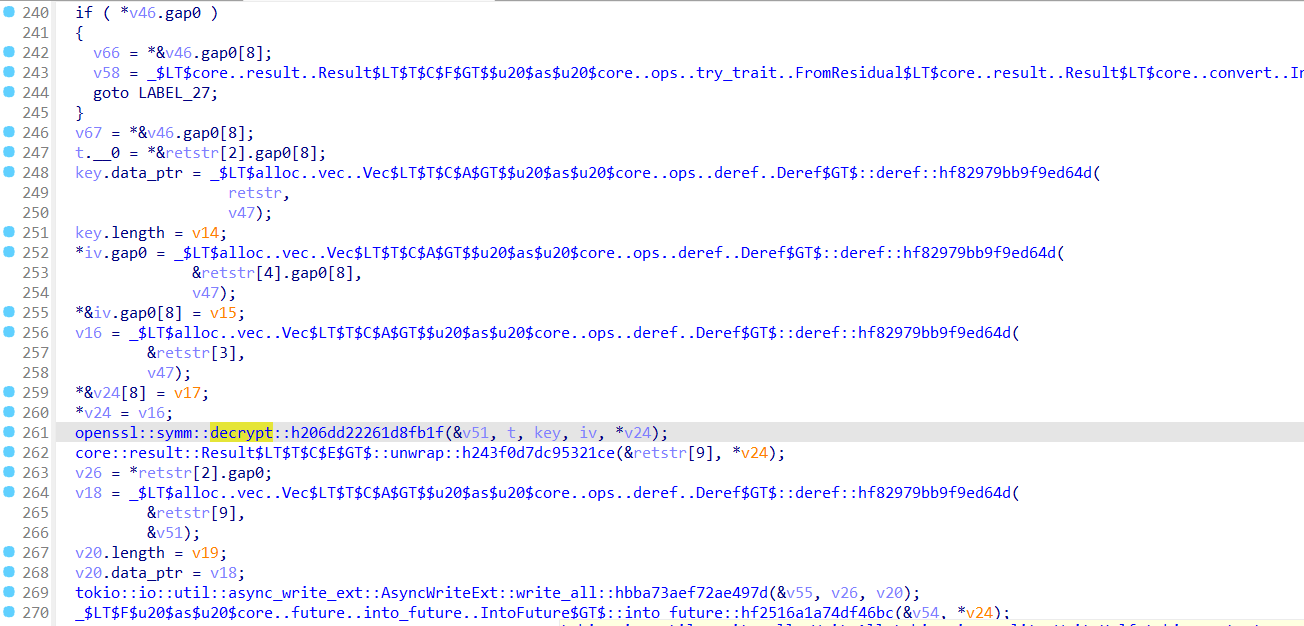
进行RC4解密后
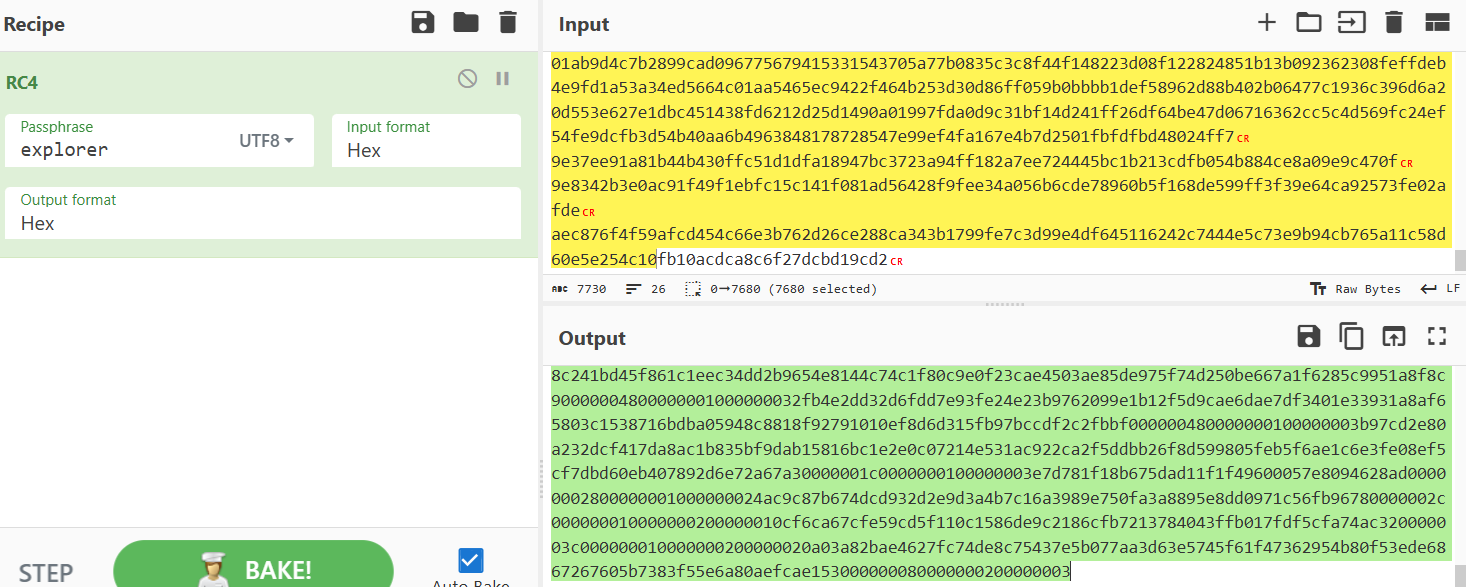
获得数据
00000008000000000000000000000008000000000000000100000048000000010000000001001db2ee547837c2b0394f9316a3c672109c854769d9627ce715aa82ae76af4fc7d468903ffa4f7c9d4afcf139528ceb24cb5f64a192287282ee7fd076992f000000480000000100000000e73f0a730b98e032e90afaf73b8ddab1e821432c3e1c2c51396914f53fb304f26cbc8f85ec68462ff85dfb0979648d43003291ccb9418e7b4016f5d3325d4083000000480000000100000000d44c5aff410f28c841fb51c2e982244d7f7370fb6b73d6e5caba56c1b4b8f96bea190aa8d66e7e37d76fe2e5fef7f78b0de90e12eefda3a36177583412ca074e00000048000000010000000096a1796af867e440a72ee81e36e05f3b73c3341f6166b804bf83c3d0b47df74cc77405595ce44d3ccfb739496b8acb78fdb02bcd510851b3e3de015fc06eadb40000000a00000001000000000f8e0000004800000001000000010100320b119809b793abf357a7f78b0742ee93a957e563a5a94fdb09804e89596f2597a2cb9ae9f5161d5fda88ff050e47b1d28bebc6563465d2e7959e8a624a000000480000000100000001cd39b2053c17021f93030e3b9bc7149ff5423faf64693932f76a8dbffa526fff7c076845b1d31967efca0b56b066e8bacedc1927e629c6d0e87f61bf14ee3039000000480000000100000001053d668ef1855426257ce68cdbc2f66919a2f9efbcb632daa6170cb8246ab7a2348032f48cefdbc3aadcee6b9ab867371346bbe90fd69d213705ed1de38922b300000048000000010000000145bbbf8e0b10c5436e5974f46426d3efdbeaba819ea5d049bb420219a426336e14bc36e5753cb71fb21a2b78f699918a0045a8badddd69646ed65a59e17feec80000000a0000000100000001b30c000000280000000100000001503fdd267309866142ae96b3197515b72ccd766dedbc09d61c25f0c3fa79ebd40000002800000001000000002accc966ccaf48a147471171fb9589c95c561100d6548ad979f328e43bcfe0750000002c00000001000000000000001023a5457e1fa2e2f4a23242b1e61a597d1458bee4871e6f44e9296820014728300000002c000000010000000100000010bd688bc8657972730f1d9a5c340cd555602957fa44cf643423bb23734bf8490b0000003c000000010000000000000020a6f95ec809bac678aa1f4a74a0094e00d33e42da057331c95a61c6b5c3cd24daefeb367e01d3765e91643e37e2ac95e90000003c000000010000000100000020184ff5940c47e4fc42a2bd1f61b304f5fdfc5e453104a3946d06c4897a86f7d2872c948ff06b270b4d024446df8b60fa0000004800000001000000000000020044f4cf64a905e470a2d8091e5320c0b8a370193fe44728340c454361c84578f3b469963d12fa608ab96bf2e8c9c2116010d50e151b6407308d3cb6a2000000480000000100000000bc02026a76b5be1d66cf03d90ea5303a5091b48d370ac186402138606da35c90fe7efb0a21f0a177896f496ba40f02e079b82218be0124ab7de5d4f48cfd921e000000480000000100000000323d2847d03880fa5cb48533939141115c3dc15fa32a82be59d78826e3d37f5cac12010ce10c850df63626f94657a5beacf7d502b59fc10f571959ce6101b8d6000000480000000100000000704e541c930ca3a8d156d7f6122fda7bbdffed9b9bc6160f4ec8ace48978bd458869a636a7d8798d7dbd503e0c41aad82496578df4fbffbd3c5c885dc0bd3dee0000004800000001000000006d6af1efc82365f1619286e7a612155d87038f4ccb39e25e0660f9f2d320ae4321996b69187ba68abdf3e6ab41abfa2dd359c7eaa5d344fc1acb97b58dd44d86000000480000000100000000d444d17c165ee78e1d55f5c42b1f1bcf9c0f302588b68d26d2a308250c42d1df13be07693aa0f42cefcb9dc1688216478a1a041c9a0c66308b3e4a5135fd2f0f0000004800000001000000002c7d9df81c7c9ccb7422089f94c0fa54067e6c4fc634c725c9aa9710aaedd671f72cf9287f38de6111ace6c0c32ed568569b45743abfc519e23aabccdf30a9af000000480000000100000000d1bbcab1224daf8ccfb5e6dbf42ee924935b990eee7abe70ac5537426236e0ff1b2ac4748c665d3aba61c4685798ae62126d89220cd5ae8c6a7c32e33ce1236d0000001c0000000100000000b802088e5e303c8389880c09c3925053cc210825000000080000000200000000000000480000000100000001000001d06fe6d3c4b7761ffea3dea5ca1b75305f3bd828925e041baabc00aa51f93e5d59aa6c5c024e1de93ccabbcc7736271de03665a2b170a42faca2e869980000004800000001000000016c6b50fecd4e0e1a9ca070fafa04c06a12f27af94d5430ccce129ada67c3040d444b772758195366025267bfea9e35cbaaf816022b34755d5ac2a4d7df857732000000480000000100000001ede0bf60b0ca23f40635dcbda76eaf3b59faa140dee0b2480aacd8df765ba5cfd1347f22c9415006210eb4f224332b5cfcac7be98e0da94f74693d8af22e1fad0000004800000001000000010614feada5c2aa494e61a0b2a848b82833860d6c1213c4aceebcbe55f419403ecd843835f14f2caa8310be6bfad7ad2054df500a54268b17530183ef4c49f1c50000004800000001000000011ed33f223e632356012a42484c1241d41ec5426ba94c0c4887a8206b86b41ac73ca8b79d90256d391190bcb2256e881642c5a0fbc178691cf9ec983e1f1db4000000004800000001000000012c5043530d28ce81e89c0a71baeb821ff0240d18fbac0e01b0952bb62b91354597b9061dc440318ce3eabd95742607546c414ebf3da32879b2af3500d08cb4e9000000480000000100000001b404a5293b85aadaa3d595d38992c219ddd7a4e5f00c09af477eea99477b3d53ac6b67c49f0cbd5a7ff038904dfc1a3b58cabe2c25dcb86fa55a53f3d362f0510000002c000000010000000128bf591667dcd1d600abe1db48f49b17a5ad9d5650f7793af7a24341b771a9247f1eb4800000000800000002000000010000000800000000000000020000000800000000000000030000004800000001000000030100abcf924576de63087c8695ccda3705e8670c770f2bfda1dafdeddcd09b2aa6d485c6a87ff31c14300ddb660576ceed52047318a30d3c05c9848b0a1fb05300000048000000010000000387d378e9cbb8914e496a633595c7f68da097afd4fbd0380b4eafe790ffe999b81ceeff32eea4d8fa4279606c7c491ec4eb4a7ef5bf614307c21bd3a314db9d2e000000480000000100000003e9f505f08c464e1f5f123bcc180305bb5a30f2c382493a1cc6d6e5e189e75950f75c8a790aef2c1fae18436c9d6f4840a9eacbf04139a2b25042c27f3a3fd756000000480000000100000003faeaff92d731e354d03dc46cbe8a001188dde35e753c259de359181678d94e47d90709345f6c9975288dbecfe1a6cf2eb7a14978854bbc73d3ac7d0a72cc3ef40000000a0000000100000003c41a0000004800000001000000020100d92f41b75bb8ced6be2fbbc0ba1cfeeebdf15826ce92ba78ef4cd0f6d47ff04e9e593cfc5fc7eac8109effce7e75f547873ab559186885edf0e519f73aed00000048000000010000000243421e08dea79fd12889b2845ca365803bb4aa23c50d0c298e6649121b6d9101f32d15a043ffdbc93e7665617fa7b4b3f01db76f5472c5aa3a085da5683efcc4000000480000000100000002bf9a240df9afc3596d4b3613ae9a2184340561c896a60cc577e6ca507b5e6548ccfcd8bccf27de73deaaf04fab707a20c6aa94febdf8a0a5532c0f4c73958e11000000480000000100000002fc1437567ccd886b5496cabb117993f31afe25f53d92721877892e472bf8bba1743b827e277f500d51b7f74f4682e943be0d3ebfdc30742e211dc3eba51dac8b0000000a00000001000000029074000000280000000100000003e836256016a5f8ca1e29732b7332d9776bdc6694a9df6c1172183f65916f83d50000002c000000010000000300000010f46cbf6896be858f5c2f86ee3c162359c545b1f5bd1eec0cd03e2b7bf9c1b4b90000003c000000010000000300000020c580aa8aad81a2800fadf74749e79c323da65a6d11e8fb517d60ba36a0113b345be7c0fce390fba664776b676d82fdbe000000480000000100000003000002002292a593b68fdbf615d43c123747cf1f1583619708368b471b4a37c8eed21e07d14a7bf309f45335592134c5cc7a18152de20bb7d2fb753bee9131d90000004800000001000000033076a9d57efa379e4f7f4700116d786c586b49523454dd9b3ae7cfde0416d9bfbb486eed31f88fec8128cd1e0bf783c8978c04fde5f1bbe67ecbe1c76e0596f5000000480000000100000003579bbdb311093c2a3bb58b848be88302ab2bb6c24bf076a694de2b2fa1a8eff53fcaa6800e938bdeee831498fcc72cc9b822dad5b2074d5bc292c766e44c13e000000048000000010000000331fffa94345676f294eceb259baa51107267136af1e829868e1a3c5e2514517bfcfaec78783afde2874c6d2f4cb8436ed421e67fe327e8c67c851da9446ef226000000480000000100000003daff3194609bf5a05c1e6ec1e085854275ee81dbee01c92e2cb357faeba811424b80bd9b204d70675aaf026f2f23bb0e882271bad34ff5294cc05cd7fc0740ac0000004800000001000000034b5b49ca009d1836cfa176112aaf7775fa8c241bd45f861c1eec34dd2b9654e8144c74c1f80c9e0f23cae4503ae85de975f74d250be667a1f6285c9951a8f8c90000004800000001000000032fb4e2dd32d6fdd7e93fe24e23b9762099e1b12f5d9cae6dae7df3401e33931a8af65803c1538716bdba05948c8818f92791010ef8d6d315fb97bccdf2c2fbbf000000480000000100000003b97cd2e80a232dcf417da8ac1b835bf9dab15816bc1e2e0c07214e531ac922ca2f5ddbb26f8d599805feb5f6ae1c6e3fe08ef5cf7dbd60eb407892d6e72a67a30000001c0000000100000003e7d781f18b675dad11f1f49600057e8094628ad00000002800000001000000024ac9c87b674dcd932d2e9d3a4b7c16a3989e750fa3a8895e8dd0971c56fb96780000002c000000010000000200000010cf6ca67cfe59cd5f110c1586de9c2186cfb7213784043ffb017fdf5cfa74ac320000003c000000010000000200000020a03a82bae4627fc74de8c75437e5b077aa3d63e5745f61f47362954b80f53ede6867267605b7383f55e6a80aefcae153000000080000000200000003
参照整理数据后,如下
8 0 0
72 1 0 01001db2ee547837c2b0394f9316a3c672109c854769d9627ce715aa82ae76af4fc7d468903ffa4f7c9d4afcf139528ceb24cb5f64a192287282ee7fd076992f
72 1 0 e73f0a730b98e032e90afaf73b8ddab1e821432c3e1c2c51396914f53fb304f26cbc8f85ec68462ff85dfb0979648d43003291ccb9418e7b4016f5d3325d4083
72 1 0 d44c5aff410f28c841fb51c2e982244d7f7370fb6b73d6e5caba56c1b4b8f96bea190aa8d66e7e37d76fe2e5fef7f78b0de90e12eefda3a36177583412ca074e
72 1 0 96a1796af867e440a72ee81e36e05f3b73c3341f6166b804bf83c3d0b47df74cc77405595ce44d3ccfb739496b8acb78fdb02bcd510851b3e3de015fc06eadb4
10 1 0 0f8e
40 1 0 2accc966ccaf48a147471171fb9589c95c561100d6548ad979f328e43bcfe075
44 1 0 0000001023a5457e1fa2e2f4a23242b1e61a597d1458bee4871e6f44e929682001472830
60 1 0 00000020a6f95ec809bac678aa1f4a74a0094e00d33e42da057331c95a61c6b5c3cd24daefeb367e01d3765e91643e37e2ac95e9
72 1 0 0000020044f4cf64a905e470a2d8091e5320c0b8a370193fe44728340c454361c84578f3b469963d12fa608ab96bf2e8c9c2116010d50e151b6407308d3cb6a2
72 1 0 bc02026a76b5be1d66cf03d90ea5303a5091b48d370ac186402138606da35c90fe7efb0a21f0a177896f496ba40f02e079b82218be0124ab7de5d4f48cfd921e
72 1 0 323d2847d03880fa5cb48533939141115c3dc15fa32a82be59d78826e3d37f5cac12010ce10c850df63626f94657a5beacf7d502b59fc10f571959ce6101b8d6
72 1 0 704e541c930ca3a8d156d7f6122fda7bbdffed9b9bc6160f4ec8ace48978bd458869a636a7d8798d7dbd503e0c41aad82496578df4fbffbd3c5c885dc0bd3dee
72 1 0 6d6af1efc82365f1619286e7a612155d87038f4ccb39e25e0660f9f2d320ae4321996b69187ba68abdf3e6ab41abfa2dd359c7eaa5d344fc1acb97b58dd44d86
72 1 0 d444d17c165ee78e1d55f5c42b1f1bcf9c0f302588b68d26d2a308250c42d1df13be07693aa0f42cefcb9dc1688216478a1a041c9a0c66308b3e4a5135fd2f0f
72 1 0 2c7d9df81c7c9ccb7422089f94c0fa54067e6c4fc634c725c9aa9710aaedd671f72cf9287f38de6111ace6c0c32ed568569b45743abfc519e23aabccdf30a9af
72 1 0 d1bbcab1224daf8ccfb5e6dbf42ee924935b990eee7abe70ac5537426236e0ff1b2ac4748c665d3aba61c4685798ae62126d89220cd5ae8c6a7c32e33ce1236d
28 1 0 b802088e5e303c8389880c09c3925053cc210825
8 2 0
8 0 1
72 1 1 0100320b119809b793abf357a7f78b0742ee93a957e563a5a94fdb09804e89596f2597a2cb9ae9f5161d5fda88ff050e47b1d28bebc6563465d2e7959e8a624a
72 1 1 cd39b2053c17021f93030e3b9bc7149ff5423faf64693932f76a8dbffa526fff7c076845b1d31967efca0b56b066e8bacedc1927e629c6d0e87f61bf14ee3039
72 1 1 053d668ef1855426257ce68cdbc2f66919a2f9efbcb632daa6170cb8246ab7a2348032f48cefdbc3aadcee6b9ab867371346bbe90fd69d213705ed1de38922b3
72 1 1 45bbbf8e0b10c5436e5974f46426d3efdbeaba819ea5d049bb420219a426336e14bc36e5753cb71fb21a2b78f699918a0045a8badddd69646ed65a59e17feec8
10 1 1 b30c
40 1 1 503fdd267309866142ae96b3197515b72ccd766dedbc09d61c25f0c3fa79ebd4
44 1 1 00000010bd688bc8657972730f1d9a5c340cd555602957fa44cf643423bb23734bf8490b
60 1 1 00000020184ff5940c47e4fc42a2bd1f61b304f5fdfc5e453104a3946d06c4897a86f7d2872c948ff06b270b4d024446df8b60fa
72 1 1 000001d06fe6d3c4b7761ffea3dea5ca1b75305f3bd828925e041baabc00aa51f93e5d59aa6c5c024e1de93ccabbcc7736271de03665a2b170a42faca2e86998
72 1 1 6c6b50fecd4e0e1a9ca070fafa04c06a12f27af94d5430ccce129ada67c3040d444b772758195366025267bfea9e35cbaaf816022b34755d5ac2a4d7df857732
72 1 1 ede0bf60b0ca23f40635dcbda76eaf3b59faa140dee0b2480aacd8df765ba5cfd1347f22c9415006210eb4f224332b5cfcac7be98e0da94f74693d8af22e1fad
72 1 1 0614feada5c2aa494e61a0b2a848b82833860d6c1213c4aceebcbe55f419403ecd843835f14f2caa8310be6bfad7ad2054df500a54268b17530183ef4c49f1c5
72 1 1 1ed33f223e632356012a42484c1241d41ec5426ba94c0c4887a8206b86b41ac73ca8b79d90256d391190bcb2256e881642c5a0fbc178691cf9ec983e1f1db400
72 1 1 2c5043530d28ce81e89c0a71baeb821ff0240d18fbac0e01b0952bb62b91354597b9061dc440318ce3eabd95742607546c414ebf3da32879b2af3500d08cb4e9
72 1 1 b404a5293b85aadaa3d595d38992c219ddd7a4e5f00c09af477eea99477b3d53ac6b67c49f0cbd5a7ff038904dfc1a3b58cabe2c25dcb86fa55a53f3d362f051
44 1 1 28bf591667dcd1d600abe1db48f49b17a5ad9d5650f7793af7a24341b771a9247f1eb480
8 2 1
8 0 2
72 1 2 0100d92f41b75bb8ced6be2fbbc0ba1cfeeebdf15826ce92ba78ef4cd0f6d47ff04e9e593cfc5fc7eac8109effce7e75f547873ab559186885edf0e519f73aed
72 1 2 43421e08dea79fd12889b2845ca365803bb4aa23c50d0c298e6649121b6d9101f32d15a043ffdbc93e7665617fa7b4b3f01db76f5472c5aa3a085da5683efcc4
72 1 2 bf9a240df9afc3596d4b3613ae9a2184340561c896a60cc577e6ca507b5e6548ccfcd8bccf27de73deaaf04fab707a20c6aa94febdf8a0a5532c0f4c73958e11
72 1 2 fc1437567ccd886b5496cabb117993f31afe25f53d92721877892e472bf8bba1743b827e277f500d51b7f74f4682e943be0d3ebfdc30742e211dc3eba51dac8b
10 1 2 9074
40 1 2 4ac9c87b674dcd932d2e9d3a4b7c16a3989e750fa3a8895e8dd0971c56fb9678
44 1 2 00000010cf6ca67cfe59cd5f110c1586de9c2186cfb7213784043ffb017fdf5cfa74ac32
60 1 2 00000020a03a82bae4627fc74de8c75437e5b077aa3d63e5745f61f47362954b80f53ede6867267605b7383f55e6a80aefcae153
8 0 3
72 1 3 0100abcf924576de63087c8695ccda3705e8670c770f2bfda1dafdeddcd09b2aa6d485c6a87ff31c14300ddb660576ceed52047318a30d3c05c9848b0a1fb053
72 1 3 87d378e9cbb8914e496a633595c7f68da097afd4fbd0380b4eafe790ffe999b81ceeff32eea4d8fa4279606c7c491ec4eb4a7ef5bf614307c21bd3a314db9d2e
72 1 3 e9f505f08c464e1f5f123bcc180305bb5a30f2c382493a1cc6d6e5e189e75950f75c8a790aef2c1fae18436c9d6f4840a9eacbf04139a2b25042c27f3a3fd756
72 1 3 faeaff92d731e354d03dc46cbe8a001188dde35e753c259de359181678d94e47d90709345f6c9975288dbecfe1a6cf2eb7a14978854bbc73d3ac7d0a72cc3ef4
10 1 3 c41a
40 1 3 e836256016a5f8ca1e29732b7332d9776bdc6694a9df6c1172183f65916f83d5
44 1 3 00000010f46cbf6896be858f5c2f86ee3c162359c545b1f5bd1eec0cd03e2b7bf9c1b4b9
60 1 3 00000020c580aa8aad81a2800fadf74749e79c323da65a6d11e8fb517d60ba36a0113b345be7c0fce390fba664776b676d82fdbe
72 1 3 000002002292a593b68fdbf615d43c123747cf1f1583619708368b471b4a37c8eed21e07d14a7bf309f45335592134c5cc7a18152de20bb7d2fb753bee9131d9
72 1 3 3076a9d57efa379e4f7f4700116d786c586b49523454dd9b3ae7cfde0416d9bfbb486eed31f88fec8128cd1e0bf783c8978c04fde5f1bbe67ecbe1c76e0596f5
72 1 3 579bbdb311093c2a3bb58b848be88302ab2bb6c24bf076a694de2b2fa1a8eff53fcaa6800e938bdeee831498fcc72cc9b822dad5b2074d5bc292c766e44c13e0
72 1 3 31fffa94345676f294eceb259baa51107267136af1e829868e1a3c5e2514517bfcfaec78783afde2874c6d2f4cb8436ed421e67fe327e8c67c851da9446ef226
72 1 3 daff3194609bf5a05c1e6ec1e085854275ee81dbee01c92e2cb357faeba811424b80bd9b204d70675aaf026f2f23bb0e882271bad34ff5294cc05cd7fc0740ac
72 1 3 4b5b49ca009d1836cfa176112aaf7775fa8c241bd45f861c1eec34dd2b9654e8144c74c1f80c9e0f23cae4503ae85de975f74d250be667a1f6285c9951a8f8c9
72 1 3 2fb4e2dd32d6fdd7e93fe24e23b9762099e1b12f5d9cae6dae7df3401e33931a8af65803c1538716bdba05948c8818f92791010ef8d6d315fb97bccdf2c2fbbf
72 1 3 b97cd2e80a232dcf417da8ac1b835bf9dab15816bc1e2e0c07214e531ac922ca2f5ddbb26f8d599805feb5f6ae1c6e3fe08ef5cf7dbd60eb407892d6e72a67a3
28 1 3 e7d781f18b675dad11f1f49600057e8094628ad0
8 2 3
最后整理一下思路,程序主要逻辑是
从主函数分析得到最开始在server与client建立连接时server端随机数生成了16字节的密钥,然后将它与publickey公钥进行加密,加密后将数据发送给server,同时也读取server端加密数据使用client端私钥解密以后将解密数据与最开始16字节加密后生成的新数据进行异或操作,得到新的密钥来进行了SHA-256,然后server与client间会进行密钥校验过程。如果校验正确,那么最后会将数据进行AES-CBC的模式解密。
如果我们要得到真正的正确发送的数据,那么我们需要获得server端生成的随机数